General audience texts
Besides the scholarly publications listed below, I have written many texts in English and German. My more notable German texts appeared by DNIP.ch. I also maintain document collections intended for a broad audience:
Scholarly publications
Up-to-date citation counts (provided by Google Scholar). List of patents granted.
2019
Robert Müller; Corinna Schmitt; Daniel Kaiser; Marcel Waldvogel
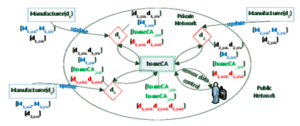
HomeCA: Scalable Secure IoT Network Integration Proceedings Article
In: Stumme, David; Geihs; Lange; (Ed.): INFORMATIK 2019, pp. 167-180, Gesellschaft für Informatik, 2019.
Abstract | BibTeX | Tags: Internet of Things, Security, Wireless | Links:
@inproceedings{mueller2019homeca,
title = {HomeCA: Scalable Secure IoT Network Integration},
author = {Robert Müller; Corinna Schmitt; Daniel Kaiser; Marcel Waldvogel},
editor = {David; Geihs; Lange; Stumme},
url = {https://netfuture.ch/wp-content/uploads/2019/09/mueller2019homeca.pdf},
year = {2019},
date = {2019-09-25},
urldate = {1000-01-01},
booktitle = {INFORMATIK 2019},
journal = {INFORMATIK 2019},
volume = {P-294},
pages = {167-180},
publisher = {Gesellschaft für Informatik},
series = {LNI},
abstract = {Integrating Internet of Things (IoT) devices into an existing network is a nightmare. Minimalistic, unfriendly user interfaces, if any; badly chosen security methods, most notably the defaults; lack of long term security; and bugs or misconfigurations are plentiful. As a result, an increasing number of owners operate unsecure devices.
Our investigations into the root causes of the problems resulted in the development of Home Certificate Authority (HomeCA). HomeCA includes a comprehensive set of secure, vendor-independent interoperable practices based on existing protocols and open standards. HomeCA avoids most of the current pitfalls in network integration by design. Long-term protocol security, permission management, and secure usage combined with simplified device integration and secure key updates on ownership acquisition pave the way toward scalable, federated IoT security.},
keywords = {Internet of Things, Security, Wireless},
pubstate = {published},
tppubtype = {inproceedings}
}
Our investigations into the root causes of the problems resulted in the development of Home Certificate Authority (HomeCA). HomeCA includes a comprehensive set of secure, vendor-independent interoperable practices based on existing protocols and open standards. HomeCA avoids most of the current pitfalls in network integration by design. Long-term protocol security, permission management, and secure usage combined with simplified device integration and secure key updates on ownership acquisition pave the way toward scalable, federated IoT security.
2018
Sandra Domenique Ringmann; Hanno Langweg; Marcel Waldvogel
Requirements for legally compliant software based on the GDPR Proceedings Article
In: Cloud and Trusted Computing 2018 (C&TC 2018), 2018.
Abstract | BibTeX | Tags: Cloud Computing, Data Protection, GDPR, Privacy | Links:
@inproceedings{Ringmann2018Requirements,
title = {Requirements for legally compliant software based on the GDPR},
author = {Sandra Domenique Ringmann and Hanno Langweg and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2018/10/ringmann2018requirements.pdf},
year = {2018},
date = {2018-10-22},
urldate = {1000-01-01},
booktitle = {Cloud and Trusted Computing 2018 (C&TC 2018)},
abstract = {We identify 74 generic, reusable technical requirements based on the GDPR that can be applied to software products which process personal data. The requirements can be traced to corresponding articles and recitals of the GDPR and fulfil the key principles of lawfulness and transparency. Therefore, we present an approach to requirements engineering with regard to developing legally compliant software that satisfies the principles of privacy by design, privacy by default as well as security by design.},
keywords = {Cloud Computing, Data Protection, GDPR, Privacy},
pubstate = {published},
tppubtype = {inproceedings}
}
Marcel Waldvogel; Thomas Zink
Einfache Zwei-Faktor-Authentisierung Journal Article
In: Digma, vol. 2018, no. 3, 2018, ISSN: 2270000414598.
Abstract | BibTeX | Tags: Passwords, Security, Two-Factor Authentication, Usability | Links:
@article{Waldvogel2018Einfache-2FA,
title = {Einfache Zwei-Faktor-Authentisierung},
author = {Marcel Waldvogel and Thomas Zink},
url = {https://netfuture.ch/wp-content/uploads/2018/09/einfache-zwei-faktor-authentisierung.pdf},
issn = {2270000414598},
year = {2018},
date = {2018-09-30},
urldate = {1000-01-01},
journal = {Digma},
volume = {2018},
number = {3},
abstract = {Der Trend zu Kundennähe und architektonischen Offenheit in Firmen und Behörden führt zu zusätzlichen Herausforderungen bei Datenschutz und -sicherheit. Viel zu häufig fehlen Know-How, Quellcode oder Ressourcen, um die betroffenen Anwendungen an die neuen Sicherheitsanforderungen anzupassen. Wir zeigen auf, wie gerade in diesen Fällen eine Zwei-Faktor-Authentisierung mittels X.509-Zertifikaten eine schnell umsetzbare, einfache, komfortable und trotzdem starke und erweiterbare Sicherheitskomponente sein kann, z.T. ohne Eingriff in die Anwendung.},
keywords = {Passwords, Security, Two-Factor Authentication, Usability},
pubstate = {published},
tppubtype = {article}
}

Matthias Held; Marcel Waldvogel
Fighting Ransomware with Guided Undo Proceedings Article
In: Proceedings of NISK 2018, 2018.
Abstract | BibTeX | Tags: Cloud Storage, Intrusion Detection, Ransomware, Replication, Security, Usability, Web Applications | Links:
@inproceedings{Held2018FightingRansomware,
title = {Fighting Ransomware with Guided Undo},
author = {Matthias Held and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2018/07/held2018fightingransomware.pdf
https://netfuture.ch/wp-content/uploads/2018/09/ransomware_detection.pdf
https://netfuture.ch/wp-content/uploads/2018/09/2018-ransomware.odp},
year = {2018},
date = {2018-09-18},
urldate = {1000-01-01},
booktitle = {Proceedings of NISK 2018},
abstract = {Ransomware attacks are rare, yet catastrophic. On closer inspection, they differ from other malware infections: Given appropriate preparation, they do not need to be caught on first sight, but can be undone later. However, current ransomware protection follows the beaten path of anti-malware copying their fallacies. We show how the move to personal cloud storage allows for a paradigm shift in ransomware protection: exceptional attack isolation, perfect elimination of false positive alerts, and simplified recovery.
In this paper, we analyze the necessary operations for ransomware, extend existing ransomware taxonomy, and verify them against real-world malware samples. We analyze the costs and benefits of moving ransomware detection to versioned personal cloud storage. Our content, meta data, and behavior analysis paired with a `guilt by association' capability greatly improve the false positive rate, but the guided undo make this rate all but inconsequential. Even though the user now carries a new burden, it comes with clear responsibilities and benefits, while being freed from questionable duties, resulting in a win-win situation for user experience and detection quality.
},
keywords = {Cloud Storage, Intrusion Detection, Ransomware, Replication, Security, Usability, Web Applications},
pubstate = {published},
tppubtype = {inproceedings}
}
In this paper, we analyze the necessary operations for ransomware, extend existing ransomware taxonomy, and verify them against real-world malware samples. We analyze the costs and benefits of moving ransomware detection to versioned personal cloud storage. Our content, meta data, and behavior analysis paired with a `guilt by association’ capability greatly improve the false positive rate, but the guided undo make this rate all but inconsequential. Even though the user now carries a new burden, it comes with clear responsibilities and benefits, while being freed from questionable duties, resulting in a win-win situation for user experience and detection quality.
Marianne Jossen; Ursula Uttinger; Marcel Waldvogel
Datenschutz und IT in der Arztpraxis: ein Fass mit Boden Journal Article
In: Schweizerische Ärztezeitung, vol. 99, no. 21, pp. 647-648, 2018.
Abstract | BibTeX | Tags: Data Protection, Medical Data | Links:
@article{Jossen2018Datenschutz,
title = {Datenschutz und IT in der Arztpraxis: ein Fass mit Boden},
author = {Marianne Jossen and Ursula Uttinger and Marcel Waldvogel},
url = {https://saez.ch/article/doi/saez.2018.06639},
doi = {https://doi.org/10.4414/saez.2018.06639},
year = {2018},
date = {2018-05-23},
urldate = {2018-05-23},
journal = {Schweizerische Ärztezeitung},
volume = {99},
number = {21},
pages = {647-648},
abstract = {Für Ärztinnen, Ärzte, MPA, Praxismanagerinnen und Praxismanager ist der sorgfältige Umgang mit den ihnen anvertrauten Patientendaten ein wichtiges Element ihres Alltags. Doch was genau muss eine Praxis dabei berücksichtigen?},
keywords = {Data Protection, Medical Data},
pubstate = {published},
tppubtype = {article}
}

Marcel Waldvogel
Meltdown und Spectre: Lesen ohne zu lesen Journal Article
In: Computerworld, 2018.
Abstract | BibTeX | Tags: Security | Links:
@article{Waldvogel-Meltdown,
title = {Meltdown und Spectre: Lesen ohne zu lesen},
author = {Marcel Waldvogel},
url = {https://www.computerworld.ch/security/hardware/meltdown-spectre-lesen-zu-lesen-1461525.html},
year = {2018},
date = {2018-01-17},
urldate = {1000-01-01},
journal = {Computerworld},
abstract = {Was Meltdown und Spectre mit einem Schachspiel zu tun haben und worum es bei den Sicherheitslücken aus technischer Sicht geht. Ein Informatikprofessor erklärt.},
keywords = {Security},
pubstate = {published},
tppubtype = {article}
}

2017
Robert Müller; Marcel Waldvogel; Corinna Schmitt
MoDeNA: Enhancing User Security for Devices in Wireless Personal and Local Area Networks Proceedings Article
In: Proceedings of AIMS 2017, 2017.
Abstract | BibTeX | Tags: Internet of Things, Mobile Networks, Security, Usability | Links:
@inproceedings{Müller2017MoDeNA-AIMS,
title = {MoDeNA: Enhancing User Security for Devices in Wireless Personal and Local Area Networks},
author = {Robert Müller and Marcel Waldvogel and Corinna Schmitt},
url = {https://netfuture.ch/wp-content/uploads/2017/07/mueller2017modena.pdf
https://netfuture.ch/wp-content/uploads/2017/07/modena_presentation_aims_2017_07_12.pdf},
year = {2017},
date = {2017-07-10},
urldate = {1000-01-01},
booktitle = {Proceedings of AIMS 2017},
abstract = {Today most used devices are connected with each other building the Internet of Things (IoT). A variety of protocols are used depending on the underlying network infrastructure, application (e.g., Smart City, eHealth), and device capability. The judgment of the security feeling of the data sharing depends on personal settings (e.g., easy to use, encrypted transmission, anonymization support). MoDeNA – a Mobile Device Network Assistant – was developed offering an opportunity for understanding the judgment of security by bringing the user’s concerns and their technology understanding of used devices and protocols into relation. MoDeNA provides a transparent overview over the used wireless security of the user’s device giving concrete advices for improving the connection security and usability of mobile device security.},
keywords = {Internet of Things, Mobile Networks, Security, Usability},
pubstate = {published},
tppubtype = {inproceedings}
}
Ursula Uttinger; Marcel Waldvogel
FAQ Datenschutz und Informationstechnologie in der medizinischen Praxis Booklet
Bern, Switzerland, 2017.
Abstract | BibTeX | Tags: Data Protection, Medical Data, Security | Links:
@booklet{uttinger2017datenschutz,
title = {FAQ Datenschutz und Informationstechnologie in der medizinischen Praxis},
author = {Ursula Uttinger and Marcel Waldvogel},
editor = {EQUAM Stiftung},
url = {https://netfuture.ch/wp-content/uploads/2017/11/faq-datenschutz-und-it_verzeichnis.pdf},
year = {2017},
date = {2017-06-01},
urldate = {1000-01-01},
address = {Bern, Switzerland},
abstract = {Für Ärztinnen, Ärzte, MPA, Praxismanager und -managerinnen ist der sorgfältige Umgang mit den ihnen anvertrauten Patientendaten ein wichtiges Anliegen. Doch wie kann man diese Daten schützen?
Die rechtliche Lage ist oftmals nur schwer durchschaubar. Rechtstexte behandeln das Thema auf einer übergeordneten Ebene und sind nicht einfach zu interpretieren. Zudem wirft die zunehmende Digitalisierung der Arztpraxen viele Fragen auf. Patientendaten müssen inmitten eines rasanten technologischen Wandels bestmöglichst geschützt werden.
Diese Wegleitung soll Ihnen eine praxisbezogene Handreichung für den Umgang mit medizinischen und anderen Patientendaten in Ihrer Praxis sein.},
month = {06},
keywords = {Data Protection, Medical Data, Security},
pubstate = {published},
tppubtype = {booklet}
}
Die rechtliche Lage ist oftmals nur schwer durchschaubar. Rechtstexte behandeln das Thema auf einer übergeordneten Ebene und sind nicht einfach zu interpretieren. Zudem wirft die zunehmende Digitalisierung der Arztpraxen viele Fragen auf. Patientendaten müssen inmitten eines rasanten technologischen Wandels bestmöglichst geschützt werden.
Diese Wegleitung soll Ihnen eine praxisbezogene Handreichung für den Umgang mit medizinischen und anderen Patientendaten in Ihrer Praxis sein.
Marcel Waldvogel; Thomas Zink
X.509 User Certificate-based Two-Factor Authentication for Web Applications Proceedings Article
In: Müller, Paul; Neumair, Bernhard; Reiser, Helmut; Dreo Rodosek, Gabi (Ed.): 10. DFN-Forum Kommunikationstechnologien, 2017.
Abstract | BibTeX | Tags: Federated Services, Identity Management, Passwords, Security, Usability, Web Applications, X.509 | Links:
@inproceedings{Waldvogel-X509,
title = {X.509 User Certificate-based Two-Factor Authentication for Web Applications},
author = {Marcel Waldvogel and Thomas Zink},
editor = {Paul Müller and Bernhard Neumair and Helmut Reiser and Dreo Rodosek, Gabi},
url = {https://netfuture.ch/wp-content/uploads/2018/05/x509auth.pdf
},
year = {2017},
date = {2017-05-30},
urldate = {1000-01-01},
booktitle = {10. DFN-Forum Kommunikationstechnologien},
abstract = {An appealing property to researchers, educators, and students is the openness of the physical environment and IT infrastructure of their organizations. However, to the IT administration, this creates challenges way beyond those of a single-purpose business or administration. Especially the personally identifiable information or the power of the critical functions behind these logins, such as financial transactions or manipulating user accounts, require extra protection in the heterogeneous educational environment with single-sign-on. However, most web-based environments still lack a reasonable second-factor protection or at least the enforcement of it for privileged operations without hindering normal usage.
In this paper we introduce a novel and surprisingly simple yet extremely flexible way to implement two-factor authentication based on X.509 user certificates in web applications. Our solution requires only a few lines of code in web server configuration and none in the application source code for basic protection. Furthermore, since it is based on X.509 certificates, it can be easily combined with smartcards or USB cryptotokens to further enhance security.},
keywords = {Federated Services, Identity Management, Passwords, Security, Usability, Web Applications, X.509},
pubstate = {published},
tppubtype = {inproceedings}
}
In this paper we introduce a novel and surprisingly simple yet extremely flexible way to implement two-factor authentication based on X.509 user certificates in web applications. Our solution requires only a few lines of code in web server configuration and none in the application source code for basic protection. Furthermore, since it is based on X.509 certificates, it can be easily combined with smartcards or USB cryptotokens to further enhance security.
Marcel Waldvogel
Weg vom Internet der (unsicheren) Dinge Journal Article
In: PC-Tipp, 2017.
Abstract | BibTeX | Tags: Public, Security | Links:
@article{Waldvogel2017Weg,
title = {Weg vom Internet der (unsicheren) Dinge},
author = {Marcel Waldvogel},
url = {http://www.pctipp.ch/tipps-tricks/kummerkasten/sicherheit/artikel/weg-vom-internet-der-unsicheren-dinge-87430/},
year = {2017},
date = {2017-03-30},
urldate = {1000-01-01},
journal = {PC-Tipp},
abstract = {Immer mehr Dinge des Alltags sind mit dem Internet verbunden und dementsprechend auch darüber steuerbar: Das Internet der Dinge ist überall. Damit es nicht uns beherrscht, sondern wir es beherrschen können, finden Sie hier einige Tipps.},
keywords = {Public, Security},
pubstate = {published},
tppubtype = {article}
}
Franziska Ackermann; Petra Enderle; Matthias Fratz; Volodymyr Kushnarenko; Daniel Scharon; Pia Schmücker; Marcel Waldvogel; Stefan Wesner
SARA-Service: Langzeitverfügbarkeit und Publikation von Softwareartefakten Miscellaneous
Poster, eScience-Tage 2017, 2017.
Abstract | BibTeX | Tags: Archiving, git, Research Data Management, Software | Links:
@misc{SARA2017,
title = {SARA-Service: Langzeitverfügbarkeit und Publikation von Softwareartefakten},
author = {Franziska Ackermann and Petra Enderle and Matthias Fratz and Volodymyr Kushnarenko and Daniel Scharon and Pia Schmücker and Marcel Waldvogel and Stefan Wesner},
url = {https://netfuture.ch/wp-content/uploads/2017/03/2017_03_esciencetage_hd.pdf},
year = {2017},
date = {2017-03-17},
urldate = {1000-01-01},
abstract = {Das Projekt SARA (Software Archiving of Research Artefacts) hat das Ziel, einen neuen wissenschaftlichen Dienst zu entwickeln, mit dem Softwareartefakte langfristig verfügbar gemacht und publiziert werden können. Der Schwerpunkt liegt besonders auf den Softwarewerkzeugen, mit deren Hilfe Forschungsdaten verarbeitet und ausgewertet werden. In der Fachdisziplin Biologie werden beispielsweise Messdaten computergestützt erfasst und weiterverarbeitet. In der Elektrotechnik und Informatik müssen kontinuierlich die unterschiedlichen Versionsstände der entwickelten Software gespeichert werden, um den Fortschritt der Entwicklung zu dokumentieren.
Der Dienst soll die Workflows der Forschenden begleiten und sie anregen, Zwischenstände ihrer Forschungsarbeit auch bei Softwarewerkzeugen bereits prozessbegleitend festzuhalten. Damit kann auf die gesamte Entstehungshistorie der oft von den Forschenden selbst entwickelten oder modifizierten Werkzeuge zurückgegriffen werden. Die erhobenen Forschungsdaten sind zusammen mit den jeweiligen Versionsständen der dazugehörigen Softwarewerkzeuge für die weiterführende Forschung nachvollziehbar. Der im Projekt prototypisch für Informatik / Elektrotechnik und Biologie entwickelte Dienst soll nach Ablauf der Evaluierungsphase grundsätzlich allen Fachdisziplinen zur Verfügung stehen.},
howpublished = {Poster, eScience-Tage 2017},
keywords = {Archiving, git, Research Data Management, Software},
pubstate = {published},
tppubtype = {misc}
}
Der Dienst soll die Workflows der Forschenden begleiten und sie anregen, Zwischenstände ihrer Forschungsarbeit auch bei Softwarewerkzeugen bereits prozessbegleitend festzuhalten. Damit kann auf die gesamte Entstehungshistorie der oft von den Forschenden selbst entwickelten oder modifizierten Werkzeuge zurückgegriffen werden. Die erhobenen Forschungsdaten sind zusammen mit den jeweiligen Versionsständen der dazugehörigen Softwarewerkzeuge für die weiterführende Forschung nachvollziehbar. Der im Projekt prototypisch für Informatik / Elektrotechnik und Biologie entwickelte Dienst soll nach Ablauf der Evaluierungsphase grundsätzlich allen Fachdisziplinen zur Verfügung stehen.

Thomas Zink; Marcel Waldvogel
X.509 User Certificate-based Two-Factor Authentication for Web Applications Technical Report
Distributed Systems Laboratory, University of Konstanz no. KN-2017-DISY-03, 2017.
Abstract | BibTeX | Tags: Certificates, Identity Management, Security, Two-Factor Authentication, Usability, Web Applications, X509 | Links:
@techreport{Zink2017X509,
title = {X.509 User Certificate-based Two-Factor Authentication for Web Applications},
author = {Thomas Zink and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2017/03/kn-2017-disy-03.pdf},
year = {2017},
date = {2017-03-14},
urldate = {1000-01-01},
number = {KN-2017-DISY-03},
institution = {Distributed Systems Laboratory, University of Konstanz},
abstract = {An appealing property to researchers, educators, and students is the openness
of the physical environment and IT infrastructure of their organizations. How-
ever, to the IT administration, this creates challenges way beyond those of a
single-purpose business or administration. Especially the personally identifiable
information or the power of the critical functions behind these logins, such as
financial transactions or manipulating user accounts, require extra protection in
the heterogeneous educational environment with single-sign-on. However, most
web-based environments still lack a reasonable second-factor protection or at
least the enforcement of it for privileged operations without hindering normal
usage.
In this paper we introduce a novel and surprisingly simple yet extremely flex-
ible way to implement two-factor authentication based on X.509 user certificates
in web applications. Our solution requires only a few lines of code in web server
configuration and none in the application source code for basic protection. Fur-
thermore, since it is based on X.509 certificates, it can be easily combined with
smartcards or USB cryptotokens to further enhance security.},
keywords = {Certificates, Identity Management, Security, Two-Factor Authentication, Usability, Web Applications, X509},
pubstate = {published},
tppubtype = {techreport}
}
of the physical environment and IT infrastructure of their organizations. How-
ever, to the IT administration, this creates challenges way beyond those of a
single-purpose business or administration. Especially the personally identifiable
information or the power of the critical functions behind these logins, such as
financial transactions or manipulating user accounts, require extra protection in
the heterogeneous educational environment with single-sign-on. However, most
web-based environments still lack a reasonable second-factor protection or at
least the enforcement of it for privileged operations without hindering normal
usage.
In this paper we introduce a novel and surprisingly simple yet extremely flex-
ible way to implement two-factor authentication based on X.509 user certificates
in web applications. Our solution requires only a few lines of code in web server
configuration and none in the application source code for basic protection. Fur-
thermore, since it is based on X.509 certificates, it can be easily combined with
smartcards or USB cryptotokens to further enhance security.
Robert Müller; Marcel Waldvogel; Corinna Schmitt
MoDeNA: Enhancing User Security for Devices in Wireless Personal and Local Area Networks Technical Report
Distributed Systems Laboratory, University of Konstanz no. KN-2017-DISY-02, 2017.
Abstract | BibTeX | Tags: Internet of Things, Security, Usability, Wireless, WPAN | Links:
@techreport{Mueller2017MoDeNA,
title = {MoDeNA: Enhancing User Security for Devices in Wireless Personal and Local Area Networks},
author = {Robert Müller and Marcel Waldvogel and Corinna Schmitt},
url = {https://netfuture.ch/wp-content/uploads/2017/03/kn-2017-disy-02.pdf},
year = {2017},
date = {2017-03-13},
urldate = {1000-01-01},
number = {KN-2017-DISY-02},
institution = {Distributed Systems Laboratory, University of Konstanz},
abstract = {Today most used devices are connected with each other building the Internet
of Things (IoT). They communicate with each other directly and share data with
a plethora of other devices indirectly by using the underlying network infrastruc-
ture. In both cases a variety of protocols are used depending on infrastructure,
application (e.g., Smart City, eHealth), and device capability. But the overall
concept of the data sharing is to do it in a secure manner so that different users
(e.g., consumer, facilities, provider) can gain benefits. But what does “secure
manner” means? This is a big question between the stakeholders, especially when
talking of wireless personal and local area networks (WPANs) and wireless local
area networks (WLAN), because the judgment of the security feeling depends
on personal settings (e.g., easy to use, encrypted transmission, anonymization
support). Therefore, MoDeNA – a Mobile Device Network Assistant – was de-
veloped offering an opportunity for understanding the judgment of security by
bringing the user’s concerns and their technology understanding of used devices
and protocols into relation. MoDeNA provides a transparent overview over the
used wireless security of the user’s device giving concrete advices for improving
the connection security, helping to improve usability of mobile device security. As
a use-case the smart city environment is used, because this is the most common
area, where many different WPAN and WLAN connections exist, supported by
different underlying infrastructures, and where secure data transmission is es-
sential, because it is an “open communication area”.},
keywords = {Internet of Things, Security, Usability, Wireless, WPAN},
pubstate = {published},
tppubtype = {techreport}
}
of Things (IoT). They communicate with each other directly and share data with
a plethora of other devices indirectly by using the underlying network infrastruc-
ture. In both cases a variety of protocols are used depending on infrastructure,
application (e.g., Smart City, eHealth), and device capability. But the overall
concept of the data sharing is to do it in a secure manner so that different users
(e.g., consumer, facilities, provider) can gain benefits. But what does “secure
manner” means? This is a big question between the stakeholders, especially when
talking of wireless personal and local area networks (WPANs) and wireless local
area networks (WLAN), because the judgment of the security feeling depends
on personal settings (e.g., easy to use, encrypted transmission, anonymization
support). Therefore, MoDeNA – a Mobile Device Network Assistant – was de-
veloped offering an opportunity for understanding the judgment of security by
bringing the user’s concerns and their technology understanding of used devices
and protocols into relation. MoDeNA provides a transparent overview over the
used wireless security of the user’s device giving concrete advices for improving
the connection security, helping to improve usability of mobile device security. As
a use-case the smart city environment is used, because this is the most common
area, where many different WPAN and WLAN connections exist, supported by
different underlying infrastructures, and where secure data transmission is es-
sential, because it is an “open communication area”.
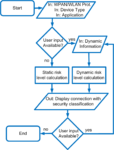
Robert Müller; Marcel Waldvogel; Daniel Kaiser
HomeCA: Scalable Secure IoT Network Integration Technical Report
Distributed Systems Laboratory, University of Konstanz no. KN-2017-DISY-01, 2017.
Abstract | BibTeX | Tags: Internet of Things, Security, Trust | Links:
@techreport{Mueller2017HomeCA,
title = {HomeCA: Scalable Secure IoT Network Integration},
author = {Robert Müller and Marcel Waldvogel and Daniel Kaiser},
url = {https://netfuture.ch/wp-content/uploads/2017/03/kn-2017-disy-01.pdf},
year = {2017},
date = {2017-03-12},
urldate = {1000-01-01},
number = {KN-2017-DISY-01},
institution = {Distributed Systems Laboratory, University of Konstanz},
abstract = {The sheer number of devices in the Internet of Things (IoT) makes efficient
device integration into a user’s home or corporate network a nightmare. More and
more owners lose control over their devices, often due to badly chosen security
defaults, software bugs, or broken protocols. The lack of user interface and the
long period of device usage increase the plight. We identify several root causes,
resulting in HomeCA, a comprehensive set of secure, vendor-neutral practices
based on existing protocols and open standards. These practices avoid most of
the common pitfalls, allow long-term permission management and secure usage,
and include support for automatic device integration. We also present a protocol
for ensuring secure key updates when acquiring device ownership.},
keywords = {Internet of Things, Security, Trust},
pubstate = {published},
tppubtype = {techreport}
}
device integration into a user’s home or corporate network a nightmare. More and
more owners lose control over their devices, often due to badly chosen security
defaults, software bugs, or broken protocols. The lack of user interface and the
long period of device usage increase the plight. We identify several root causes,
resulting in HomeCA, a comprehensive set of secure, vendor-neutral practices
based on existing protocols and open standards. These practices avoid most of
the common pitfalls, allow long-term permission management and secure usage,
and include support for automatic device integration. We also present a protocol
for ensuring secure key updates when acquiring device ownership.

2016
Daniel Kaiser; Marcel Waldvogel; Holger Strittmatter; Oliver Haase
User-Friendly, Versatile, and Efficient Multi-Link DNS Service Discovery Proceedings Article
In: Proceedings of the 1st Workshop on Edge Computing (WEC 2016); in conjunction with IEEE ICDCS 2016, 2016.
Abstract | BibTeX | Tags: DNS-SD, Multicast, Service Discovery, Zeroconf | Links:
@inproceedings{kaiser2016user-friendly,
title = {User-Friendly, Versatile, and Efficient Multi-Link DNS Service Discovery},
author = {Daniel Kaiser and Marcel Waldvogel and Holger Strittmatter and Oliver Haase
},
url = {https://netfuture.ch/wp-content/uploads/2016/06/kaiser2016user-friendly.pdf},
year = {2016},
date = {2016-06-27},
urldate = {1000-01-01},
booktitle = {Proceedings of the 1st Workshop on Edge Computing (WEC 2016); in conjunction with IEEE ICDCS 2016},
abstract = {When mobile devices at the network edge want to communicate with each other, they too often depend on the availability of faraway resources. Feasible user-friendly service discovery is essential for direct communication. DNS Service Discovery over Multicast DNS (DNS-SD/mDNS) is widely used for configurationless service discovery in local networks; due in no small part to the fact that it is based on the well established DNS, and efficient in small networks.
In our research, we enhance DNS-SD/mDNS providing versatility, user control, efficiency, and privacy, while maintaining the deployment simplicity and backward compatibility. These enhancements are necessary to make it a solid, flexible foundation for device communication in the edge of the Internet.
In this paper, we focus on providing multi-link capabilities and scalable scopes for DNS-SD while being mindful of both user-friendliness and efficiency. We propose DNS-SD over Stateless DNS (DNS-SD/sDNS), a solution that allows configurationless service discovery in arbitrary self-named scopes – largely independent of the physical network layout – by leveraging our Stateless DNS technique and the Raft consensus algorithm.},
keywords = {DNS-SD, Multicast, Service Discovery, Zeroconf},
pubstate = {published},
tppubtype = {inproceedings}
}
In our research, we enhance DNS-SD/mDNS providing versatility, user control, efficiency, and privacy, while maintaining the deployment simplicity and backward compatibility. These enhancements are necessary to make it a solid, flexible foundation for device communication in the edge of the Internet.
In this paper, we focus on providing multi-link capabilities and scalable scopes for DNS-SD while being mindful of both user-friendliness and efficiency. We propose DNS-SD over Stateless DNS (DNS-SD/sDNS), a solution that allows configurationless service discovery in arbitrary self-named scopes – largely independent of the physical network layout – by leveraging our Stateless DNS technique and the Raft consensus algorithm.
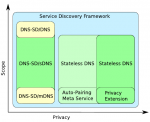
2015
Andreas Rain; Daniel Kaiser; Marcel Waldvogel
Realistic, Extensible DNS and mDNS Models for INET/OMNeT++ Proceedings Article
In: Proceedings of the “OMNeT++ Community Summit 2015â€, 2015.
Abstract | BibTeX | Tags: DNS-SD, Mobile Networks, Multicast, Service Discovery, Simulation, Zeroconf | Links:
@inproceedings{rain2015realistic,
title = {Realistic, Extensible DNS and mDNS Models for INET/OMNeT++},
author = {Andreas Rain and Daniel Kaiser and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2016/06/rain2015realistic.pdf
https://netfuture.ch/wp-content/uploads/2016/06/rain2015realistic-slides.pdf},
year = {2015},
date = {2015-09-03},
urldate = {1000-01-01},
booktitle = {Proceedings of the “OMNeT++ Community Summit 2015â€},
abstract = {The domain name system (DNS) is one of the core services in today’s network structures. In local and ad-hoc networks DNS is often enhanced or replaced by mDNS. As of yet, no simulation models for DNS and mDNS have been developed for INET/OMNeT++. We introduce DNS and mDNS simulation models for OMNeT++, which allow researchers to easily prototype and evaluate extensions for these protocols. In addition, we present models for our own experimental extensions, namely Stateless DNS and Privacy-Enhanced mDNS, that are based on the aforementioned models. Using our models we were able to further improve the efficiency of our protocol extensions.},
keywords = {DNS-SD, Mobile Networks, Multicast, Service Discovery, Simulation, Zeroconf},
pubstate = {published},
tppubtype = {inproceedings}
}
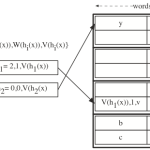
Thomas Zink; Marcel Waldvogel
Efficient hash tables for network applications Journal Article
In: SpringerPlus, vol. 4, no. 222, pp. 1-19, 2015.
Abstract | BibTeX | Tags: Fast Routers, Hash Tables | Links:
@article{Zink2015EHT,
title = {Efficient hash tables for network applications},
author = {Thomas Zink and Marcel Waldvogel},
editor = {Springer},
url = {https://netfuture.ch/wp-content/uploads/2015/05/zink2015eht.pdf},
doi = {10.1186/s40064-015-0958-y},
year = {2015},
date = {2015-05-15},
urldate = {1000-01-01},
journal = {SpringerPlus},
volume = {4},
number = {222},
pages = {1-19},
abstract = {Hashing has yet to be widely accepted as a component of hard real-time systems and hardware implementations, due to still existing prejudices concerning the unpredictability of space and time requirements resulting from collisions. While in theory perfect hashing can provide optimal mapping, in practice, finding a perfect hash function is too expensive, especially in the context of high-speed applications.
The introduction of hashing with multiple choices, d-left hashing and probabilistic table summaries, has caused a shift towards deterministic DRAM access. However, high amounts of rare and expensive high-speed SRAM need to be traded off for predictability, which is infeasible for many applications.
In this paper we show that previous suggestions suffer from the false precondition of full generality. Our approach exploits four individual degrees of freedom available in many practical applications, especially hardware and high-speed lookups. This reduces the requirement of on-chip memory up to an order of magnitude and guarantees constant lookup and update time at the cost of only minute amounts of additional hardware. Our design makes efficient hash table implementations cheaper, more predictable, and more practical.},
keywords = {Fast Routers, Hash Tables},
pubstate = {published},
tppubtype = {article}
}
The introduction of hashing with multiple choices, d-left hashing and probabilistic table summaries, has caused a shift towards deterministic DRAM access. However, high amounts of rare and expensive high-speed SRAM need to be traded off for predictability, which is infeasible for many applications.
In this paper we show that previous suggestions suffer from the false precondition of full generality. Our approach exploits four individual degrees of freedom available in many practical applications, especially hardware and high-speed lookups. This reduces the requirement of on-chip memory up to an order of magnitude and guarantees constant lookup and update time at the cost of only minute amounts of additional hardware. Our design makes efficient hash table implementations cheaper, more predictable, and more practical.
Daniel Kaiser; Andreas Rain; Marcel Waldvogel; Holger Strittmatter
A Multicast-Avoiding Privacy Extension for the Avahi Zeroconf Daemon Proceedings Article
In: NetSys 2015, Gesellschaft für Informatik, 2015.
Abstract | BibTeX | Tags: DNS-SD, Privacy, Security, Zeroconf | Links:
@inproceedings{Kaiser2015Multicast-avoiding,
title = {A Multicast-Avoiding Privacy Extension for the Avahi Zeroconf Daemon},
author = {Daniel Kaiser and Andreas Rain and Marcel Waldvogel and Holger Strittmatter},
url = {https://netfuture.ch/wp-content/uploads/2014/12/kaiser2015multicast-avoiding.pdf
https://netfuture.ch/wp-content/uploads/2015/03/mdns-security-poster.pdf},
year = {2015},
date = {2015-03-10},
urldate = {1000-01-01},
booktitle = {NetSys 2015},
publisher = {Gesellschaft für Informatik},
abstract = {In today’s local networks, a significant amount of traffic is caused by Multicast packets, such as Multicast DNS Service Discovery (mDNS-SD), a widespread technique used for configurationless service distribution and discovery. It suffers from two major problems inherent in multicast: privacy and network load. We present a privacy extension for the Avahi Zeroconf Daemon that tackles both problems while being very efficient.},
keywords = {DNS-SD, Privacy, Security, Zeroconf},
pubstate = {published},
tppubtype = {inproceedings}
}
Klaus Herberth; Daniel Scharon; Matthias Fratz; Marcel Waldvogel
JSXC: Adding Encrypted Chat with 3 Lines of Code Proceedings Article
In: NetSys 2015, Gesellschaft für Informatik, 2015.
Abstract | BibTeX | Tags: Security, XMPP | Links:
@inproceedings{Herberth2015JSXC,
title = {JSXC: Adding Encrypted Chat with 3 Lines of Code},
author = {Klaus Herberth and Daniel Scharon and Matthias Fratz and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2014/12/herberth2015jsxc.pdf
https://netfuture.ch/wp-content/uploads/2015/02/jsxc-poster.pdf},
year = {2015},
date = {2015-03-10},
urldate = {1000-01-01},
booktitle = {NetSys 2015},
publisher = {Gesellschaft für Informatik},
abstract = {If it is not in the web, it does not exist. However, most of our current arsenal of web services are provided for free by large international corporations – free as in targeted advertising. More privacy-aware self-hosted alternatives frequently lack the feature set of their commercial rivals, leaving users to decide between privacy and functionality. Therefore, we present WISEchat (Web-Integrated Secure Enhanced Chat), our concept for enhancing practical security for web-based chat, as well as an implementation, the JavaScript XMPP Client (JSXC). By design, JSXC can be easily and painlessly integrated into existing web apps to equip them with encrypted chat capabilities, making them more attractive and thus more frequently providing a secure alternative as the most functional and convenient alternative.},
keywords = {Security, XMPP},
pubstate = {published},
tppubtype = {inproceedings}
}
Marcel Waldvogel; Thomas Zink
Boost DNS Privacy, Reliability, and Efficiency with opDNS Safe Query Elimination Proceedings Article
In: NetSys 2015, Gesellschaft für Informatik, 2015.
Abstract | BibTeX | Tags: DNS, Privacy, Security | Links:
@inproceedings{Waldvogel2015Boost,
title = {Boost DNS Privacy, Reliability, and Efficiency with opDNS Safe Query Elimination},
author = {Marcel Waldvogel and Thomas Zink},
url = {https://netfuture.ch/wp-content/uploads/2014/12/waldvogel2015boost.pdf
https://netfuture.ch/wp-content/uploads/2015/03/opdns-poster.pdf},
year = {2015},
date = {2015-03-10},
urldate = {1000-01-01},
booktitle = {NetSys 2015},
publisher = {Gesellschaft für Informatik},
abstract = {SRV records, DNSSEC, and DANE among others fortify the Domain Name System as the central information hub behind the Internet. Largely hidden from the end user, an increasing number of protocol and trust decisions are contingent on DNS. Neglect or attacks on DNS have much more impact today than ever, now endangering security far beyond denial of service. Opportunistic Persistent DNS (opDNS) addresses these problems by abandoning pessimistic caching and eliminating unnecessary traffic. Today’s DNS infrastructure relies on the hosts forgetting and refreshing DNS records in relatively short time. In conjunction with TLS, opDNS greatly reduces the number of queries and in turn increases privacy, reliability, and efficiency. Even with DNS lookups all but eliminated for frequently visited secure services, changes to the server addresses will be recognized almost immediately, unlike standard DNS. We will show how end systems can take advantage of opDNS without having to wait for support by server operators or application developers, enabling the most effective way of deployment.},
keywords = {DNS, Privacy, Security},
pubstate = {published},
tppubtype = {inproceedings}
}

2014
Daniel Kaiser; Matthias Fratz; Marcel Waldvogel; Valentin Dietrich; Holger Strittmatter
Stateless DNS Technical Report
University of Konstanz Technical Report, no. KN-2014-DISY-004, 2014.
Abstract | BibTeX | Tags: DNS-SD, Multicast, Peer-to-Peer, Privacy, Zeroconf | Links:
@techreport{Kaiser2014Stateless,
title = {Stateless DNS},
author = {Daniel Kaiser and Matthias Fratz and Marcel Waldvogel and Valentin Dietrich and Holger Strittmatter},
url = {https://netfuture.ch/wp-content/uploads/2015/02/kaiser14stateless.pdf},
year = {2014},
date = {2014-12-31},
urldate = {1000-01-01},
number = {KN-2014-DISY-004},
institution = {University of Konstanz},
abstract = {Several network applications, like service discovery, file discovery in P2P networks, distributed hash tables, and distributed caches, use or would benefit from distributed key value stores. The Domain Name System (DNS) is a key value store which has a huge infrastructure and is accessible from almost everywhere.
Nevertheless storing information in this database makes it necessary to be authoritative for a domain or to be “registered” with a domain, e.g. via DynDNS, to be allowed to store and update resource records using
nsupdate. Applications like the ones listed above would greatly benefit from a configurationless approach, giving users a much more convenient experience.
In this report we describe a technique we call Stateless DNS, which allows to store data in the cache of the local DNS server. It works without any infrastructure updates; it just needs our very simple, configurationless echo DNS server that can parse special queries containing information desired to be stored, process this information, and generate DNS answers in a way that the DNS cache that was asked the special query will store the desired information. Because all this happens in the authority zone of our echo DNS server, we do not cause cache poisoning. Our tests show that Stateless DNS works with a huge number of public DNS servers.},
type = {Technical Report},
keywords = {DNS-SD, Multicast, Peer-to-Peer, Privacy, Zeroconf},
pubstate = {published},
tppubtype = {techreport}
}
Nevertheless storing information in this database makes it necessary to be authoritative for a domain or to be “registered” with a domain, e.g. via DynDNS, to be allowed to store and update resource records using
nsupdate. Applications like the ones listed above would greatly benefit from a configurationless approach, giving users a much more convenient experience.
In this report we describe a technique we call Stateless DNS, which allows to store data in the cache of the local DNS server. It works without any infrastructure updates; it just needs our very simple, configurationless echo DNS server that can parse special queries containing information desired to be stored, process this information, and generate DNS answers in a way that the DNS cache that was asked the special query will store the desired information. Because all this happens in the authority zone of our echo DNS server, we do not cause cache poisoning. Our tests show that Stateless DNS works with a huge number of public DNS servers.
Marcel Waldvogel; Jürgen Kollek
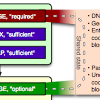
SIEGE: Service-Independent Enterprise-GradE protection against password scans Journal Article
In: DFN-Mitteilungen, no. 87, pp. 40–46, 2014, ISSN: 0177-6894.
Abstract | BibTeX | Tags: Federated Services, Intrusion Detection, Security | Links:
@article{Waldvogel2014SIEGE-DFN,
title = {SIEGE: Service-Independent Enterprise-GradE protection against password scans},
author = {Marcel Waldvogel and Jürgen Kollek},
editor = {Kai Hoelzner},
url = {https://netfuture.ch/wp-content/uploads/2014/12/SIEGE-DFN.pdf
https://www.dfn.de/fileadmin/5Presse/DFNMitteilungen/DFN_Mitteilungen_87.pdf},
issn = {0177-6894},
year = {2014},
date = {2014-11-30},
urldate = {1000-01-01},
journal = {DFN-Mitteilungen},
number = {87},
pages = {40--46},
abstract = {Security is one of the main challenges today, complicated significantly by the heterogeneous and open academic networks with thousands of different applications. Botnet-based brute-force password scans are a common security threat against the open academic networks. Common de- fenses are hard to maintain, error-prone and do not reliably discriminate between user error and coordinated attack. In this paper, we present a novel approach, which allows to secure many net- work services at once. By combining in-app tracking, local and global crowdsourcing, geographic information, and probabilistic user-bot distinction through differential password analysis, our PAM-based detection module can provide higher accuracy and faster blocking of botnets. In the future, we aim to make the mechanism even more generic and thus provide a distributed defense for our infrastructure against one of the strongest threats.},
keywords = {Federated Services, Intrusion Detection, Security},
pubstate = {published},
tppubtype = {article}
}
Thomas Zink; Oliver Haase; Marcel Waldvogel
Webharvesting von Publikationsdaten Technical Report
University of Konstanz no. KN-2014-DISY-02, 2014.
Abstract | BibTeX | Tags: Web Applications, Web Archiving | Links:
@techreport{Zink2014Webharvesting,
title = {Webharvesting von Publikationsdaten},
author = {Thomas Zink and Oliver Haase and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2018/09/zink2014webharvesting.pdf},
year = {2014},
date = {2014-10-01},
urldate = {1000-01-01},
number = {KN-2014-DISY-02},
institution = {University of Konstanz},
abstract = {Forschungsarbeiten, -daten und -resultate an Universitäten und Hochschulen werden immer häufiger nicht mehr als Schriftstück, sondern exklusiv auf Webseiten im Internet und Intranet veröffentlicht und dokumentiert. Diese werden bisher nur ungenügend und unvollständig archiviert. Dadurch entstehen potentiell große Lücken in der Archivierung und künftigen Dokumentation. Zudem beeinträchtigt dies die Nachvollziehbarkeit und Reproduzierbarkeit, beides Eigenschaften, die besonders im wissenschaftlichen Kontext einen hohen Stellwert haben.},
keywords = {Web Applications, Web Archiving},
pubstate = {published},
tppubtype = {techreport}
}
Thomas Zink; Oliver Haase; Marcel Waldvogel
Automatische Identifikation relevanter Domains zur Web-Archivierung Technical Report
University of Konstanz no. KN-2014-DISY-01, 2014.
Abstract | BibTeX | Tags: Web Applications, Web Archiving | Links:
@techreport{Zink2014AutomatischeDomains,
title = {Automatische Identifikation relevanter Domains zur Web-Archivierung},
author = {Thomas Zink and Oliver Haase and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2018/09/zink2014automatischedomains.pdf},
year = {2014},
date = {2014-10-01},
urldate = {1000-01-01},
number = {KN-2014-DISY-01},
institution = {University of Konstanz},
abstract = {Oftmals werden Organisationen und Forschungseinrichtungen wie Hochschulen und Universitäten durch viele verschiedene Domains repräsentiert, die auf mehreren Webservern gehostet werden. Dem Anwender sind diese oftmals nicht gänzlich bekannt, da Arbeitsgruppen, Institute, etc. ihre eigenen Domains und Webserver – unter Umständen auch extern gehostet – haben können. Für die Web-Archivierung in großen Organisationen stellt dies ein Problem dar, da a priori nicht bekannt ist, welche Domains archiviert werden müssen. Diese sollten automatisch erkannt werden. Das Hauptproblem dabei besteht darin, eine Zugehörigkeit von Domains zur Organisation festzustellen. Wir stellen verschiedene Verfahren vor, die vor und während des Harvestens angewand werden können, um dynamisch zu entscheiden, welche Domains dem Archiv hinzugefügt werden müssen.},
keywords = {Web Applications, Web Archiving},
pubstate = {published},
tppubtype = {techreport}
}
Daniel Kaiser; Marcel Waldvogel
Adding Privacy to Multicast DNS Service Discovery Proceedings Article
In: Proceedings of IEEE TrustCom 2014 (IEEE EFINS 2014 workshop), 2014.
Abstract | BibTeX | Tags: DNS-SD, Multicast, Peer-to-Peer, Privacy, Service Discovery, Social Networks, Trust, Zeroconf | Links:
@inproceedings{Kaiser2014Adding,
title = {Adding Privacy to Multicast DNS Service Discovery},
author = {Daniel Kaiser and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2014/08/Kaiser2014Adding.pdf},
year = {2014},
date = {2014-09-24},
urldate = {1000-01-01},
booktitle = {Proceedings of IEEE TrustCom 2014 (IEEE EFINS 2014 workshop)},
abstract = {Multicast DNS Service Discovery (mDNS-SD), made fashionable through Apple’s \emph{Bonjour}, is a prevalent technique allowing service distribution and discovery in local networks without configuration (Zeroconf). Possible application areas are device synchronization, instant messaging, VoIP, file and screen sharing. It is very convenient for users, because they can connect to and offer services when they enter a network without any manual configuration. However, it requires the public exposure of the offering and requesting identities along with information about the offered and requested services, even when services do not need to be public. Some of the information published by the announcements can be very revealing, including complete lists of family members. In this paper we discuss the privacy problems arising when using mDNS-SD and present our privacy extension, which allows hiding all information published while still not requiring any network configuration except for an initial pairing. A key feature of our solution is the ease of upgrading existing systems, a must for widespread deployment and acceptance. To show the feasibility of our mDNS-SD privacy extension, we developed an implementation based on the open-source \emph{Avahi} daemon.},
keywords = {DNS-SD, Multicast, Peer-to-Peer, Privacy, Service Discovery, Social Networks, Trust, Zeroconf},
pubstate = {published},
tppubtype = {inproceedings}
}
Daniel Kaiser; Marcel Waldvogel
Efficient Privacy Preserving Multicast DNS Service Discovery Proceedings Article
In: Workshop on Privacy-Preserving Cyberspace Safety and Security (CSS), 2014.
Abstract | BibTeX | Tags: DNS-SD, Multicast, Privacy, Service Discovery, Zeroconf | Links:
@inproceedings{Kaiser2014Efficient,
title = {Efficient Privacy Preserving Multicast DNS Service Discovery},
author = {Daniel Kaiser and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2014/08/Kaiser2014Efficient.pdf},
year = {2014},
date = {2014-08-23},
urldate = {1000-01-01},
booktitle = {Workshop on Privacy-Preserving Cyberspace Safety and Security (CSS)},
abstract = {In today’s local networks a significant amount of traffic is caused by Multicast DNS Service Discovery (mDNS-SD), a prevalent technique used for configurationless service distribution and discovery. It allows users to offer and use services like device synchronization, file sharing, and chat, when joining a local network without any manual configuration. While this is very convenient, it requires the public exposure of the offering and requesting identities along with information about the offered and requested services, even when services do not need to be public. Some of the information published by the announcements can be very revealing, including complete lists of family members. Another problem is the huge amount of multicast traffic caused, which is especially relevant for large WiFi networks.
In this paper we present a privacy extension that does not publish private information and reduces the number of packets sent while still not requiring any network configuration except for an initial pairing per pair of users. A key feature of our solution is the ease of upgrading existing systems, a must for widespread deployment and acceptance. We developed an implementation based on the open-source Avahi daemon to show the feasibility of our privacy extension. Our solution grants tunable privacy and reduces multicast traffic without affecting user experience.},
keywords = {DNS-SD, Multicast, Privacy, Service Discovery, Zeroconf},
pubstate = {published},
tppubtype = {inproceedings}
}
In this paper we present a privacy extension that does not publish private information and reduces the number of packets sent while still not requiring any network configuration except for an initial pairing per pair of users. A key feature of our solution is the ease of upgrading existing systems, a must for widespread deployment and acceptance. We developed an implementation based on the open-source Avahi daemon to show the feasibility of our privacy extension. Our solution grants tunable privacy and reduces multicast traffic without affecting user experience.
Muhammad Arshad Islam; Marcel Waldvogel
Analysis of Cognitive Radio Enabled Flooding in Opportunistic Networks Journal Article
In: International Journal of Communications, Network and System Sciences, vol. 7, pp. 212-222, 2014.
Abstract | BibTeX | Tags: Mobile Networks, Opportunistic Networks | Links:
@article{islam2014cognitive,
title = {Analysis of Cognitive Radio Enabled Flooding in Opportunistic Networks},
author = {Muhammad Arshad Islam and Marcel Waldvogel},
editor = {Scientific Research},
url = {https://netfuture.ch/wp-content/uploads/2015/06/islam2014cognitive.pdf},
doi = {http://dx.doi.org/10.4236/ijcns.2014.77023},
year = {2014},
date = {2014-07-01},
urldate = {1000-01-01},
journal = {International Journal of Communications, Network and System Sciences},
volume = {7},
pages = {212-222},
abstract = {Epidemic routing (Flooding) is considered as a simple routing protocol for opportunistic networks where the participants attempt to transmit whatever information they have to everyone who does not already have that information. However, it is plagued with disadvantages of resource scarcity as it exerts stress on available bandwidth as well as storage capacity of the devices in the network. Cognitive radio (CR) is one of the emerging technologies that can improve the bandwidth utilization by smart allocation of spectrum radio bands. Ideally speaking, a spectrum-aware cognitive radio is able to sense the local spectrum usage and adapt its own radio parameters accordingly. In this study, we have performed experiments to analyze the gains achieved by flooding protocol using cognitive radios of varying capabilities in opportunistic networks. We have performed expe- riments on three opportunistic networks obtained from real-life traces from different environments and presented results showing variance in delivery efficiency as well as cost incurred on those scenarios. Our results show that performance of flooding can be significantly improved using CRs in bandwidth-scarce environments; however, the improvement is not uniform with the increase in a number of available bands.},
keywords = {Mobile Networks, Opportunistic Networks},
pubstate = {published},
tppubtype = {article}
}
Marcel Waldvogel; Jürgen Kollek
SIEGE: Service-Independent Enterprise-GradE protection against password scans Proceedings Article
In: Müller, Paul; Neumair, Bernhard; Reiser, Helmut; Dreo Rodosek, Gabi (Ed.): 7. DFN-Forum Kommunikationstechnologien — Beiträge der Fachtagung, Gesellschaft für Informatik, 2014.
Abstract | BibTeX | Tags: Federated Services, Identity Management, Intrusion Detection, Passwords, Peer, Security | Links:
@inproceedings{Waldvogel2014SIEGE,
title = {SIEGE: Service-Independent Enterprise-GradE protection against password scans},
author = {Marcel Waldvogel and Jürgen Kollek},
editor = {Paul Müller and Bernhard Neumair and
Helmut Reiser and Dreo Rodosek, Gabi},
url = {https://netfuture.ch/wp-content/uploads/2014/08/Waldvogel2014SIEGE.pdf
https://netfuture.ch/wp-content/uploads/2014/08/Waldvogel2014SIEGE-slides.pdf},
year = {2014},
date = {2014-06-16},
urldate = {1000-01-01},
booktitle = {7. DFN-Forum Kommunikationstechnologien -- Beiträge der Fachtagung},
publisher = {Gesellschaft für Informatik},
series = {Lecture Notes in Informatics},
abstract = {Security is one of the main challenges today, complicated significantly by the heterogeneous and open academic networks with thousands of different applications. Botnet-based brute-force password scans are a common security threat against the open academic networks. Common defenses are hard to maintain, error-prone and do not reliably discriminate between user error and coordinated attack. In this paper, we present a novel approach, which allows to secure many network services at once. By combining in-app tracking, local and global crowdsourcing, geographic information, and probabilistic user-bot distinction through differential password analysis, our PAM-based detection module can provide higher accuracy and faster blocking of botnets. In the future, we aim to make the mechanism even more generic and thus provide a distributed defense against one of the strongest threats against our infrastructure.},
keywords = {Federated Services, Identity Management, Intrusion Detection, Passwords, Peer, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
Marcel Waldvogel; Klaus Herberth; Daniel Scharon
Chat in Forschung und Lehre? Sicher! Journal Article
In: DFN-Mitteilungen, no. 86, pp. 38-41, 2014, ISSN: 0177-6894.
Abstract | BibTeX | Tags: Federated Services, Privacy, Security, Social Networks, Video Chat, Web Applications, XMPP | Links:
@article{Waldvogel2014Chat,
title = {Chat in Forschung und Lehre? Sicher!},
author = {Marcel Waldvogel and Klaus Herberth and Daniel Scharon},
url = {https://netfuture.ch/wp-content/uploads/2014/05/Waldvogel2014Chat.pdf
https://www.dfn.de/publikationen/dfnmitteilungen/},
issn = {0177-6894},
year = {2014},
date = {2014-05-23},
urldate = {1000-01-01},
journal = {DFN-Mitteilungen},
number = {86},
pages = {38-41},
abstract = {Instant Messaging, Audio- und Videoanrufe, kurz Chat, ist aus unserem täglichen Leben nicht mehr wegzudenken. Die meisten nutzen dafür geschlossene Systeme, die für den Privatgebrauch bequem sind, für den dienstlichen Einsatz in Forschung und Lehre aber an Datenschutz und Privatsphäre scheitern. Das muss nicht so sein: Auf Basis des offenen, föderierten Extensible Messaging and Presence Protocols (XMPP) bietet WISEchat webbasiert und -integriert die Sicherheit, den Komfort und die Erweiterbarkeit, die eine moderne Hochschule braucht. Die Hintergründe, Vorteile und Zukunftssicherheit erläutern wir anhand einiger konkreter Beispiele.},
keywords = {Federated Services, Privacy, Security, Social Networks, Video Chat, Web Applications, XMPP},
pubstate = {published},
tppubtype = {article}
}

Klaus Herberth; Daniel Kaiser; Daniel Scharon; Marcel Waldvogel
Interaktive Webseiten für effiziente Kooperation auf Basis offener Standards Technical Report
University of Konstanz no. KN-2014-DiSy-002, 2014.
Abstract | BibTeX | Tags: Collaboration, Privacy, Security, Social Networks, Video Chat, Web Applications, XMPP | Links:
@techreport{herberth14interaktive,
title = {Interaktive Webseiten für effiziente Kooperation auf Basis offener Standards},
author = {Klaus Herberth and Daniel Kaiser and Daniel Scharon and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2014/01/herberth14interaktive.pdf},
year = {2014},
date = {2014-01-18},
urldate = {1000-01-01},
number = {KN-2014-DiSy-002},
institution = {University of Konstanz},
abstract = {Homepages von Forschern, Informationsseiten der Verwaltung, Support- und Beratungsseiten, Webmail oder sonstige Groupware begleiten uns bei der täglichen Arbeit im akademischen Umfeld. Unmittelbare Rückfragen zu den Inhalten oder Interaktionen sind jedoch weiterhin nicht möglich; eine Integration von Direktkontakten wäre häufig angenehm und hilfreich. Swoosch, unsere Javascript-Bibliothek auf Basis der offenen Standards XMPP, HTML5 und WebRTC, bietet hier Abhilfe. Auf einfachste Weise lassen sich so bestehende Webseiten und -anwendungen transparent um Funktionen für Instant Messaging inklusive Videokonferenz erweitern und neue Beratungs- und Kommunikationskanäle eröffnen, bei denen die Privatsphäre durch Ende-zu-Ende-Verschlüsselung gesichert ist. Die Erfahrungen in den Testinstallationen zeigten nahtlose Integration, niedrige Eintrittsschwelle, Geschwindigkeit und Benutzerfreundlichkeit. Durch die inhärente Föderation von XMPP ist der Dienst auch über die Organisationsgrenzen hinaus einsetzbar. Dank seiner offenen Standards ist Swoosch beinahe beliebig integrier- und erweiterbar.},
keywords = {Collaboration, Privacy, Security, Social Networks, Video Chat, Web Applications, XMPP},
pubstate = {published},
tppubtype = {techreport}
}
Marcel Waldvogel; Jürgen Kollek
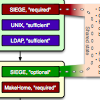
SIEGE: Service-Independent Enterprise-GradE protection against password scans Technical Report
University of Konstanz no. KN-2014-DiSy-001, 2014.
Abstract | BibTeX | Tags: Denial of Service, Intrusion Detection, Peer-to-Peer, Security, Trust | Links:
@techreport{waldvogel4siege,
title = {SIEGE: Service-Independent Enterprise-GradE protection against password scans},
author = {Marcel Waldvogel and Jürgen Kollek},
url = {https://netfuture.ch/wp-content/uploads/2014/01/waldvogel14siege.pdf},
year = {2014},
date = {2014-01-17},
urldate = {1000-01-01},
number = {KN-2014-DiSy-001},
institution = {University of Konstanz},
abstract = {Security is one of the main challenges today, complicated significantly by the heterogeneous and open academic networks with thousands of different applications. Botnet-based brute-force password scans are common security threat against the open academic networks. Common defenses are hard to maintain, error-prone and do not reliably discriminate between user error and coordinated attack. In this paper, we present a novel approach, which allows to secure many network services at once. By combining in-app tracking, local and global crowdsourcing, geographic information, and probabilistic user-bot distinction through differential password analysis, our PAM-based detection module can provide higher accuracy and faster blocking of bot- nets. In the future, we aim to make the mechanism even more generic and thus provide a distributed defense against one of the strongest threats against our infrastructure.},
keywords = {Denial of Service, Intrusion Detection, Peer-to-Peer, Security, Trust},
pubstate = {published},
tppubtype = {techreport}
}
2013
Sebastian Graf; Wolfgang Miller; Marcel Waldvogel
Utilizing Photo Sharing Websites for Cloud Storage Backends Technical Report
University of Konstanz, Distributed Systems Laboratory no. KN-2013-DiSy-02, 2013.
Abstract | BibTeX | Tags: Cloud Storage | Links:
@techreport{Graf2013PhotoSharing,
title = {Utilizing Photo Sharing Websites for Cloud Storage Backends},
author = {Sebastian Graf and Wolfgang Miller and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2013/03/graf13photo-sharing.pdf},
year = {2013},
date = {2013-08-14},
urldate = {1000-01-01},
number = {KN-2013-DiSy-02},
institution = {University of Konstanz, Distributed Systems Laboratory},
abstract = {Cloud Storages combine high availability with the unencessity to maintain any own infrastructure and all-time availability. A wide field of different providers offer a flexible portfolio for any technical need and financial possibility. Yet, the possibilities of different cloud storage providers have all one issue in common: Basic storage is cheap whereas the costs increase with the storage consumed adhering the pay-as-you-go paradigm. Photo sharing websites such as Facebook, Picasa-Web, and Flickr leverage from own cloud infrastructure and offer unlimited storage for less or no charge. Obviously pictures can be used to store information in, which has been used for steganography and watermarking at low data rates. We propose a general framework for storing large amounts of data, its data density and error-correcting mechanisms tunable to the properties of the photo sharing website of your choice. Our cost-performance-analysis shows that photo sharing websites compare favorably to professional cloud storage services such as Amazon S3. Thanks to the integration of our software as a backend to the widely-used jClouds framework, everyone can now use photo sharing websites as one component for low-cost purposes, including archival.},
keywords = {Cloud Storage},
pubstate = {published},
tppubtype = {techreport}
}

Sebastian Graf; Andreas Rain; Daniel Scharon; Marcel Waldvogel
Utilizing Cloud Storages for iSCSI: Is Security really expensive? Technical Report
University of Konstanz, Distributed Systems Laboratory no. KN-2013-DiSy-01, 2013.
Abstract | BibTeX | Tags: Cloud Storage, Security | Links:
@techreport{Graf2013iSCSI,
title = {Utilizing Cloud Storages for iSCSI: Is Security really expensive?},
author = {Sebastian Graf and Andreas Rain and Daniel Scharon and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2013/08/graf13isci.pdf},
year = {2013},
date = {2013-03-03},
urldate = {1000-01-01},
number = {KN-2013-DiSy-01},
institution = {University of Konstanz, Distributed Systems Laboratory},
abstract = {Cloud storage promises unlimited, flexible and cheap storages, including all-time availability and accessibility with the help of various technologies. Free-of-charge offers for endusers allure customers the same way as professional, pay-as-you-go storages do. The delocalization of the data provokes security concerns especially regarding the confidentiality of the data. Even though encryption offers a straight-forward solution to this problem, the performance questions its applicability when it comes to the utilization of professional storage-approaches like iSCSI. In this white-paper, we propose a utilization of NoSQL-based cloud-storages like Amazon S3 or Microsoft Azure for iSCSI. We evaluate the costs of a direct, bucket-based encryption and show, that in complex systems like iSCSI, the distance to the cloud represents the bottleneck instead of the encryption. Performance-boosting techniques like prefetching and caching improve the access and result in no practical overhead within such an utilization. Based on our own developed fully Java-based iSCSI target (jSCSI) and jClouds, our prototype represents, to the best of our knowledge, the first, free available, cloud-deployable iSCSI.},
keywords = {Cloud Storage, Security},
pubstate = {published},
tppubtype = {techreport}
}
2012
Sebastian Graf; Patrick Lang; Stefan A. Hohenadel; Marcel Waldvogel
Versatile Key Management for Secure Cloud Storage Proceedings Article
In: IEEE 31st Symposium on Reliable Distributed Systems, SRDS 2012, pp. 469-474, 2012.
BibTeX | Tags: Cloud Storage, Security | Links:
@inproceedings{Graf2012Versatile,
title = {Versatile Key Management for Secure Cloud Storage},
author = {Sebastian Graf and Patrick Lang and Stefan A. Hohenadel and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2012/graf12versatile.pdf},
year = {2012},
date = {2012-10-08},
urldate = {1000-01-01},
booktitle = {IEEE 31st Symposium on Reliable Distributed Systems, SRDS 2012},
pages = {469-474},
crossref = {DBLP:conf/srds/2012},
keywords = {Cloud Storage, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
Thomas Zink; Marcel Waldvogel
BitTorrent traffic obfuscation: A chase towards semantic traffic identification Proceedings Article
In: 12th IEEE International Conference on Peer-to-Peer Computing, P2P 2012, pp. 126-137, 2012.
Abstract | BibTeX | Tags: Denial of Service, Peer-to-Peer, Security, Traffic Engineering | Links:
@inproceedings{Zink2012BitTorrent,
title = {BitTorrent traffic obfuscation: A chase towards semantic traffic identification},
author = {Thomas Zink and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2012/zink12bittorrent.pdf},
year = {2012},
date = {2012-09-03},
urldate = {1000-01-01},
booktitle = {12th IEEE International Conference on Peer-to-Peer Computing, P2P 2012},
pages = {126-137},
crossref = {DBLP:conf/p2p/2012},
abstract = {With the beginning of the 21st century emerging peer-to-peer networks ushered in a new era of large scale media exchange. Faced with ever increasing volumes of traffic, legal threats by copyright holders, and QoS demands of customers, network service providers are urged to apply traffic classification and shaping techniques. These systems usually are highly integrated to satisfy the harsh restrictions present in network infrastructure. They require constant maintenance and updates. Additionally, they have legal issues and violate both the net neutrality and end-to-end principles. On the other hand, clients see their freedom and privacy attacked. As a result, users, application programmers, and even commercial service providers laboriously strive to hide their interests and circumvent classification techniques. In this user vs. ISP war, the user side has a clear edge. While changing the network infrastructure is by nature very complex, and only slowly reacts to new conditions, updating and distributing software between users is easy and practically instantaneous. In this paper we discuss how state-of-the-art traffic classification systems can be circumvented with little effort. We present a new obfuscation extension to the BitTorrent protocol that allows signature free handshaking. The extension requires no changes to the infrastructure and is fully backwards compatible. With only little change to client software, contemporary classification techniques are rendered ineffective. We argue that future traffic classification must not rely on restricted local syntax information but instead must exploit global communication patterns and protocol semantics in order to be able to keep pace with rapid application and protocol changes.},
keywords = {Denial of Service, Peer-to-Peer, Security, Traffic Engineering},
pubstate = {published},
tppubtype = {inproceedings}
}

Thomas Zink; Oliver Haase; Jürgen Wäsch; Marcel Waldvogel
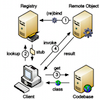
P2P-RMI: Transparent Distribution of Remote Java Objects Journal Article
In: International Journal of Computer Networks & Communications (IJCNC), vol. 4, no. 5, pp. 17-34, 2012.
Abstract | BibTeX | Tags: Java RMI, NAT traversal, Peer-to-Peer, Service Discovery | Links:
@article{Zink2012P2P-RMI,
title = {P2P-RMI: Transparent Distribution of Remote Java Objects},
author = {Thomas Zink and Oliver Haase and Jürgen Wäsch and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2015/02/zink2012p2p-rmi.pdf},
year = {2012},
date = {2012-09-01},
urldate = {1000-01-01},
journal = {International Journal of Computer Networks & Communications (IJCNC)},
volume = {4},
number = {5},
pages = {17-34},
abstract = {Java Remote Method Invocation (RMI) is a built-in and easy-to-use framework for the distribution of remote Java objects. Its simplicity and seamless inter-virtual machine communication has made it a valuable tool for distributed services. It nevertheless exhibits certain constraints that practically limit RMI applications to the classical client/server distribution model, and make highly distributed and highly dynamic systems very difficult to build atop RMI.
We present an approach that makes Java RMI usable for P2P and similar distribution models. The solution basically consists of three ideas: (1) separate the location of the registry from the remote service object, (2) distribute the registry across a DHT infrastructure, and (3) transparently enhance the built-in communication between RMI servers and clients to allow traversal of NAT and firewall boundaries. Our approach is extremely lightweight, transparent, and requires practically zero configuration.},
keywords = {Java RMI, NAT traversal, Peer-to-Peer, Service Discovery},
pubstate = {published},
tppubtype = {article}
}
We present an approach that makes Java RMI usable for P2P and similar distribution models. The solution basically consists of three ideas: (1) separate the location of the registry from the remote service object, (2) distribute the registry across a DHT infrastructure, and (3) transparently enhance the built-in communication between RMI servers and clients to allow traversal of NAT and firewall boundaries. Our approach is extremely lightweight, transparent, and requires practically zero configuration.
Muhammad Arshad Islam; Marcel Waldvogel
Analyzing History Quality for Routing Purposes in Opportunistic Network Using Max-Flow Journal Article
In: Wireless Engineering and Technology, vol. 3, pp. 132-141, 2012.
Abstract | BibTeX | Tags: Opportunistic Networks | Links:
@article{Islam2012Analyzing,
title = {Analyzing History Quality for Routing Purposes in Opportunistic Network Using Max-Flow},
author = {Muhammad Arshad Islam and Marcel Waldvogel},
editor = {Scientific Research},
url = {https://netfuture.ch/wp-content/uploads/2018/10/islam2012analyzing.pdf},
year = {2012},
date = {2012-07-01},
urldate = {1000-01-01},
journal = {Wireless Engineering and Technology},
volume = {3},
pages = {132-141},
abstract = {Most of the existing opportunistic network routing protocols are based on some type of utility function that is directly or indirectly dependent on the past behavior of devices. The past behavior or history of a device is usually referred to as contacts that the device had in the past. Whatever may be the metric of history, most of these routing protocols work on the realistic premise that node mobility is not truly random. In contrast, there are several oracles based methods where such oracles assist these methods to gain access to information that is unrealistic in the real world. Although, such oracles are unrealistic, they can help to understand the nature and behavior of underlying networks. In this paper, we have analyzed the gap between these two extremes. We have performed max-flow computations on three different opportunistic networks and then compared the results by performing max-flow computations on history generated by the respective networks. We have found that the correctness of the history based prediction of history is dependent on the dense nature of the underlying network. Moreover, the history based prediction can deliver correct paths but cannot guarantee their absolute reliability.},
keywords = {Opportunistic Networks},
pubstate = {published},
tppubtype = {article}
}

Michael Simon; Marcel Waldvogel; Sven Schober; Saher Semaan; Martin Nussbaumer
bwIDM: Föderieren auch nicht-webbasierter Dienste auf Basis von SAML Proceedings Article
In: 5. DFN-Forum Kommunikationstechnologien: Verteilte Systeme im Wissenschaftsbereich, pp. 119-128, 2012.
Abstract | BibTeX | Tags: Cloud Storage, Identity Management, Security | Links:
@inproceedings{Simon2012bwIDM,
title = {bwIDM: Föderieren auch nicht-webbasierter Dienste auf Basis von SAML},
author = {Michael Simon and Marcel Waldvogel and Sven Schober and Saher Semaan and Martin Nussbaumer},
url = {https://netfuture.ch/wp-content/uploads/2012/simon12bwidm.pdf},
year = {2012},
date = {2012-05-20},
urldate = {1000-01-01},
booktitle = {5. DFN-Forum Kommunikationstechnologien: Verteilte Systeme im Wissenschaftsbereich},
pages = {119-128},
crossref = {DBLP:conf/dfn/2012},
abstract = {Zur organisationsübergreifenden Nutzung von IT-Diensten werden Dienstföderationen gebildet. Dabei kann das Nutzerkonto der sogenannten Heimateinrichtung auch zum Zugriff auf nicht-lokale Dienste genutzt werden. Während die Integration webbasierter Dienste in Föderationen mit SAML und beispielsweise Shibboleth mittlerweile in vielen Anwendungsbereichen allgegenwärtig ist, fällt die Integration nicht-webbasierter IT-Dienste schwer. Existierende Ansätze, mit denen sich prinzipiell auch nicht-webbasierte Dienste integrieren lassen, erfüllen essentielle Anforderungen nicht und/oder sind nach ihrem heutigen Entwicklungsstand noch nicht betriebsfähig. In diesem Papier werden zwei Verfahren für nicht-webbasierte, föderative Dienstzugriffe (Moonshot und PAM/ECP) evaluiert und notwendige Erweiterungen zur Sicherstellung der Betriebsfa ̈higkeit vorgestellt. Ein implementierter Proof-of-Concept zeigt die Umsetzbarkeit der Lösung.},
keywords = {Cloud Storage, Identity Management, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
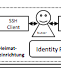
Sebastian Graf; Jörg Eisele; Marcel Waldvogel; Marc Strittmatter
A Legal and Technical Perspective on Secure Cloud Storage Proceedings Article
In: 5. DFN-Forum Kommunikationstechnologien: Verteilte Systeme im Wissenschaftsbereich, pp. 63-72, 2012.
Abstract | BibTeX | Tags: Cloud Storage, Security | Links:
@inproceedings{Graf2012Legal,
title = {A Legal and Technical Perspective on Secure Cloud Storage},
author = {Sebastian Graf and Jörg Eisele and Marcel Waldvogel and Marc Strittmatter},
url = {https://netfuture.ch/wp-content/uploads/2012/graf12legal.pdf},
year = {2012},
date = {2012-05-20},
urldate = {1000-01-01},
booktitle = {5. DFN-Forum Kommunikationstechnologien: Verteilte Systeme im Wissenschaftsbereich},
pages = {63-72},
crossref = {DBLP:conf/dfn/2012},
abstract = {Cloud infrastructures are nowadays an irreplaceable component within modern IT-infrastructures.
Due to their representing abstraction regarding the physical execution framework from the deployment of the service, clouds not offer valuable attributes like scalability, environmental protection by best utilization of hardware resources, pay-as-you-go billing but also problem fields especially when it comes to the storage of confidential data. More concise, secure utilization of common cloud infrastructures like provided by Google, Microsoft or Amazon generate not only an indistinguishable impact to computer science but also to law science. As a consequence, based upon the confidentially of the data and the different methods and parties able to access this information, the safeness of the data must not only be provided by applying technical security measures upon the cloud-stored information but also by the investigation of legal issues going along with the flexibility of the cloud. To fill this gap, our contribution bases upon two pillars:<ul><li>We discuss legal issues going along with the storage of (especially confidential) data on cloud infrastructures provided by third parties.</li><li>Besides the legal issues, we further investigate technical measures how to ensure secure data storage on a technical level utilizing the benefits of cloud infrastructures (namely the scalability and availability).</li></ul>Based upon these investigations, we propose a technical model for secure cloud storage and interpret the measures against common aspects from the area of jurisprudence. Besides, we show that the area of jurisprudence still offers many open issues related to cloud based storage which represent a challenge for end-users as well as complex institutions like universities.},
keywords = {Cloud Storage, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
Due to their representing abstraction regarding the physical execution framework from the deployment of the service, clouds not offer valuable attributes like scalability, environmental protection by best utilization of hardware resources, pay-as-you-go billing but also problem fields especially when it comes to the storage of confidential data. More concise, secure utilization of common cloud infrastructures like provided by Google, Microsoft or Amazon generate not only an indistinguishable impact to computer science but also to law science. As a consequence, based upon the confidentially of the data and the different methods and parties able to access this information, the safeness of the data must not only be provided by applying technical security measures upon the cloud-stored information but also by the investigation of legal issues going along with the flexibility of the cloud. To fill this gap, our contribution bases upon two pillars:
- We discuss legal issues going along with the storage of (especially confidential) data on cloud infrastructures provided by third parties.
- Besides the legal issues, we further investigate technical measures how to ensure secure data storage on a technical level utilizing the benefits of cloud infrastructures (namely the scalability and availability).

Thomas Zink; Marcel Waldvogel
Efficient BitTorrent handshake obfuscation Proceedings Article
In: Proceedings of the First Workshop on P2P and Dependability, ACM, 2012, ISBN: 978-1-4503-1148-9.
Abstract | BibTeX | Tags: Peer-to-Peer, Privacy, Security, Traffic Engineering | Links:
@inproceedings{Zink2012Efficient,
title = {Efficient BitTorrent handshake obfuscation},
author = {Thomas Zink and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2015/02/zink2012efficient.pdf},
isbn = {978-1-4503-1148-9},
year = {2012},
date = {2012-05-08},
urldate = {1000-01-01},
booktitle = {Proceedings of the First Workshop on P2P and Dependability},
publisher = {ACM},
abstract = {During the last decade, large scale media distribution populated peer-to-peer applications. Faced with ever increasing volumes of traffic, legal threats by copyright holders, and QoS demands of customers, network service providers are urged to apply traffic classification and shaping techniques. These highly integrated systems require constant maintenance, introduce legal issues, and violate both the net neutrality and end-to-end principles.
Clients see their freedom and privacy attacked. Users, application programmers, and even commercial service providers laboriously strive to hide their interests and circumvent classification techniques. While changing the network infrastructure is by nature very complex, and it reacts only slowly to new conditions, updating and distributing software between users is easy and practically instantaneous.
We present a new obfuscation extension to the BitTorrent protocol, which allows signature free handshaking. The extension requires no changes to the infrastructure and is fully backwards compatible. With only little change to client software, contemporary classification techniques can be rendered ineffective.},
keywords = {Peer-to-Peer, Privacy, Security, Traffic Engineering},
pubstate = {published},
tppubtype = {inproceedings}
}
Clients see their freedom and privacy attacked. Users, application programmers, and even commercial service providers laboriously strive to hide their interests and circumvent classification techniques. While changing the network infrastructure is by nature very complex, and it reacts only slowly to new conditions, updating and distributing software between users is easy and practically instantaneous.
We present a new obfuscation extension to the BitTorrent protocol, which allows signature free handshaking. The extension requires no changes to the infrastructure and is fully backwards compatible. With only little change to client software, contemporary classification techniques can be rendered ineffective.
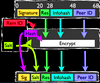
2011
Daniel Maier; Oliver Haase; Jürgen Wäsch; Marcel Waldvogel
A Comparative Analysis of NAT Hole Punching Journal Article
In: HTWG Forum, pp. 40-48, 2011, ISSN: 1619-9812.
BibTeX | Tags: NAT traversal, Peer-to-Peer | Links:
@article{Maier2011Comparative,
title = {A Comparative Analysis of NAT Hole Punching},
author = {Daniel Maier and Oliver Haase and Jürgen Wäsch and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2011/maier11comparative.pdf},
issn = {1619-9812},
year = {2011},
date = {2011-11-01},
urldate = {1000-01-01},
journal = {HTWG Forum},
pages = {40-48},
keywords = {NAT traversal, Peer-to-Peer},
pubstate = {published},
tppubtype = {article}
}
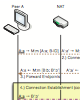
Muhammad Arshad Islam; Marcel Waldvogel
Prediction quality of contact history in opportunistic networks Proceedings Article
In: Wireless Days, 2011.
Abstract | BibTeX | Tags: Opportunistic Networks | Links:
@inproceedings{islam11prediction,
title = {Prediction quality of contact history in opportunistic networks},
author = {Muhammad Arshad Islam and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2013/11/islam11prediction.pdf},
year = {2011},
date = {2011-10-10},
urldate = {1000-01-01},
booktitle = {Wireless Days},
crossref = {DBLP:conf/wd/2011},
abstract = {Routing in opportunistic networks heavily relies on past behavior of the mobile devices it is formed of to predict their future and thus making routing decisions. While almost every protocol relies on this history, its prediction quality has never been studied in a realistic setting. Using extensive simulations on real traces, we are able to describe for the first time how well predictions can be. Unlike oracle-based prediction comparisons, we do not try to predict a contact, but compare the expected user result, namely message delivery probabilities. The analysis also provides guidance on the importance of multi-path routing and the path diversity required, as well as on the impact on forward error correction on the delivery probability. Our results show that the repetitive nature of path is directly proportional to the mobility extent of the devices and, consequently, history obtained from dense opportunistic networks is reliable.},
keywords = {Opportunistic Networks},
pubstate = {published},
tppubtype = {inproceedings}
}
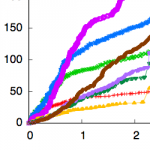
Muhammad Arshad Islam; Marcel Waldvogel
Prediction Quality of Contact History in Opportunistic Networks Proceedings Article
In: IFIP Wireless Days 2011, 2011.
Abstract | BibTeX | Tags: Opportunistic Networks | Links:
@inproceedings{Islam2011Prediction,
title = {Prediction Quality of Contact History in Opportunistic Networks},
author = {Muhammad Arshad Islam and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2018/10/islam2011prediction.pdf},
year = {2011},
date = {2011-10-10},
urldate = {1000-01-01},
booktitle = {IFIP Wireless Days 2011},
abstract = {Routing in opportunistic networks heavily relies on past behavior of the mobile devices it is formed of to predict their future and thus making routing decisions. While almost every protocol relies on this history, its prediction quality has never been studied in a realistic setting. Using extensive simulations on real traces, we are able to describe for the first time how well predictions can be. Unlike oracle-based prediction comparisons, we do not try to predict a contact, but compare the expected user result, namely message delivery probabilities. The analysis also provides guidance on the importance of multi-path routing and the path diversity required, as well as on the impact on forward error correction on the delivery probability. Our results show that the repetitive nature of path is directly proportional to the mobility extent of the devices and, consequently, history obtained from dense opportunistic networks is reliable.},
keywords = {Opportunistic Networks},
pubstate = {published},
tppubtype = {inproceedings}
}

Daniel Maier; Oliver Haase; Jürgen Wäsch; Marcel Waldvogel
NAT Hole Punching Revisited Proceedings Article
In: Proceedings of IEEE LCN 2011, The 36th IEEE Conference on Local Computer Networks, 2011.
Abstract | BibTeX | Tags: NAT traversal, Peer-to-Peer | Links:
@inproceedings{Maier2011NAT,
title = {NAT Hole Punching Revisited},
author = {Daniel Maier and Oliver Haase and Jürgen Wäsch and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2011/maier11nat.pdf},
year = {2011},
date = {2011-10-07},
urldate = {1000-01-01},
booktitle = {Proceedings of IEEE LCN 2011, The 36th IEEE Conference on Local Computer Networks},
abstract = {Setting up connections to hosts behind Network Address Translation (NAT) equipment has last been the subject of research debates half a decade ago when NAT technology was still immature. This paper fills this gap and provides a solid comparison of two essential TCP hole punching approaches: sequential and parallel TCP hole punching. The comparison features current conditions and thoroughly compares setup delay, implementation complexity, resource usage, and effectuality of the two approaches. The result is a list of recommendations and a portable, effectual, and open-source Java implementation.},
keywords = {NAT traversal, Peer-to-Peer},
pubstate = {published},
tppubtype = {inproceedings}
}

Pascal Gienger; Marcel Waldvogel
Polybius: Secure Web Single-Sign-On for Legacy Applications Proceedings Article
In: 4. DFN-Forum Kommunikationstechnologien, 2011.
Abstract | BibTeX | Tags: Cloud Storage, Identity Management, Security, Trust, Web Applications | Links:
@inproceedings{Gienger2011Polybius,
title = {Polybius: Secure Web Single-Sign-On for Legacy Applications},
author = {Pascal Gienger and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2011/gienger11polybius.pdf},
year = {2011},
date = {2011-06-20},
urldate = {1000-01-01},
booktitle = {4. DFN-Forum Kommunikationstechnologien},
abstract = {Web-based interfaces to applications in all domains of university life are surging. Given the diverse demands in and the histories of universities, combined with the rapid IT industry developments, all attempts at a sole all-encompassing platform for single-sign-on (SSO) will remain futile. In this paper, we present an architecture for a meta-SSO, which is able to seamlessly integrate with a wide variety of existing local sign-in and SSO mechanisms. It is therefore an excellent candidate for a university-wide all-purpose SSO system. Among the highlights are: No passwords are ever stored on disk, neither in the browser nor in the gateway; its basics have been implemented in a simple, yet versatile Apache module; and it can help reducing the impact of security problems anywhere in the system. It could even form the basis for secure inter-university collaborations and mutual outsourcing.},
keywords = {Cloud Storage, Identity Management, Security, Trust, Web Applications},
pubstate = {published},
tppubtype = {inproceedings}
}
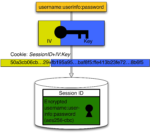
Sebastian Graf; Vyacheslav Zholudev; Lukas Lewandowski; Marcel Waldvogel
Hecate: Managing Authorization with RESTful XML Proceedings Article
In: Proceedings of WS-REST 2011, 2011.
Abstract | BibTeX | Tags: Identity Management, Security, XML | Links:
@inproceedings{Graf2011Hecate,
title = {Hecate: Managing Authorization with RESTful XML},
author = {Sebastian Graf and Vyacheslav Zholudev and Lukas Lewandowski and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2011/graf11hecate.pdf},
year = {2011},
date = {2011-03-28},
urldate = {1000-01-01},
booktitle = {Proceedings of WS-REST 2011},
abstract = {The potentials of REST offers new ways for communications between louse coupled entities featured through the Web of Things. The binding of the disjunct components of this architecture creates security issues, such as the centralized authorization techniques respecting the independence of the underlying entities. This results in the question how authorization is performed respecting the flexibility of REST without any knowledge about the underlying resources. Nevertheless, possible knowledge about these resources should enable the authorization workflow to offer finer-granular permissions on substructures of the resources. With our new approach - named Hecate - we offer a framework to assure simplified handling while keeping the potentials and flexibility of REST. We have designed an architecture based on XML with a flexible authorization mechanism on the one hand and optional resource-awareness on the other hand. The flexibility within the authorization work-flow bases on permission sets respecting the HTTP verbs. Additional in-depth knowledge of the entity optionally extends these permissions with resource-aware filters. Hecate offers not only great benefits because of its flexibility, but also because of the optional extensibility proved within the two reference implementations. With Hecate, we show that a centralized authorization mechanism combining independence and optional resource-based filtering extends the flexibility of REST rather than restricting it.},
keywords = {Identity Management, Security, XML},
pubstate = {published},
tppubtype = {inproceedings}
}
Sebastian Graf; Sebastian Kay Belle; Marcel Waldvogel
Rolling Boles, Optimal XML Structure Integrity for Updating Operations Proceedings Article
In: Proceedings of the 20th international conference on World Wide Web (WWW2011), pp. 49-50, ACM, Hyderabad, India, 2011.
Abstract | BibTeX | Tags: XML | Links:
@inproceedings{Graf2011Rolling,
title = {Rolling Boles, Optimal XML Structure Integrity for Updating Operations},
author = {Sebastian Graf and Sebastian Kay Belle and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2011/graf11rolling.pdf},
year = {2011},
date = {2011-03-28},
urldate = {1000-01-01},
booktitle = {Proceedings of the 20th international conference on World Wide Web (WWW2011)},
pages = {49-50},
publisher = {ACM},
address = {Hyderabad, India},
abstract = {While multiple techniques exist to utilize the tree structure of the Extensible Markup Language (XML) regarding integrity checks, they all rely on adaptions of the Merkle Tree: All children are acting as one slice regarding the checksum of one node with the help of an one-way hash concatenation. This results in postorder traversals regarding the (re-)computation of the integrity structure within modification operations. With our approach we perform nearly in-time updates of the entire integrity structure. We therefore equipped an XHash-based approach with an incremental hash function. This replaces postorder traversals by adapting only the incremental modifications to the checksums of a node and its ancestors. With experimental results we prove that our approach only generates a constant overhead depending on the depth of the tree while native DOMHash implementations produce an overhead based on the depth and the number of all nodes in the tree. Consequently, our approach called Rolling Boles generates sustainable impact since it facilitates instant integrity updates in constant time.},
keywords = {XML},
pubstate = {published},
tppubtype = {inproceedings}
}
Sebastian Graf; Marc Kramis; Marcel Waldvogel
Treetank, Designing A Versioned XML Storage Proceedings Article
In: XML Prague ’11, 2011.
Abstract | BibTeX | Tags: Cloud Storage, XML | Links:
@inproceedings{Graf2011Treetank,
title = {Treetank, Designing A Versioned XML Storage},
author = {Sebastian Graf and Marc Kramis and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2011/graf11treetank.pdf},
year = {2011},
date = {2011-03-26},
urldate = {1000-01-01},
booktitle = {XML Prague '11},
abstract = {XML underlies the same constant modification scenarios like any other resource especially in flexible environments like the WWW. Therefore, intelligent handling of versioned XML is mandatory. Due to the structural nature of XML, the efficient storage of changes in the data and therefor in the tree needs new paradigms regarding efficient storage and effective retrieval operations. We present a node granular XML versioning approach which relies on the independence of the storage and the versioning system. Different layers which have the ability to satisfy specific aspects of a node-granular versioning storage guarantee this independence. Results prove that our architecture offers efficient handling of consecutive changes within all modification scenarios while not restricting XML regarding its usage. Hence, our prototype system handles even huge XML instances while ensuring equal access to each revision of the data.},
keywords = {Cloud Storage, XML},
pubstate = {published},
tppubtype = {inproceedings}
}
Arshad Islam; Marcel Waldvogel
Questioning flooding as a routing benchmark in Opportunistic Networks Proceedings Article
In: Proceedings of the Baltic Congress on Future Internet Communications, pp. 128-133, 2011.
Abstract | BibTeX | Tags: Mobile Networks, Opportunistic Networks | Links:
@inproceedings{Islam2011Questioning,
title = {Questioning flooding as a routing benchmark in Opportunistic Networks},
author = {Arshad Islam and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2011/islam11questioning.pdf},
year = {2011},
date = {2011-03-26},
urldate = {1000-01-01},
booktitle = {Proceedings of the Baltic Congress on Future Internet Communications},
pages = {128-133},
abstract = {Routing in Opportunistic Networks, as a relatively young discipline, still lacks coherent, simple and valid benchmarks. It is customary to use epidemic routing as performance benchmark for Opportunistic Networks. We identify and describe the current simulation practices that do not expose the shortcomings of flooding as an upper bound. In this paper to provide a step towards a routing benchmark, which is flexible, provides results close to an upper bound, is simple to implement, and thus might be a candidate for a common benchmark. This new method called EPO, does not suffer from bottlenecks that limit the performance of epidemic flooding, even when bandwidth is scarce. Our analysis shows that networks are not suffering from that much severe congestion as suggested by flooding and thus giving a better insight to the underlying network.},
keywords = {Mobile Networks, Opportunistic Networks},
pubstate = {published},
tppubtype = {inproceedings}
}

Arshad Islam; Marcel Waldvogel
Optimizing Message Delivery in Mobile-Opportunistic Networks Proceedings Article
In: Proceedings of the Baltic Congress on Future Internet Communications, pp. 134-141, 2011, ISBN: 978-1-4244-8511-6.
Abstract | BibTeX | Tags: Mobile Networks, Opportunistic Networks | Links:
@inproceedings{Islam2011Optimizing,
title = {Optimizing Message Delivery in Mobile-Opportunistic Networks},
author = {Arshad Islam and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2011/islam11optimizing.pdf},
isbn = {978-1-4244-8511-6},
year = {2011},
date = {2011-02-16},
urldate = {1000-01-01},
booktitle = {Proceedings of the Baltic Congress on Future Internet Communications},
pages = {134-141},
abstract = {The big challenge of routing in opportunistic mobile networks, overlooked by most researchers, is to not only find any path to the destination, but a path that is stable and powerful enough to actually carry the message. Few attempts addressed this problem, all of them under controlled scenarios, avoiding the complexity of real-world connectivity. As a result of our comparison of selected networks under a wide variety of realistic scenarios, we have not only been able to identify and describe favorable traits of protocols, but also necessary relationship of successful MON protocols with QoS routing in wired networks. We present a novel protocol, Nile, that performs both in dense as well as sparse networks. Nile is the first autonomous “controlled Hooding” protocol that keeps the link loads in check, to push replicas only on those paths that are both promising and may sustain more load. It is a multi path protocol that deploys replication based on heuristic for disjoint path calculation. Other protocols' performance, when simulated in real-world traces, highly depends on parameter choice. Nile, however, consistently performs among the top protocols without any external tuning and exerts far less overhead than other replication protocols.},
keywords = {Mobile Networks, Opportunistic Networks},
pubstate = {published},
tppubtype = {inproceedings}
}

2010
Sebastian Graf; Lukas Lewandowski; Marcel Waldvogel
Integrity Assurance for RESTful XML Proceedings Article
In: Proceedings of WISM 2010, 2010.
Abstract | BibTeX | Tags: Security, XML | Links:
@inproceedings{Graf2010Integrity,
title = {Integrity Assurance for RESTful XML},
author = {Sebastian Graf and Lukas Lewandowski and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2010/graf10integrity.pdf},
year = {2010},
date = {2010-11-04},
urldate = {1000-01-01},
booktitle = {Proceedings of WISM 2010},
abstract = {The REpresentational State Transfer (REST) represents an extensible, easy and elegant architecture for accessing web-based resources. REST alone and in combination with XML is fast gaining momentum in a diverse set of web applications. REST is stateless, as is HTTP on which it is built. For many applications, this not enough, especially in the context of concurrent access and the increasing need for auditing and accountability. We present a lightweight mechanism which allows the application to control the integrity of the underlying resources in a simple, yet flexible manner. Based on an opportunistic locking approach, we show in this paper that XML does not only act as an extensible and direct accessible backend that ensures easy modifications due to the allocation of nodes, but also gives scalable possibilities to perform on-the-fly integrity verification based on the tree structure.},
keywords = {Security, XML},
pubstate = {published},
tppubtype = {inproceedings}
}
Thomas Zink; Marcel Waldvogel
Analysis and Efficient Classification of P2P File Sharing Traffic Technical Report
University of Konstanz Konstanz, Germany, no. KN-2010-DISY-02, 2010.
Abstract | BibTeX | Tags: Peer-to-Peer, Security, Traffic Engineering | Links:
@techreport{Zink2010Analysis,
title = {Analysis and Efficient Classification of P2P File Sharing Traffic},
author = {Thomas Zink and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2015/02/zink2010analysis.pdf},
year = {2010},
date = {2010-10-01},
urldate = {1000-01-01},
number = {KN-2010-DISY-02},
address = {Konstanz, Germany},
institution = {University of Konstanz},
abstract = {Since the advent of P2P networks they have grown to be the biggest source of internet traffic, superseding HTTP and FTP. For service providers P2P traffic results in increased costs for both infrastructure and transportation. Interest is high to reliably identify the type of service to ensure quality of service. In this document we analyze P2P network architectures and give an overview of existing identification mechanisms. In addition we devise a simple identification scheme suitable for implementation in resources restricted environments with limited computational power and memory. The scheme is based on behavior analysis and as such is not prone to traffic obfuscation techniques.},
keywords = {Peer-to-Peer, Security, Traffic Engineering},
pubstate = {published},
tppubtype = {techreport}
}
Sebastian Kay Belle; Oliver Haase; Marcel Waldvogel
CallForge: Call Anonymity in Cellular Networks Technical Report
University of Konstanz 2010.
Abstract | BibTeX | Tags: Mobile Networks, Privacy, Security | Links:
@techreport{Belle2010CallForge,
title = {CallForge: Call Anonymity in Cellular Networks},
author = {Sebastian Kay Belle and Oliver Haase and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2010/belle10callforge.pdf},
year = {2010},
date = {2010-05-19},
urldate = {1000-01-01},
booktitle = {PERVASIVE 2008 Workshop on Security and Privacy in Spontaneous Interaction and Mobile Phone Use (SPMU 2008)},
institution = {University of Konstanz},
abstract = {In cellular networks, the locations of all subscribers are continously tracked even when they only passively carry their mobile devices with them. This privacy sensitive data can be an invaluable source of information, not only for benevolent parties. We therefore present CallForge, the concept of a location management scheme that preserves the subscribers' anonymity -- in many cases even while they participate in a phone call -- as well as a theoretical analysis of the approach. CallForge improves on PathForge, a previously presented location management scheme, and as such is based on ID switching that we have combined with the emulation of a media break within a single call set-up procedure. We have analyzed and compared the anonymity of PathForge and CallForges, and shown that CallForge consistently provides superior anonymity. CallForge can be implemented entirely in the end device and run on existing network infrastructure without any modifications.},
keywords = {Mobile Networks, Privacy, Security},
pubstate = {published},
tppubtype = {techreport}
}
2009
Sebastian Kay Belle; Marcel Waldvogel
PathForge: Faithful Anonymization of Movement Data Proceedings Article
In: Proceedings of the 1st ACM workshop on Networking, systems, and applications for mobile handhelds (MobiHeld ’09), pp. 63-64, 2009.
Abstract | BibTeX | Tags: Mobile Networks, Privacy, Security | Links:
@inproceedings{Belle2009PathForge,
title = {PathForge: Faithful Anonymization of Movement Data},
author = {Sebastian Kay Belle and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2009/belle09pathforge.pdf},
year = {2009},
date = {2009-08-17},
urldate = {1000-01-01},
booktitle = {Proceedings of the 1st ACM workshop on Networking, systems, and applications for mobile handhelds (MobiHeld '09)},
pages = {63-64},
abstract = {For most mobile networks, providers need the current position of their users to provide efficient service. The resulting motion data is not only an invaluable source for analyzing traffic or flow patterns, but also for tracking an individual's whereabouts, even without their knowledge. Today, many carry at least one mobile networked device with them wherever they go, day and night. The resulting motion data can be used to reveal the most intimate details of our lives, making this information extremely privacy sensitive. In this paper, we present PathForge, a lightweight solution, which not only fulfills the provider's efficiency requirement, but continues to allow flow pattern analysis, yet provides full privacy for users when not actively involved in a call.},
keywords = {Mobile Networks, Privacy, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
Marc Kramis; Cedric Gabathuler; Sara Irina Fabrikant; Marcel Waldvogel
An XML-based Infrastructure to Enhance Geographic Visual Analytics Journal Article
In: Cartography and Geographic Information Science, vol. 36, no. 3, pp. 281-293, 2009.
Abstract | BibTeX | Tags: XML | Links:
@article{Kramis2009XML-based,
title = {An XML-based Infrastructure to Enhance Geographic Visual Analytics},
author = {Marc Kramis and Cedric Gabathuler and Sara Irina Fabrikant and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2009/kramis09xml-based.pdf},
year = {2009},
date = {2009-07-01},
urldate = {1000-01-01},
journal = {Cartography and Geographic Information Science},
volume = {36},
number = {3},
pages = {281-293},
abstract = {We propose a new, streamlined, two-step geographic visual analytics (GVA) workflow for efficient data storage and access based on a native web XML database called TreeTank coupled with a Scalable Vector Graphics (SVG) graphical user interface for visualization. This new storage framework promises better scalability with rapidly growing datasets available on the Internet, while also reducing data access and updating delays for collaborative GVA environments. Both improve interactivity and flexibility from an end-user perspective. The proposed framework relies on a REST-based web interface providing scalable and spatio-temporal read-write access to complex spatio-temporal datasets of structured, semi-structured, or unstructured data. The clean separation of client and server at the HTTP web layer assures backward compatibility and better extensibility. We discuss the proposed framework and apply it on a prototype implementation employing world debt data. The excellent compression ratio of SVG as well as its fast delivery to end users are encourageing and suggest important steps have been made towards dynamic, highly interactive, and collaborative geovisual analytics environments.},
keywords = {XML},
pubstate = {published},
tppubtype = {article}
}

Florian Mansmann; Fabian Fischer; Daniel A. Keim; Stephan Pietzko; Marcel Waldvogel
Interactive Analysis of NetFlows for Misuse Detection in Large IP Networks Proceedings Article
In: DFN-Forum Kommunikationstechnologie, Garching (Munich), Germany, 2009.
Abstract | BibTeX | Tags: Intrusion Detection, Security | Links:
@inproceedings{Mansmann2009Interactive,
title = {Interactive Analysis of NetFlows for Misuse Detection in Large IP Networks},
author = {Florian Mansmann and Fabian Fischer and Daniel A. Keim and Stephan Pietzko and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2009/mansmann09interactive.pdf},
year = {2009},
date = {2009-05-01},
urldate = {1000-01-01},
booktitle = {DFN-Forum Kommunikationstechnologie},
address = {Garching (Munich), Germany},
abstract = {While more and more applications require higher network bandwidth, there is also a tendency that large portions of this bandwidth are misused for dubious purposes, such as unauthorized VoIP, file sharing, or criminal botnet activity. Automatie intrusion detection methods can detcct a large portion of such misuse, but novel patterns can only be detected by humans. Moreover, interpretation of large amounts of alerts imposes new challenges on the analysts. The goal of this paper is to preseot the visual analysis system NFlowVis to interactively detcct unwanted usage of the network infrastructure either by pivoting NetFlows using IOS alerts or by specifying usage patterns, such as sets of suspicious port numbers. Thereby, our work focuses on providing a scalable approach to store and retrieve large quantities of Netflows by means of a database management system.},
keywords = {Intrusion Detection, Security},
pubstate = {published},
tppubtype = {inproceedings}
}

Thomas Zink; Marcel Waldvogel
Packet Forwarding using Efficient Hash Tables Technical Report
University of Konstanz Konstanz, Germany, no. KN-2009-DISY-01, 2009.
Abstract | BibTeX | Tags: Fast Routers, Hash Tables | Links:
@techreport{Zink2009Packet,
title = {Packet Forwarding using Efficient Hash Tables},
author = {Thomas Zink and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2015/02/zink2009packet.pdf},
year = {2009},
date = {2009-04-03},
urldate = {1000-01-01},
number = {KN-2009-DISY-01},
address = {Konstanz, Germany},
institution = {University of Konstanz},
abstract = {This report discusses our proposed improvements to Fast Hash Tables (FHT) which we name ’Efficient Hash Table’ (EHT) where ’efficient’ relates to both memory efficiency and lookup performance. The mechanism we use to design the EHT lead to improvements in terms of SRAM memory requirements by the factor of ten over the FHT. Our results back the theoretical analysis and allow accurate predictions. A cost function is provided that allows the adjustment of EHT parameter to different user requirements.},
keywords = {Fast Routers, Hash Tables},
pubstate = {published},
tppubtype = {techreport}
}
2008
Sebastian Kay Belle; Muhammad Arshad Islam; Marcel Waldvogel
I Seek for Knowledge: Exploiting Social Properties in Mobile Ad-Hoc Networks Proceedings Article
In: In Proceedings of 1st IFIP Wireless Days 2008, pp. 1-5, 2008.
Abstract | BibTeX | Tags: Opportunistic Networks, Privacy, Social Networks | Links:
@inproceedings{Belle2008I,
title = {I Seek for Knowledge: Exploiting Social Properties in Mobile Ad-Hoc Networks},
author = {Sebastian Kay Belle and Muhammad Arshad Islam and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2008/belle08iseek.pdf},
year = {2008},
date = {2008-11-24},
urldate = {1000-01-01},
booktitle = {In Proceedings of 1st IFIP Wireless Days 2008},
pages = {1-5},
abstract = {New social networks are born each day, at a formal conference, at informal social gathering, at family reunions etc. Internet has already been playing an important role to let people socialize through online social websites. For many users, its still not the optimal way of interaction as one has to be very active updating their activities on the online profiles. With the easy access to mobile devices, modern technologies have now started to adopt to more human of socializing. As these mobile devices accompany their users almost all the time, they can record and observe their users behavior as well as gather information about their social circle. Therefore, they can help users to get information from contacts, that they potentially not even know. In this paper we put our efforts towards the initial design of such an architecture, we call \emph{Mergenet}, that will sniff for information around the user's surrounding, leveraging useful answers on their demand.
},
keywords = {Opportunistic Networks, Privacy, Social Networks},
pubstate = {published},
tppubtype = {inproceedings}
}
Sebastian Graf; Marc Kramis; Marcel Waldvogel
Distributing XML with Focus on Parallel Evaluation Proceedings Article
In: Sixth International Workshop on Databases, Information Systems and Peer-to-Peer Computing (DBISP2P 2008), pp. 55-67, 2008.
Abstract | BibTeX | Tags: Cloud Storage, XML | Links:
@inproceedings{Graf2008Distributing,
title = {Distributing XML with Focus on Parallel Evaluation},
author = {Sebastian Graf and Marc Kramis and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2008/graf08distributing.pdf},
year = {2008},
date = {2008-08-23},
urldate = {1000-01-01},
booktitle = {Sixth International Workshop on Databases, Information Systems and Peer-to-Peer Computing (DBISP2P 2008)},
pages = {55-67},
abstract = {In contrast to relational databases the distribution of document-centric XML is not well researched. While there are some suggestions on how to split and distribute large XML documents, these approaches do not consider the parallel query evaluation. In this paper, we present and compare five different algorithms to search after suitable split nodes in
a large XML document. We then describe how to distribute extractable substructures over a fixed number of peers and how to query these peers in parallel to retrieve the final result. In addition, we analyse the impact of our splitting algorithms with respect to scalability for two different XPath expression classes on three well-known XML data sets. We conclude this paper with an outlook on future work, including result ordering during parallel query execution and dynamic re-distribution of XML fragments to new peers due to updates.},
keywords = {Cloud Storage, XML},
pubstate = {published},
tppubtype = {inproceedings}
}
a large XML document. We then describe how to distribute extractable substructures over a fixed number of peers and how to query these peers in parallel to retrieve the final result. In addition, we analyse the impact of our splitting algorithms with respect to scalability for two different XPath expression classes on three well-known XML data sets. We conclude this paper with an outlook on future work, including result ordering during parallel query execution and dynamic re-distribution of XML fragments to new peers due to updates.
Fabian Fischer; Florian Mansmann; Daniel A. Keim; Stephan Pietzko; Marcel Waldvogel
Large-scale Network Monitoring for Visual Analysis of Attacks Proceedings Article
In: 5th International Workshop on Visualization for Cyber Security (VizSEC 2008), Cambridge, MA, USA, 2008.
Abstract | BibTeX | Tags: Intrusion Detection, Security | Links:
@inproceedings{Fischer2008Large-scale,
title = {Large-scale Network Monitoring for Visual Analysis of Attacks},
author = {Fabian Fischer and Florian Mansmann and Daniel A. Keim and Stephan Pietzko and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2008/fischer08large-scale.pdf},
year = {2008},
date = {2008-08-15},
urldate = {1000-01-01},
booktitle = {5th International Workshop on Visualization for Cyber Security (VizSEC 2008)},
address = {Cambridge, MA, USA},
abstract = {The importance of the Internet and our dependency on computer networks are steadily growing, which results in high costs and substantial consequences in case of successful intrusions, stolen data, and interrupted services. At the same time, a trend towards massive attacks against the network infrastructure is noticeable. Therefore, monitoring large networks has become an important field in practice and research. Through monitoring systems, attacks can be detected and analyzed to gain knowledge of how to better protect the network in the future. In the scope of this paper, we present a system to analyze NetFlow data using a relational database system. NetFlow records are linked with alerts from an intrusion detection system to enable efficient exploration of suspicious activity within the monitored network. Within the system, the monitored network is mapped to a TreeMap visualization, the attackers are arranged at the borders and linked using splines parameterized with prefix information. In a series of case studies, we demonstrate how the tool can be used to judge the relevance of alerts, to reveal massive distributed attacks, and to analyze service usage within a network.},
keywords = {Intrusion Detection, Security},
pubstate = {published},
tppubtype = {inproceedings}
}

Sebastian Kay Belle; Marcel Waldvogel
Consistent Deniable Lying: Privacy in Mobile Social Networks Proceedings Article
In: Pervasive 2008 Workshop on Security and Privacy Issues in Mobile Phone Use (SPMU 2008), Sydney, Australia, 2008.
Abstract | BibTeX | Tags: Opportunistic Networks, Peer-to-Peer, Privacy, Security, Social Networks | Links:
@inproceedings{Belle2008Consistent,
title = {Consistent Deniable Lying: Privacy in Mobile Social Networks},
author = {Sebastian Kay Belle and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2008/belle08consistent.pdf},
year = {2008},
date = {2008-05-19},
urldate = {1000-01-01},
booktitle = {Pervasive 2008 Workshop on Security and Privacy Issues in Mobile Phone Use (SPMU 2008)},
address = {Sydney, Australia},
abstract = {Social networking is moving to mobile phones. This not only means continuous access, but also allows to link virtual and physical neighbourhood in novel ways. To make such systems useful, personal data such as lists of friends and interests need to be shared with more and frequently unknown people, posing a risk to your privacy. In this paper, we present our approach to social networking, Consistent Deniable Lying (CDL). Using easy-to-understand mechanisms and tuned to this environment, it enables you to meet new friends with joint interests while limiting exposure of your private data. Not only can it be generalised to include “friends of friends” (transitivity) into interest search, it allows you to plausibly refute any allegations of your claimed interests. Unlike prior work, we focus on the application to similarity finding and include the novel aspects of transitivity and deniability, which are key to success in social networks.},
keywords = {Opportunistic Networks, Peer-to-Peer, Privacy, Security, Social Networks},
pubstate = {published},
tppubtype = {inproceedings}
}
Sebastian Graf; Marcel Waldvogel
Splitting and Distributing Large Document-Centric XML Databases Technical Report
University of Konstanz no. KN-2008-DISY-04, 2008.
BibTeX | Tags:
@techreport{Graf2008Splitting-techreport,
title = {Splitting and Distributing Large Document-Centric XML Databases},
author = {Sebastian Graf and Marcel Waldvogel},
year = {2008},
date = {2008-01-01},
urldate = {1000-01-01},
number = {KN-2008-DISY-04},
institution = {University of Konstanz},
keywords = {},
pubstate = {published},
tppubtype = {techreport}
}

Arshad Islam; Marcel Waldvogel
Reality-Check for DTN Routing Algorithms Proceedings Article
In: ICDCSW ’08: Proceedings of the 2008 The 28th International Conference on Distributed Computing Systems Workshops, pp. 204–209, IEEE Computer Society, Washington, DC, USA, 2008, ISBN: 978-0-7695-3173-1.
Abstract | BibTeX | Tags: Opportunistic Networks | Links:
@inproceedings{Islam2008Reality-Check,
title = {Reality-Check for DTN Routing Algorithms},
author = {Arshad Islam and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2008/islam08reality.pdf},
isbn = {978-0-7695-3173-1},
year = {2008},
date = {2008-01-01},
urldate = {1000-01-01},
booktitle = {ICDCSW '08: Proceedings of the 2008 The 28th International Conference on Distributed Computing Systems Workshops},
pages = {204--209},
publisher = {IEEE Computer Society},
address = {Washington, DC, USA},
abstract = {Many applications of ad-hoc networks include intermittent connectivity. Anyone wishing to implement routing into her delay-tolerant network can select from a wide variation of options, but the choice is hard, as there is no strong comparative evidence to the relative performance of the algorithms. Every paper uses a different setting, mostly far from realistic. In our desire to improve the basis for decisions, we simulated a promising selection of DTN routing algorithms in three vastly different scenarios, all based on publicly available real-world traces. Using our open-source DTN simulator, we compare and analyse 11 routing techniques, then provide explanations for the behaviour and give advice for choosing a suitable mechanism. To our own surprise, the results challenge the conventional wisdom gained from synthetic simulations and poses the question whether the world is ready for DTNs.
},
keywords = {Opportunistic Networks},
pubstate = {published},
tppubtype = {inproceedings}
}
2007
Daniel Bauer; Paul Hurley; Marcel Waldvogel
Replica Placement and Location using Distributed Hash Tables Proceedings Article
In: Proceedings of IEEE LCN, pp. 315-324, 2007, ISBN: 0-7695-3000-1.
Abstract | BibTeX | Tags: Peer-to-Peer, Replication | Links:
@inproceedings{Bauer2007Replica,
title = {Replica Placement and Location using Distributed Hash Tables},
author = {Daniel Bauer and Paul Hurley and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2007/bauer07replica.pdf},
isbn = {0-7695-3000-1},
year = {2007},
date = {2007-10-15},
urldate = {2007-10-15},
booktitle = {Proceedings of IEEE LCN},
pages = {315-324},
crossref = {DBLP:conf/lcn/2007},
abstract = {Interest in distributed storage is fueled by demand for reliability and resilience combined with decreasing hardware costs. Peer-to-peer storage networks based on distributed hash tables are attractive for their efficient use of resources and resulting performance. The placement and subsequent efficient location of replicas in such systems remain open problems, especially (1) the requirement to update replicated content, (2) working in the absence of global information, and (3) determination of the locations in a dynamic system without introducing single points of failure. We present and evaluate a novel and versatile technique, replica enumeration, which allows for controlled replication and replica access. The possibility of enumerating and addressing individual replicas allows dynamic updates as well as superior performance without burdening the network with state information, yet taking advantage of locality information when available. We simulate, analyze, and prove properties of the system, and discuss some applications.},
keywords = {Peer-to-Peer, Replication},
pubstate = {published},
tppubtype = {inproceedings}
}
Marcel Waldvogel; Tobias Köck
Light-weight End-to-End QoS as DoS Prevention Proceedings Article
In: Proceedings of IEEE LCN 2007, 2007.
Abstract | BibTeX | Tags: Denial of Service, Quality of Service, Security | Links:
@inproceedings{Waldvogel2007Light-weight,
title = {Light-weight End-to-End QoS as DoS Prevention},
author = {Marcel Waldvogel and Tobias Köck},
url = {https://netfuture.ch/wp-content/uploads/2006/waldvogel06light-weight.pdf},
year = {2007},
date = {2007-09-01},
urldate = {1000-01-01},
booktitle = {Proceedings of IEEE LCN 2007},
abstract = {Despite decades of QoS research and many years of DoS defence work, neither group of proponents have been able to get their results included into mainstream Internet service. It seems that demand for either solution exists, but individually, they seem to be just below the cost/ benefit threshold. This paper proposes a first step into a common solution, where combined and extended interests will hopefully allow us to surpass this threshold. While there are still some open issues, we hope to not only pro- pose a basic working mechanism but also provide fresh ideas to start thinking off the beaten path. Our main contribution is to create a lightweight, end-to-end binding between path and service, which is then used as a basis to associate fur- ther attributes and mechanisms to this binding. As a result, both DoS defence and QoS can be achieved with stateless routers and only with prior consent of receiving the end sys- tems, short, achieving several of the IntServ advantages in a DiffServ-style system, i.e., avoiding per-connection state.},
keywords = {Denial of Service, Quality of Service, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
Paul Hurley; Marcel Waldvogel
Bloom Filters: One Size Fits All? Proceedings Article
In: Proceedings of IEEE LCN 2007, pp. 183-190, 2007, ISSN: 0742-1303.
Abstract | BibTeX | Tags: Bloom Filters, Hash Tables | Links:
@inproceedings{Hurley2007Bloom,
title = {Bloom Filters: One Size Fits All?},
author = {Paul Hurley and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2007/waldvogel07bloom.pdf},
issn = {0742-1303},
year = {2007},
date = {2007-06-17},
urldate = {1000-01-01},
booktitle = {Proceedings of IEEE LCN 2007},
journal = {lcn},
pages = {183-190},
abstract = {Bloom filters impress by their sheer elegance and have become a widely and indiscriminately used tool in network applications, although, as we show, their performance can often be far from optimal. Notably in application areas where false negatives are tolerable, other techniques can clearly be better. We show that, at least for a specific area in the parameter space, Bloom filters are significantly outperformed even by a simple scheme. We show that many application areas where Bloom filters are deployed do not require the strong policy of no false negatives and sometimes even prefer false negatives. We analyze, through modelling, how far Bloom filters are from the optimal and then examine application specific issues in a distributed web caching scenario. We hope to open up and seed discussion towards domain-specific alternatives to Bloom filters while perhaps sparking ideas for a general-purpose alternative.},
keywords = {Bloom Filters, Hash Tables},
pubstate = {published},
tppubtype = {inproceedings}
}
Marc Kramis; Volker Wildi; Bastian Lemke; Sebastian Graf; Halldór Janetzko; Marcel Waldvogel
jSCSI – A Java iSCSI Initiator Proceedings Article
In: Paper for: Jazoon’07 – Internationale Konferenz für Java-Technologie, Universität Konstanz, 2007.
Abstract | BibTeX | Tags: Cloud Storage | Links:
@inproceedings{Kramis07jscsi,
title = {jSCSI – A Java iSCSI Initiator},
author = {Marc Kramis and Volker Wildi and Bastian Lemke and Sebastian Graf and Halldór Janetzko and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2013/12/jscsi_slides.pdf},
year = {2007},
date = {2007-01-01},
urldate = {1000-01-01},
booktitle = {Paper for: Jazoon'07 – Internationale Konferenz für Java-Technologie},
publisher = {Universität Konstanz},
abstract = {Accessing persistent storage from Java usually means talking to the file system through the frugal Java file system abstraction, i.e., the File class. Currently, there is no platform-independent way to directly talk to a single local or remote storage device, yet alone a device pool. jSCSI aims to fill this gap by implementing the iSCSI protocol right in Java. We believe that firstly, Java is mature enough to cleanly implement well-performing low-level storage protocols and secondly, that it would be very convenient to plug a terabyte-sized iSCSI RAID into the local network and immediately connect to it from any JVM.},
keywords = {Cloud Storage},
pubstate = {published},
tppubtype = {inproceedings}
}

2006
Halldór Janetzko; Daniel A. Keim; Marc Kramis; Florian Mansmann; Marcel Waldvogel
Interactive Poster: Exploring Block Access Patterns of Native XML Storage Proceedings Article
In: Proceedings of InfoVis 2006, 2006.
Abstract | BibTeX | Tags: XML | Links:
@inproceedings{Janetzko2006Exploring,
title = {Interactive Poster: Exploring Block Access Patterns of Native XML Storage},
author = {Halldór Janetzko and Daniel A. Keim and Marc Kramis and Florian Mansmann and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2006/janetzko06exploring.pdf},
year = {2006},
date = {2006-10-29},
urldate = {1000-01-01},
booktitle = {Proceedings of InfoVis 2006},
abstract = {Recent block-based native XML storage systems such as IDEFIX touch blocks according to the XQuery engine’s execution plan. The resulting access patterns are virtually unknown and potentially cause many expensive disk seeks. Visualization comes to the rescue when extensive log files must be analyzed – a tedious and difficult task. The dynamic time-based block-touch animation as well as the static block-type information of VISUAL IDEFIX foster the insight into the performance-critical internals of the XML storage and help to optimize both the block layout and the XQuery engine to speed up queries.},
keywords = {XML},
pubstate = {published},
tppubtype = {inproceedings}
}

Marcel Waldvogel; Michael Muncan; Mahak Patidar
Stealth DoS Proceedings Article
In: Proceedings of IEEEslash IST Workshop on Monitoring, Attack Detection, and Mitigation (MonAM 2006), 2006.
Abstract | BibTeX | Tags: Denial of Service, Security | Links:
@inproceedings{Waldvogel2006Stealth,
title = {Stealth DoS},
author = {Marcel Waldvogel and Michael Muncan and Mahak Patidar},
url = {https://netfuture.ch/wp-content/uploads/2006/waldvogel06stealth.pdf},
year = {2006},
date = {2006-09-28},
urldate = {1000-01-01},
booktitle = {Proceedings of IEEEslash IST Workshop on Monitoring, Attack Detection, and Mitigation (MonAM 2006)},
abstract = {Users and providers increasingly disagree on what Denial of Service (DoS) is. For example, an ISP might consider large multimedia downloads an attack to overload its infrastructure or have it pay high interconnection fees. On the other hand, a user will certainly consider selective bandwidth reduction that is used by ISPs as a countermea- sure, as a DoS measure. Given the nature of their business relationship, neither side is likely to openly admit that they are fighting each other. In this paper we attempt to formalise the concept of Stealth DoS, including listing mechanisms that may be used at high speed. We concentrate on mechanisms that might be used in one particular area, voice over IP (VoIP). We start evaluating them under the different aspects, including their cost, political suitability and the likelihood for countermeasures to succeed. We expect that this will give both sides better insight on their options and plea for peace, hopefully in an attempt to avoid and open war.},
keywords = {Denial of Service, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
Christian Grün; Alexander Holupirek; Marc Kramis; Marc H. Scholl; Marcel Waldvogel
Pushing XPath Accelerator to its Limits Proceedings Article
In: Proceedings of the First International Workshop on Performance and Evaluation of Data Management Systems (EXPDB 2006), ACM, 2006.
Abstract | BibTeX | Tags: XML | Links:
@inproceedings{Gruen2006Pushing,
title = {Pushing XPath Accelerator to its Limits},
author = {Christian Grün and Alexander Holupirek and Marc Kramis and Marc H. Scholl and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2006/gruen06pushing.pdf},
year = {2006},
date = {2006-06-01},
urldate = {1000-01-01},
booktitle = {Proceedings of the First International Workshop on Performance and Evaluation of Data Management Systems (EXPDB 2006)},
publisher = {ACM},
abstract = {<p>Two competing encoding concepts are known to scale well with growing amounts of XML data: XPath Accelerator encoding implemented by MonetDB for in-memory documents and X-Hive's Persistent DOM for on-disk storage. We identified two ways to improve XPath Accelerator and present prototypes for the respective techniques: BaseX boosts inmemory performance with optimized data and value index structures while Idefix introduces native block-oriented persistence with logarithmic update behavior for true scalability, overcoming main-memory constraints.</p><p>An easy-to-use Java-based benchmarking framework was developed and used to consistently compare these competing techniques and perform scalability measurements. The established XMark benchmark was applied to all four systems under test. Additional fulltext-sensitive queries against the well-known DBLP database complement the XMark results. Not only did the latest version of X-Hive finally surprise with good scalability and performance numbers. Also, both BaseX and Idefix hold their promise to push XPath Accelerator to its limits: BaseX efficiently exploits available main memory to speedup XML queries while Idefix surpasses main-memory constraints and rivals the on-disk leadership of X-Hive. The competition between XPath Accelerator and Persistent DOM definitely is relaunched.</p>},
keywords = {XML},
pubstate = {published},
tppubtype = {inproceedings}
}

2004
Daniel Bauer; Paul Hurley; Roman Pletka; Marcel Waldvogel
Bringing Efficient Advanced Queries to Distributed Hash Tables Proceedings Article
In: Proceedings of IEEE LCN, 2004.
Abstract | BibTeX | Tags: Peer-to-Peer | Links:
@inproceedings{Bauer2004Bringing,
title = {Bringing Efficient Advanced Queries to Distributed Hash Tables},
author = {Daniel Bauer and Paul Hurley and Roman Pletka and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2004/bauer04bringing.pdf},
year = {2004},
date = {2004-11-01},
urldate = {1000-01-01},
booktitle = {Proceedings of IEEE LCN},
abstract = {Interest in distributed storage is fueled by demand for reliability and resilience combined with ubiquitous availability. Peer-to-peer (P2P) storage networks are known for their decentralized control, self-organization, and adaptation. Advanced searching for documents and resources remains an open problem. The flooding approach favored by some P2P networks is ineffiencient in resource usage, but more scalable and resource-efficient solutions based on Distributed Hash Tables (DHT) lack in query expressiveness and flexibility. In this paper, we address this issue and introduce new efficient, scalable, and completely distributed methods that strive to keep resource consumption by queries and index information as low as possible. We describe how to improve the handling of multiple subqueries combined through boolean set operators. The need for these operators is intensified by applications to go beyond simple exact keyword matches. We discuss, optimize, and analyze appropriate extensions to support range and prefix matching in DHTs.},
keywords = {Peer-to-Peer},
pubstate = {published},
tppubtype = {inproceedings}
}
Samphel Norden; Milind M. Buddhikot; Marcel Waldvogel; Subhash Suri
Routing Bandwidth Guaranteed Paths with Restoration in Label Switched Networks Journal Article
In: Computer Networks, vol. 46, no. 2, pp. 197-218, 2004.
Abstract | BibTeX | Tags: Traffic Engineering | Links:
@article{Norden2004Routing,
title = {Routing Bandwidth Guaranteed Paths with Restoration in Label Switched Networks},
author = {Samphel Norden and Milind M. Buddhikot and Marcel Waldvogel and Subhash Suri},
url = {https://netfuture.ch/wp-content/uploads/2004/norden04routing.pdf},
year = {2004},
date = {2004-10-07},
urldate = {1000-01-01},
journal = {Computer Networks},
volume = {46},
number = {2},
pages = {197-218},
abstract = {A Network Service Provider (NSP) operating a label-switched networks such as ATM or Multi-Protocol Label Switching (MPLS) networks, sets up end-to-end bandwidth-guaranteed Label-Switched Paths (LSPs) to satisfy the connectivity requirements of its client networks. To make such a service highly available, the NSP may set up one or more backup LSPs for every active LSP. The backup LSPs are activated when the corresponding active LSP fails. Accordingly, the problem of LSP routing with and without restoration backup has received some attention in the recent past.</p><p>In this paper, we investigate distributed algorithms for routing of end-to-end LSPs with backup restoration in the context of label-switched networks. Specifically, we propose a new concept of the Backup Load Distribution (BLD) matrix that captures partial network state and eliminates the problems of bandwidth wastage, pessimistic link selection, and bandwidth release ambiguity. We describe two new, distributed routing algorithms that utilize the BLD matrix and require a bounded amount of run time. We can realize these algorithms in the current Internet architecture using the OSPF extensions for Quality-of-Service (QoS) routing to exchange the proposed BLD matrix among peer routers/switches. Our simulation results for realistic sample topologies show an excellent (30-50%) improvement in terms of rejected requests and 30-40% savings in the total bandwidth used for backup connections. We also show that, although the performance of our routing scheme is sensitive to the frequency of BLD matrix updates, the performance degradation resulting due to stale state information is insignificant for typical update periods.},
keywords = {Traffic Engineering},
pubstate = {published},
tppubtype = {article}
}
Sean Rooney; Christopher J. Giblin; Marcel Waldvogel; Paul T. Hurley
Identifying a Distributed Denial of Service (DDoS) Attack within a Network and Defending Against such an Attack Miscellaneous
International Patent TWI332159, 2004.
Abstract | BibTeX | Tags: Denial of Service, Security | Links:
@misc{Rooney2004Identifying,
title = {Identifying a Distributed Denial of Service (DDoS) Attack within a Network and Defending Against such an Attack},
author = {Sean Rooney and Christopher J. Giblin and Marcel Waldvogel and Paul T. Hurley},
url = {https://netfuture.ch/wp-content/uploads/2017/01/us2006010389a1.pdf},
year = {2004},
date = {2004-04-05},
urldate = {1000-01-01},
abstract = {The invention provides methods, apparatus and systems for detecting distributed denial of service (DDoS) attacks within the Internet by sampling packets at a point or points in Internet backbone connections to determine a packet metric parameter. The packet metric parameter which might comprise the volume of packets received is analysed over selected time intervals with respect to specified geographical locations in which the hosts transmitting the packets are located. The expected behaviour can be employed to identify traffic distortions revealing a DDoS attack. In a complementary aspect, the invention provides a method of authenticating packets at routers in order to elevate the QoS of authenticated packets. This method can be used to block or filter packets and can be used in conjunction with the DDoS attack detection system to defend against DDoS attacks within the Internet in a distributed manner.},
howpublished = {International Patent TWI332159},
keywords = {Denial of Service, Security},
pubstate = {published},
tppubtype = {misc}
}
Andreas Doering; Marcel Waldvogel
Fast and Flexible CRC Calculation Journal Article
In: IEE Electronics Letters, vol. 40, no. 1, pp. 10-11, 2004.
Abstract | BibTeX | Tags: CRC, FPGA, Network Processors | Links:
@article{Doering2004Fast,
title = {Fast and Flexible CRC Calculation},
author = {Andreas Doering and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2004/doering04fast.pdf},
year = {2004},
date = {2004-01-01},
urldate = {1000-01-01},
journal = {IEE Electronics Letters},
volume = {40},
number = {1},
pages = {10-11},
abstract = {An algorithm for software or hardware implementation is presented, allowing fast computation of Cyclic Redundancy Checks with arbitrary polynomials and a high flexibility, such as updating of checksums after modifying data block parts with a known old checksum.},
keywords = {CRC, FPGA, Network Processors},
pubstate = {published},
tppubtype = {article}
}
2003
Andreas Kind; Roman Pletka; Marcel Waldvogel
The Role of Network Processors in Active Networks Proceedings Article
In: Proceedings of IWAN 2003, pp. 18-29, Kyoto, Japan, 2003.
Abstract | BibTeX | Tags: Active Networks, Network Processors, Quality of Service, Security | Links:
@inproceedings{Kind2003Role,
title = {The Role of Network Processors in Active Networks},
author = {Andreas Kind and Roman Pletka and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2003/kind03role.pdf},
year = {2003},
date = {2003-12-01},
urldate = {1000-01-01},
booktitle = {Proceedings of IWAN 2003},
pages = {18-29},
address = {Kyoto, Japan},
abstract = {Network processors (NPs) implement a balance between hardware and software that addresses the demand of performance and programmability in active networks (AN). We argue that this makes them an important player in the implementation and deployment of ANs. Besides a general introduction into the relationship of NPs and ANs, we describe the power of this combination in a framework for secure and safe capsule-based active code. We also describe the advantages of offloading AN control point functionality into the NP and how to execute active code in the data path efficiently. Furthermore, the paper reports on experiences about implementing active networking concepts on the IBM PowerNP network processor. },
keywords = {Active Networks, Network Processors, Quality of Service, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
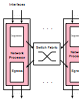
Roman Pletka; Marcel Waldvogel; Soenke Mannal
PURPLE: Predictive Active Queue Management Utilizing Congestion Information Proceedings Article
In: Proceedings of IEEE LCN 2003, pp. 21–30, 2003.
Abstract | BibTeX | Tags: | Links:
@inproceedings{Pletka2003PURPLE,
title = {PURPLE: Predictive Active Queue Management Utilizing Congestion Information},
author = {Roman Pletka and Marcel Waldvogel and Soenke Mannal},
url = {https://netfuture.ch/wp-content/uploads/2003/pletka03purple.pdf},
year = {2003},
date = {2003-10-01},
urldate = {1000-01-01},
booktitle = {Proceedings of IEEE LCN 2003},
pages = {21--30},
abstract = {Active Queue Management (AQM) is an attempt to find a delicate balance between two antagonistic Internet queuing requirements: First, buffer space should be maximized to accommodate the possibly huge transient bursts; second, buffer occupation should be minimum so as not to introduce unnecessary end-to-end delays. Traditional AQM mechanisms have been built on heuristics to achieve this balance, and have mostly done so quite well, but often require manual tuning or have resulted in slow convergence. In contrast, the PURPLE approach predicts the impact of its own actions on the behavior of reactive protocols and thus on the short-term future traffic without keeping per-flow state. PURPLE allows much faster convergence of the main AQM parameters, at least towards a local optimum, thereby smoothing and minimizing both congestion feedback and queue occupancy. To improve the quality of the prediction, we also passively monitor (using lightweight operations) information pertaining to the amount of congestion elsewhere in the network, for example, as seen by flows traversing this router.},
keywords = {},
pubstate = {published},
tppubtype = {inproceedings}
}
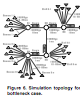
Germano Caronni; Marcel Waldvogel
Establishing Trust in Distributed Storage Providers Proceedings Article
In: Proceedings of Third IEEE International Conference on Peer-to-Peer Computing (P2P 2003), 2003.
Abstract | BibTeX | Tags: Cloud Storage, Peer-to-Peer, Replication, Trust | Links:
@inproceedings{Caronni2003Establishing,
title = {Establishing Trust in Distributed Storage Providers},
author = {Germano Caronni and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2003/caronni03establishing.pdf},
year = {2003},
date = {2003-09-01},
urldate = {1000-01-01},
booktitle = {Proceedings of Third IEEE International Conference on Peer-to-Peer Computing (P2P 2003)},
abstract = {Corporate IT as well as individuals show increasing interest in reliable outsourcing of storage infrastructure. Decentralized solutions with their resilience against partial outages are among the most attractive approaches. Irrespective of the form of the relationship, be it based on a contract or on the more flexible cooperative model, the problem of verifying whether someone promising to store one's data actually does so remains to be solved, especially in the presence of multiple replicas. In this paper, we introduce a lightweight mechanism that allows the \textit{data originator} or a dedicated \textit{verification agent} to build up trust in the \textit{replica holder} by means of protocols that do not require prior trust or key establishment. We show how naive versions of the protocol do not prevent cheating, and then strengthen it by adding means that make it economically attractive to be honest. This provides a foundation for further work in providing trustworthy distributed storage.},
keywords = {Cloud Storage, Peer-to-Peer, Replication, Trust},
pubstate = {published},
tppubtype = {inproceedings}
}
Marcel Waldvogel; Paul Hurley; Daniel Bauer
Dynamic Replica Management in Distributed Hash Tables Technical Report
IBM no. RZ–3502, 2003.
Abstract | BibTeX | Tags: Peer-to-Peer, Replication | Links:
@techreport{Waldvogel2003Dynamic-techreport,
title = {Dynamic Replica Management in Distributed Hash Tables},
author = {Marcel Waldvogel and Paul Hurley and Daniel Bauer},
url = {https://netfuture.ch/wp-content/uploads/2003/waldvogel03dynamic-techreport.pdf},
year = {2003},
date = {2003-07-01},
urldate = {1000-01-01},
number = {RZ--3502},
institution = {IBM},
abstract = {Interest in distributed storage is fueled by demand for reliability and resilience combined with decreasing hardware costs. Peer-to-peer storage networks based on distributed hash tables are an attractive solution due to their efficient use of resources and resulting performance. The placement and subsequent efficient location of replicas in such systems remain open problems, especially<ol><li>the requirement to update replicated content,</li><li>working in the absence of global information, and</li><li>how to determine the locations in a dynamic system without introducing single points of failure.</li></ol>We present and evaluate a novel and versatile technique, replica enumeration, which allows for controlled replication and replica access. The possibility of enumerating and addressing individual replicas allows dynamic updates as well as superior performance without burdening the network with state information, yet taking advantage of locality information when available. We simulate, analyze, and prove properties of the system, and discuss some applications.},
keywords = {Peer-to-Peer, Replication},
pubstate = {published},
tppubtype = {techreport}
}
- the requirement to update replicated content,
- working in the absence of global information, and
- how to determine the locations in a dynamic system without introducing single points of failure.
Marcel Waldvogel; Wei Deng; Ramaprabhu Janakiraman
Efficient Buffer Management for Scalable Media-on-Demand Proceedings Article
In: SPIE Multimedia Computing and Networking (MMCN 2003), Santa Clara, CA, USA, 2003.
Abstract | BibTeX | Tags: Multicast, Video-on-Demand | Links:
@inproceedings{Waldvogel2003Efficient,
title = {Efficient Buffer Management for Scalable Media-on-Demand},
author = {Marcel Waldvogel and Wei Deng and Ramaprabhu Janakiraman},
url = {https://netfuture.ch/wp-content/uploads/2003/waldvogel03efficient.pdf},
year = {2003},
date = {2003-01-15},
urldate = {1000-01-01},
booktitle = {SPIE Multimedia Computing and Networking (MMCN 2003)},
address = {Santa Clara, CA, USA},
abstract = {<p>Widespread availability of high-speed networks and fast, cheap computation have rendered high-quality Media-on-Demand (MoD) feasible. Research on scalable MoD has resulted in many efficient schemes that involve segmentation and asynchronous broadcast of media data, requiring clients to buffer and reorder out-of-order segments efficiently for serial playout.</p><p>In such schemes, buffer space requirements run to several hundred megabytes and hence require efficient buffer management techniques involving both primary memory and secondary storage: while disk sizes have increased exponentially, access speeds have not kept pace at all.</p><p>The conversion of out-of-order arrival to in-order playout suggests the use of external memory priority queues, but their content-agnostic nature prevents them from performing well under MoD loads. In this paper, we propose and evaluate a series of simple heuristic schemes which, in simulation studies and in combination with our scalable MoD scheme, achieve significant improvements in storage performance over existing schemes.</p>},
keywords = {Multicast, Video-on-Demand},
pubstate = {published},
tppubtype = {inproceedings}
}
Subhash Suri; Marcel Waldvogel; Daniel Bauer; Priyank Ramesh Warkhede
Profile-Based Routing and Traffic Engineering Journal Article
In: Computer Communications, vol. 26, no. 4, pp. 351–365, 2003.
Abstract | BibTeX | Tags: Quality of Service, Traffic Engineering | Links:
@article{Suri2003Profile-Based,
title = {Profile-Based Routing and Traffic Engineering},
author = {Subhash Suri and Marcel Waldvogel and Daniel Bauer and Priyank Ramesh Warkhede},
url = {https://netfuture.ch/wp-content/uploads/2003/suri03profilebased.pdf},
year = {2003},
date = {2003-01-01},
urldate = {1000-01-01},
journal = {Computer Communications},
volume = {26},
number = {4},
pages = {351--365},
abstract = { We present a new algorithm and framework for dynamic routing of bandwidth-guaranteed flows. The problem is motivated by the need to set up bandwidth-guaranteed paths in carrier and ISP networks dynamically. Traditional routing algorithms such as minimum-hop or widest-path routing do not take advantage of any knowledge about the traffic distribution or ingress-egress pairs, and therefore can often lead to severe network underutilization. Our work is inspired by the recently proposed "minimum interference routing" algorithm (MIRA) of Kodialam and Lakshman, but it improves on their approach in several ways. Our main idea is to use a "traffic profile" of the network, obtained by measurements or service-level agreements as a rough predictor of the future traffic distribution. We use this profile to solve a multi-commodity network flow problem, whose output is used both to guide our online path-selection algorithm as well as to impose admission control. The offline multi-commodity solution seems very effective at distributing the routes and avoiding bottlenecks around hot spots. In particular, our algorithm can anticipate a flow's blocking effect on groups of ingress-egress pairs, whereas MIRA only considers one ingress-egress pair at a time. Our simulation results show that the new algorithm outperforms shortest-path, widest-path, and minimum interference routing algorithms on several metrics, including the fraction of requests routed and the fraction of requested bandwidth routed. Finally, the framework is quite general and can be extended in numerous ways to accommodate a variety of traffic management priorities in the network.},
keywords = {Quality of Service, Traffic Engineering},
pubstate = {published},
tppubtype = {article}
}
Marcel Waldvogel; Roberto Rinaldi
Efficient Topology-Aware Overlay Network Journal Article
In: ACM Computer Communications Review, vol. 33, no. 1, pp. 101-106, 2003, (Proceedings of ACM HotNets-I (October 2002)).
BibTeX | Tags: Fast Routers, Peer-to-Peer, Traffic Engineering
@article{Waldvogel2003Efficienta,
title = {Efficient Topology-Aware Overlay Network},
author = {Marcel Waldvogel and Roberto Rinaldi},
year = {2003},
date = {2003-01-01},
urldate = {1000-01-01},
journal = {ACM Computer Communications Review},
volume = {33},
number = {1},
pages = {101-106},
note = {Proceedings of ACM HotNets-I (October 2002)},
keywords = {Fast Routers, Peer-to-Peer, Traffic Engineering},
pubstate = {published},
tppubtype = {article}
}
James Allen; Brian Bass; Claude Basso; Rick Boivie; Jean Calvignac; Gordon Davis; Laurent Freléchoux; Marco Heddes; Andreas Herkersdorf; Andreas Kind; Joe Logan; Mohammad Peyravian; Mark Rinaldi; Ravi Sabhikhi; Michael Siegel; Marcel Waldvogel
IBM PowerNP Network Processor: Hardware Software and Applications Journal Article
In: IBM Journal of Research and Development, vol. 47, no. 2/3, pp. 177-194, 2003.
Abstract | BibTeX | Tags: Fast Routers, Network Processors, Quality of Service | Links:
@article{Allen2003PowerNP,
title = {IBM PowerNP Network Processor: Hardware Software and Applications},
author = {James Allen and Brian Bass and Claude Basso and Rick Boivie and Jean Calvignac and Gordon Davis and Laurent Freléchoux and Marco Heddes and Andreas Herkersdorf and Andreas Kind and Joe Logan and Mohammad Peyravian and Mark Rinaldi and Ravi Sabhikhi and Michael Siegel and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2003/allen03powernp.pdf},
year = {2003},
date = {2003-01-01},
urldate = {1000-01-01},
journal = {IBM Journal of Research and Development},
volume = {47},
number = {2/3},
pages = {177-194},
abstract = {Deep packet processing is migrating to the edges of service provider networks to simplify and speed up core functions. On the other hand, the cores of such networks are migrating to the switching of high-speed traffic aggregates, e.g., using switching with dense wavelength division multiplexing (DWDM). As a result, more services will need to be performed at the edges, both on behalf of the core and end users. Associated network equipment will therefore require high flexibility to support evolving high-level services as well as extraordinary performance to deal with the high packet rates. Whereas in the past network equipment were based either on general-purpose processors (GPPs) or application-specific integrated circuits (ASICs), favoring flexibility over speed or vice versa, the network processor approach achieves both flexibility and performance. The key advantage of network processors is that hardware-level performance is complemented by flexible software architecture. In this paper, we describe the IBM PowerNP&tm; NP4GS3 network processor and how it addresses these issues. Its hardware and software design characteristics and its comprehensive base operating software of this network processor make it well suited for a wide range of networking applications.},
keywords = {Fast Routers, Network Processors, Quality of Service},
pubstate = {published},
tppubtype = {article}
}
Robert Haas; Clark Jeffries; Lukas Kencl; Andreas Kind; Bernard Metzler; Roman Pletka; Marcel Waldvogel; Laurent Freléchoux; Patrick Droz
Creating Advanced Functions on Network Processors: Experience and Perspectives Journal Article
In: IEEE Network, vol. 17, no. 4, pp. 46-54, 2003.
Abstract | BibTeX | Tags: Active Networks, Network Processors, Quality of Service, Replication | Links:
@article{Haas2003Creating,
title = {Creating Advanced Functions on Network Processors: Experience and Perspectives},
author = {Robert Haas and Clark Jeffries and Lukas Kencl and Andreas Kind and Bernard Metzler and Roman Pletka and Marcel Waldvogel and Laurent Freléchoux and Patrick Droz},
url = {https://netfuture.ch/wp-content/uploads/2003/haas03creating.pdf},
year = {2003},
date = {2003-01-01},
urldate = {1000-01-01},
journal = {IEEE Network},
volume = {17},
number = {4},
pages = {46-54},
abstract = {In this paper, we present five case studies of advanced networking functions that detail how a network processor (NP) can provide high performance and also the necessary flexibility compared with Application-Specific Integrated Circuits (ASICs). We first review the basic NP system architectures, and describe the IBM PowerNP architecture from a data-plane as well as from a control-plane point of view. We introduce models for the programmer's views of NPs that facilitate a global understanding of NP software programming. Then, for each case study, we present results from prototypes as well as general considerations that apply to a wider range of system architectures. Specifically, we investigate the suitability of NPs for<ul><li>Quality of Service (active queue management and traffic engineering),</li><li>header processing (GPRS tunneling protocol),</li><li>intelligent forwarding (load balancing without flow disruption),</li><li>payload processing (code interpretation and just-in-time compilation in active networks), and protocol stack termination (SCTP).</li></ul>Finally, we summarize the key features as revealed by each case study, and conclude with remarks on the future of NPs.},
keywords = {Active Networks, Network Processors, Quality of Service, Replication},
pubstate = {published},
tppubtype = {article}
}
- Quality of Service (active queue management and traffic engineering),
- header processing (GPRS tunneling protocol),
- intelligent forwarding (load balancing without flow disruption),
- payload processing (code interpretation and just-in-time compilation in active networks), and protocol stack termination (SCTP).
Ramaprabhu Janakiraman; Marcel Waldvogel; Qi Zhang
Indra: A Peer-to-Peer Approach to Network Intrusion Detection and Prevention Proceedings Article
In: Proceedings of IEEE WETICE 2003, Linz, Austria, 2003.
Abstract | BibTeX | Tags: Denial of Service, Security, Trust | Links:
@inproceedings{Janakiraman2003Indra,
title = {Indra: A Peer-to-Peer Approach to Network Intrusion Detection and Prevention},
author = {Ramaprabhu Janakiraman and Marcel Waldvogel and Qi Zhang},
url = {https://netfuture.ch/wp-content/uploads/2003/janakiraman03indra.pdf},
year = {2003},
date = {2003-01-01},
urldate = {1000-01-01},
booktitle = {Proceedings of IEEE WETICE 2003},
address = {Linz, Austria},
abstract = {While the spread of the Internet has made the network ubiquitous, it has also rendered networked systems vulnerable to malicious attacks orchestrated from anywhere. These attacks or intrusions typically start with attackers infiltrating a network through a vulnerable host and then launching further attacks on the local network or Intranet. Attackers rely on increasingly sophisticated techniques like using distributed attack sources and obfuscating their network addresses. On the other hand, software that guards against them remains rooted in traditional centralized techniques, presenting an easily-targeted single point of failure. Scalable, distributed network intrusion prevention techniques are sorely needed. We propose Indra---a distributed scheme based on sharing information between trusted peers in a network to guard the network as a whole against intrusion attempts. We present initial ideas for running Indra over a peer-to-peer infrastructure to distribute up-to-date rumors, facts, and trust information in a scalable way.},
keywords = {Denial of Service, Security, Trust},
pubstate = {published},
tppubtype = {inproceedings}
}
Roman Pletka; Andreas Kind; Marcel Waldvogel; Soenke Mannal
Closed-Loop Congestion Control for Mixed Responsive and Non-Responsive Traffic Proceedings Article
In: Proceedings of Globecom 2003, 2003.
Abstract | BibTeX | Tags: Control Engineering, Fast Routers, Traffic Engineering | Links:
@inproceedings{Pletka2003Closed-Loop,
title = {Closed-Loop Congestion Control for Mixed Responsive and Non-Responsive Traffic},
author = {Roman Pletka and Andreas Kind and Marcel Waldvogel and Soenke Mannal},
url = {https://netfuture.ch/wp-content/uploads/2003/pletka03closedloop.pdf},
year = {2003},
date = {2003-01-01},
urldate = {1000-01-01},
booktitle = {Proceedings of Globecom 2003},
abstract = {Today's known and widely used active queue management (AQM) schemes do not differentiate between packets from responsive (e.g., TCP sessions) and non-responsive traffic (e.g., UDP). This results in further widening the gap of unfair advantage already inherent to non-responsive traffic, as the responsive sender will significantly reduce its future transmit rate as a result of the congestion signals. As a simple work-around, responsive and non-responsive traffic are often assigned distinct AQM parameters. This approach however requires tuning for each traffic class that potentially depends on the current or expected offered load. In other words, responsiveness and TCP-friendliness cannot be estimated easily—not at last due to short-lived TCP sessions. In this paper we propose a closed-loop congestion control (CLCC) scheme on top of an existing AQM scheme to achieve fair bandwidth distribution among concurrent responsive and non-responsive traffic. The new scheme has the advantage that it does not need to estimate the level of responsiveness of traffic. We analyze our scheme on top of an existing rate-based AQM scheme known to approximate max-min fairness, and by means of simulations show that our extension significantly improves fair bandwidth allocation for responsive and non-responsive traffic. The simulation results have been verified with a prototype implementation on the IBM PowerNP 4GS3 network processor.},
keywords = {Control Engineering, Fast Routers, Traffic Engineering},
pubstate = {published},
tppubtype = {inproceedings}
}

2002
Marcel Waldvogel; Roberto Rinaldi
Efficient Topology-Aware Overlay Network Proceedings Article
In: Proceedings of ACM HotNets-I, 2002.
Abstract | BibTeX | Tags: Peer-to-Peer | Links:
@inproceedings{Waldvogel2002Efficient,
title = {Efficient Topology-Aware Overlay Network},
author = {Marcel Waldvogel and Roberto Rinaldi},
url = {https://netfuture.ch/wp-content/uploads/2003/waldvogel03efficient.pdf},
year = {2002},
date = {2002-10-01},
urldate = {1000-01-01},
booktitle = {Proceedings of ACM HotNets-I},
abstract = {Peer-to-peer (P2P) networking has become a household word in the past few years, being marketed as a work-around for server scalability problems and ``wonder drug'' to achieve resilience. Current widely-used P2P networks rely on central directory servers or massive message flooding, clearly not scalable solutions. Distributed Hash Tables (DHT) are expected to eliminate flooding and central servers, but can require many long-haul message deliveries. We introduce Mithos, an content-addressable overlay network that only uses minimal routing information and is directly suitable as an underlay network for P2P systems, both using traditional and DHT addressing. Unlike other schemes, it also efficiently provides locality-aware connectivity, thereby ensuring that a message reaches its destination with minimal overhead. Mithos provides for highly efficient forwarding, making it suitable for use in high-throughput applications. Paired with its ability to have addresses directly mapped into a subspace of the IPv6 address space, it provides a potential candidate for native deployment. Additionally, Mithos can be used to support third-party triangulation to quickly select a close-by replica of data or services.},
keywords = {Peer-to-Peer},
pubstate = {published},
tppubtype = {inproceedings}
}

Ramaprabhu Janakiraman; Marcel Waldvogel; Lihao Xu
Fuzzycast: Efficient Video-on-Demand over Multicast Proceedings Article
In: Proceedings of INFOCOM, pp. 920-929, New York, NY, USA, 2002.
Abstract | BibTeX | Tags: Multicast, Video-on-Demand | Links:
@inproceedings{Janakiraman2002Fuzzycast:,
title = {Fuzzycast: Efficient Video-on-Demand over Multicast},
author = {Ramaprabhu Janakiraman and Marcel Waldvogel and Lihao Xu},
url = {https://netfuture.ch/wp-content/uploads/2002/janakiraman02fuzzycast.pdf},
year = {2002},
date = {2002-06-01},
urldate = {1000-01-01},
booktitle = {Proceedings of INFOCOM},
pages = {920-929},
address = {New York, NY, USA},
abstract = { Server bandwidth has been identified as a major bottleneck in large Video-on-Demand (VoD) systems. Using multicast delivery to serve popular content helps increase scalability by making efficient use of server bandwidth. In addition, recent research has focused on proactive schemes in which the server periodically multicasts popular content without explicit requests from clients. Proactive schemes are attractive because they consume bounded server bandwidth irrespective of client arrival rate. In this work, we describe Fuzzycast, a scalable periodic multicast scheme that uses simple techniques to provide video on demand at reasonable client start-up times while consuming optimal server bandwidth. We present a theoretical analysis of its bandwidth and client buffer requirements and prove its optimality. We study the effect of variable bitrate (VBR) media on Fuzzycast performance and propose a simple extension to transmit VBR media over constant rate channels. Finally, we solve the problem of partitioning a transmission over multiple multicast groups by considering it as a specific instance of a more widely encountered resource trade-off. },
keywords = {Multicast, Video-on-Demand},
pubstate = {published},
tppubtype = {inproceedings}
}
Samphel Norden; Marcel Waldvogel
Imprecise Multicast Routing for Scalable Information Distribution Proceedings Article
In: Proceedings of International Zurich Seminar (IZS) 2002, pp. 14-1 – 14-6, Zurich, Switzerland, 2002.
Abstract | BibTeX | Tags: Bloom Filters, Fast Routers, Multicast | Links:
@inproceedings{Norden2002Imprecise,
title = {Imprecise Multicast Routing for Scalable Information Distribution},
author = {Samphel Norden and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2002/norden02imprecise.pdf},
year = {2002},
date = {2002-02-01},
urldate = {1000-01-01},
booktitle = {Proceedings of International Zurich Seminar (IZS) 2002},
pages = {14-1 -- 14-6},
address = {Zurich, Switzerland},
abstract = {Typically, multicast data distribution uses rendezvous points (PIM, CBT), multicast distribution tree building protocols, and multicast forwarding. Whereas the first two approaches have been extensively studied, scaling multicast forwarding state without increasing forwarding complexity has not been addressed in detail. Having a scalable strategy for aggregation of multicast forwarding state is essential for inter-domain multicast which could have any number of concurrent multicast groups, especially in applications such as event notification and web cache invalidation mechanisms. We first present the essential characteristics of a scalable multicast routing mechanism. We then introduce and analyze, according to these metrics, a scalable aggregation mechanism for multicast-based update and change distribution based on imprecise (too generous) aggregation. Our mechanism is simple to implement, requires no additional information about the groups, and allows important savings in routing table size and routing protocol overhead, at a minimal expense in additional network and end-system traffic.},
keywords = {Bloom Filters, Fast Routers, Multicast},
pubstate = {published},
tppubtype = {inproceedings}
}
Florian Braun; John Lockwood; Marcel Waldvogel
Protocol Wrappers for Layered Network Packet Processing in Reconfigurable Networks Journal Article
In: IEEE Micro, vol. 22, no. 1, pp. 66-74, 2002.
Abstract | BibTeX | Tags: Fast Routers, FPGA | Links:
@article{Braun2002Protocol,
title = {Protocol Wrappers for Layered Network Packet Processing in Reconfigurable Networks},
author = {Florian Braun and John Lockwood and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2002/braun02protocol.pdf},
year = {2002},
date = {2002-01-01},
urldate = {1000-01-01},
journal = {IEEE Micro},
volume = {22},
number = {1},
pages = {66-74},
abstract = { A library of layered protocol wrappers has been developed that process Internet packets in reconfigurable hardware. These wrappers can be used with a reprogrammable network platform called the Field Programmable Port Extender (FPX) to rapidly prototype hardware circuits for processing Internet packets. We present a framework to streamline and simplify the development of networking applications that process ATM cells, AAL5 frames, Internet Protocol (IP) packets and UDP datagrams directly in hardware.},
keywords = {Fast Routers, FPGA},
pubstate = {published},
tppubtype = {article}
}
Roberto Rinaldi; Marcel Waldvogel
Routing and Data Location in Overlay Peer-to-Peer Networks Technical Report
IBM no. RZ-3433, 2002.
Abstract | BibTeX | Tags: Fast Routers, Peer-to-Peer | Links:
@techreport{Rinaldi2002Routing-techreport,
title = {Routing and Data Location in Overlay Peer-to-Peer Networks},
author = {Roberto Rinaldi and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2002/waldvogel02topology-techreport.pdf},
year = {2002},
date = {2002-01-01},
urldate = {1000-01-01},
number = {RZ-3433},
institution = {IBM},
abstract = {Peer-to-peer (P2P) networking has become a household word in the past few years, being marketed as a work-around for server scalability problems and “wonder drug” to achieve resilience. Current widely-used P2P networks rely on central directory servers or massive message flooding, clearly not scalable solutions. Distributed Hash Tables (DHT) are expected to eliminate flooding and central servers, but can require many long-haul message deliveries. We introduce Mithos, an overlay network that only uses minimal routing information and is directly suitable for normal and DHT addressing. Unlike other schemes, it also efficiently provides locality-aware connectivity, thereby ensuring that a message reaches its destination with minimal overhead and highly efficient forwarding. The service can in addition be used to support third-party triangulation to point to close replicas of data or services. Its addressing can be mapped directly into a subspace of the IPv6 addresses.},
keywords = {Fast Routers, Peer-to-Peer},
pubstate = {published},
tppubtype = {techreport}
}

Subhash Suri; Marcel Waldvogel; Daniel Bauer; Priyank Ramesh Warkhede
Profile-Based Routing and Traffic Engineering Technical Report
IBM no. RZ-3399, 2002.
BibTeX | Tags: Quality of Service, Traffic Engineering
@techreport{Suri2002Profile-Based-techreport,
title = {Profile-Based Routing and Traffic Engineering},
author = {Subhash Suri and Marcel Waldvogel and Daniel Bauer and Priyank Ramesh Warkhede},
year = {2002},
date = {2002-01-01},
urldate = {1000-01-01},
number = {RZ-3399},
institution = {IBM},
keywords = {Quality of Service, Traffic Engineering},
pubstate = {published},
tppubtype = {techreport}
}

Marcel Waldvogel
GOSSIB vs. IP Traceback Rumors Proceedings Article
In: 18th Annual Computer Security Applications Conference (ACSAC 2002), pp. 5–13, 2002.
Abstract | BibTeX | Tags: Denial of Service, Security | Links:
@inproceedings{Waldvogel2002GOSSIB,
title = {GOSSIB vs. IP Traceback Rumors},
author = {Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2002/waldvogel02gossib.pdf},
year = {2002},
date = {2002-01-01},
urldate = {1000-01-01},
booktitle = {18th Annual Computer Security Applications Conference (ACSAC 2002)},
pages = {5--13},
abstract = { To identify sources of distributed denial-of-service attacks, path traceback mechanisms have been proposed. Traceback mechanisms relying on probabilistic packet marking (PPM) have received most attention, as they are easy to implement and deploy incrementally. In this paper, we introduce a new concept, namely groups of strongly similar birthdays (GOSSIB), that can be used by to obtain effects similar to a successful birthday attack on PPM schemes. The original and most widely known IP traceback mechanism, compressed edge fragment sampling (CEFS), was developed by Savage et al. We analyze the effects of an attacker using GOSSIB against CEFS and show that the attacker can seed misinformation much more effiently than the network is able to contribute real traceback information. Thus, GOSSIB will render PPM effctively useless. It can be expected that GOSSIB has similar effcts on other PPM traceback schemes and that standard modifiations to the systems will not solve the problem.},
keywords = {Denial of Service, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
Marcel Waldvogel; Roberto Rinaldi
Efficient Topology-Aware Overlay Network Technical Report
IBM no. RZ-3436, 2002.
BibTeX | Tags: Fast Routers, Peer-to-Peer
@techreport{Waldvogel2002Efficient-techreport,
title = {Efficient Topology-Aware Overlay Network},
author = {Marcel Waldvogel and Roberto Rinaldi},
year = {2002},
date = {2002-01-01},
urldate = {1000-01-01},
number = {RZ-3436},
institution = {IBM},
keywords = {Fast Routers, Peer-to-Peer},
pubstate = {published},
tppubtype = {techreport}
}

Ken Christensen; Marcel Waldvogel
Issues and Trends in Terabit Switching Journal Article
In: Computer Communications, vol. 25, no. 6, pp. 545–546, 2002.
Abstract | BibTeX | Tags: Fast Routers | Links:
@article{Christensen2002Issues,
title = {Issues and Trends in Terabit Switching},
author = {Ken Christensen and Marcel Waldvogel},
url = {http://www.sciencedirect.com/science/journal/01403664/25/6},
year = {2002},
date = {2002-01-01},
urldate = {1000-01-01},
journal = {Computer Communications},
volume = {25},
number = {6},
pages = {545--546},
abstract = {Terabit-per-second switches and routers are already beginning to be commercially available. However, numerous issues still exist in the design of very high-speed switches. Link speeds are now approaching, and exceeding, memory bandwidths, complicating buffer designs. In addition to very high-speed links and large switching capacities, future high-speed switches are expected to be able to support multiple classes of traffic with varying Quality-of-Service (QoS) requirements. This includes traffic classes with guaranteed throughput and bounded delay requirements. Input buffered architectures are being used to deal with memory bandwidth bottlenecks. New challenges arise in switch-matrix and flow-level scheduling. Challenges remain in packet classification. Multistage switching fabrics are being revisited. Network processors are opening new opportunities for supporting high-level capabilities including traffic management. In addition, standardization efforts for switch fabric interfaces are ongoing. Overall, this is an exciting time for switch developers and researchers.},
keywords = {Fast Routers},
pubstate = {published},
tppubtype = {article}
}
2001
Samphel Norden; Milind M. Buddhikot; Marcel Waldvogel; Subhash Suri
Routing Bandwidth Guaranteed Paths with Restoration in Label Switched Networks Proceedings Article
In: Proceedings of IEEE International Conference on Network Protocols (ICNP 2001), pp. 71-79, Riverside, CA, USA, 2001.
Abstract | BibTeX | Tags: Traffic Engineering | Links:
@inproceedings{Norden2001Routing,
title = {Routing Bandwidth Guaranteed Paths with Restoration in Label Switched Networks},
author = {Samphel Norden and Milind M. Buddhikot and Marcel Waldvogel and Subhash Suri},
url = {https://netfuture.ch/wp-content/uploads/2001/norden01routing.pdf},
year = {2001},
date = {2001-11-01},
urldate = {1000-01-01},
booktitle = {Proceedings of IEEE International Conference on Network Protocols (ICNP 2001)},
pages = {71-79},
address = {Riverside, CA, USA},
abstract = { Label switched networks have become increasingly attractive to both network providers and customers. By creating aggregate, bandwidth-reserved flows, these networks are known for their routing flexibility, predictable bandwidth usage, and quality-of-service (QoS) provisioning. This flexibility in routing enables fault-persistent QoS reservations, where connectivity and allotted bandwidth remains available, even if some links or network nodes fail. The automatic switch-over from a now-defunct path to a new, working path is known as restoration. Restoring bandwidth-guaranteed paths requires allocation of resources to be used in presence of faults, so-called backup paths. In this paper, we investigate distributed algorithms for routing with backup restoration. Specifically, we propose a new concept of Backup Load Distribution Matrix, that captures partial network state, greatly reducing the amount of routing information maintained and transmitted while achieving efficient bandwidth usage. We present and simulate two new distributed routing algorithms, which provide significant improvements in rejection rates and provide substantial savings in call setup time compared to existing algorithms.},
keywords = {Traffic Engineering},
pubstate = {published},
tppubtype = {inproceedings}
}

Subhash Suri; Marcel Waldvogel; Priyank Ramesh Warkhede
Profile-Based Routing: A New Framework for MPLS Traffic Engineering Proceedings Article
In: Boavida, Fernando (Ed.): Quality of future Internet Services, pp. 138-157, Springer Verlag, Berlin, 2001.
Abstract | BibTeX | Tags: MPLS, Quality of Service, Traffic Engineering | Links:
@inproceedings{Suri2001Profile-Based,
title = {Profile-Based Routing: A New Framework for MPLS Traffic Engineering},
author = {Subhash Suri and Marcel Waldvogel and Priyank Ramesh Warkhede},
editor = {Fernando Boavida},
url = {https://netfuture.ch/wp-content/uploads/2001/suri01profilebased.pdf},
year = {2001},
date = {2001-09-01},
urldate = {1000-01-01},
booktitle = {Quality of future Internet Services},
number = {2156},
pages = {138-157},
publisher = {Springer Verlag},
address = {Berlin},
series = {Lecture Notes in Computer Science},
abstract = { We present a new algorithm and framework for dynamic routing of bandwidth guaranteed flows. The problem is motivated by the need to dynamically set up bandwidth guaranteed paths in carrier and ISP networks. Traditional routing algorithms such as minimum hop routing or widest path routing do not take advantage of any knowledge about the traffic distribution or ingress-egress pairs, and therefore can often lead to severe network underutilization. Our work is inspired by the recently proposed ``minimum interference routing'' algorithm (MIRA) of Kodialam and Lakshman, but it improves on their approach in several ways. Our main idea is to use a ``traffic profile'' of the network, obtained by measurements or service level agreements (SLAs), as a rough predictor of the future traffic distribution. We use this profile to solve a multicommodity network flow problem, whose output is used both to guide our online path selection algorithm as well as impose admission control. The offline multicommodity solution seems very effective at distributing the routes and avoiding bottlenecks around hot spots. In particular, our algorithm can anticipate a flow's blocking effect on groups of ingress-egress pairs, while MIRA only considers one ingress-egress pair at a time. Our simulation results show that the new algorithm outperforms shortest path, widest path, and minimum interference routing algorithms on several metrics, including the fraction of requests routed and the fraction of requested bandwidth routed. Finally, the framework is quite general and can be extended in numerous ways to accommodate a variety of traffic management priorities in the network. },
keywords = {MPLS, Quality of Service, Traffic Engineering},
pubstate = {published},
tppubtype = {inproceedings}
}

Florian Braun; John Lockwood; Marcel Waldvogel
Layered Protocol Wrappers for Internet Packet Processing in Reconfigurable Hardware Proceedings Article
In: Proceedings of IEEE Hot Interconnects 9, Stanford, CA, USA, 2001.
Abstract | BibTeX | Tags: Fast Routers, FPGA | Links:
@inproceedings{Braun2001Layered,
title = {Layered Protocol Wrappers for Internet Packet Processing in Reconfigurable Hardware},
author = {Florian Braun and John Lockwood and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2001/braun01layered.pdf},
year = {2001},
date = {2001-08-01},
urldate = {1000-01-01},
booktitle = {Proceedings of IEEE Hot Interconnects 9},
address = {Stanford, CA, USA},
abstract = { A library of layered protocol wrappers has been developed that process Internet packets in reconfigurable hardware. These wrappers can be used with a reprogrammable network platform called the Field Programmable Port Extender (FPX) to rapidly prototype hardware circuits for processing Internet packets. We present a framework to streamline and simplify the development of networking applications that process ATM cells, AAL5 frames, Internet Protocol (IP) packets and UDP datagrams directly in hardware.},
keywords = {Fast Routers, FPGA},
pubstate = {published},
tppubtype = {inproceedings}
}

Marcel Waldvogel; George Varghese; Jon Turner; Bernhard Plattner
Scalable High-Speed Prefix Matching Journal Article
In: Transaction on Computer Systems, vol. 19, no. 4, pp. 440-482, 2001.
Abstract | BibTeX | Tags: Fast Routers, Hash Tables | Links:
@article{Waldvogel2001Scalable,
title = {Scalable High-Speed Prefix Matching},
author = {Marcel Waldvogel and George Varghese and Jon Turner and Bernhard Plattner},
url = {https://netfuture.ch/wp-content/uploads/2001/waldvogel01scalable.pdf},
year = {2001},
date = {2001-06-21},
urldate = {1000-01-01},
journal = {Transaction on Computer Systems},
volume = {19},
number = {4},
pages = {440-482},
abstract = {Finding the longest matching prefix from a database of keywords is an old problem with a number of applications, ranging from dictionary searches to advanced memory management to computational geometry. But perhaps today's most frequent best matching prefix lookups occur in the Internet, when forwarding packets from router to router. Internet traffic volume and link speeds are rapidly increasing; at the same time, a growing user population is increasing the size of routing tables against which packets must be matched. Both factors make router prefix matching extremely performance critical.In this paper, we introduce a taxonomy for prefix matching technologies, which we use as a basis for describing, categorizing, and comparing existing approaches. We then present in detail a fast scheme using binary search over hash tables, which is especially suited for matching long addresses, such as the 128 bit addresses proposed for use in the next generation Internet Protocol, IPv6. We also present optimizations that exploit the structure of existing databases to further improve access time and reduce storage space.},
keywords = {Fast Routers, Hash Tables},
pubstate = {published},
tppubtype = {article}
}
Dimitris Pendarakis; Sherlia Shi; Dinesh Verma; Marcel Waldvogel
ALMI: An Application Level Multicast Infrastructure Proceedings Article
In: Proceedings of the 3rd USENIX Symposium on Internet Technologies and Systems (USITS ’01), pp. 49-60, San Francisco, CA, USA, 2001.
Abstract | BibTeX | Tags: Multicast, Peer-to-Peer | Links:
@inproceedings{Pendarakis2001ALMI,
title = {ALMI: An Application Level Multicast Infrastructure},
author = {Dimitris Pendarakis and Sherlia Shi and Dinesh Verma and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2001/pendarakis01almi.pdf},
year = {2001},
date = {2001-03-01},
urldate = {1000-01-01},
booktitle = {Proceedings of the 3rd USENIX Symposium on Internet Technologies and Systems (USITS '01)},
pages = {49-60},
address = {San Francisco, CA, USA},
abstract = {The IP multicast model allows scalable and efficient multi-party communication, particularly for groups of large size. However, deployment of IP multicast requires substantial infrastructure modifications and is hampered by a host of unresolved open problems. To circumvent this situation, we have designed and implemented ALMI, an application level group communication middleware, which allows accelerated application deployment and simplified network configuration, without the need of network infrastructure support. ALMI is tailored toward support of multicast groups of relatively small size (several 10s of members) with many to many semantics. Session participants are connected via a virtual multicast tree, which consists of unicast connections between end hosts and is formed as a minimum spanning tree (MST) using application-specific performance metric. Using simulation, we show that the performance penalties, introduced by this shift of multicast to end systems, is a relatively small increase in traffic load and that ALMI multicast trees approach the efficiency of IP multicast trees. We have also implemented ALMI as a Java based middleware package and performed experiments over the Internet. Experimental results show that ALMI is able to cope with network dynamics and keep the multicast tree efficient. },
keywords = {Multicast, Peer-to-Peer},
pubstate = {published},
tppubtype = {inproceedings}
}
Florian Braun; John Lockwood; Marcel Waldvogel
Layered Protocol Wrappers for Internet Packet Processing in Reconfigurable Hardware Technical Report
Washington University in St. Louis no. WUCS-01-10, 2001.
BibTeX | Tags: Fast Routers, FPGA
@techreport{Braun2001Layered-techreport,
title = {Layered Protocol Wrappers for Internet Packet Processing in Reconfigurable Hardware},
author = {Florian Braun and John Lockwood and Marcel Waldvogel},
year = {2001},
date = {2001-01-01},
urldate = {1000-01-01},
number = {WUCS-01-10},
institution = {Washington University in St. Louis},
keywords = {Fast Routers, FPGA},
pubstate = {published},
tppubtype = {techreport}
}
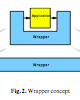
Florian Braun; John Lockwood; Marcel Waldvogel
Reconfigurable Router Modules Using Network Protocol Wrappers Proceedings Article
In: Field-Programmable Logic and Applications (FPL), pp. 254–263, Belfast, Northern Ireland, 2001.
Abstract | BibTeX | Tags: Fast Routers, FPGA | Links:
@inproceedings{Braun2001Reconfigurable,
title = {Reconfigurable Router Modules Using Network Protocol Wrappers},
author = {Florian Braun and John Lockwood and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2001/braun01reconfigurable.pdf},
year = {2001},
date = {2001-01-01},
urldate = {1000-01-01},
booktitle = {Field-Programmable Logic and Applications (FPL)},
pages = {254--263},
address = {Belfast, Northern Ireland},
abstract = { A library of layered protocol wrappers has been developed that process Internet packets in reconfigurable hardware. These wrappers can be used with a reprogrammable network platform called the Field Programmable Port Extender (FPX) to rapidly prototype hardware circuits for processing Internet packets. We present a framework to streamline and simplify the development of networking applications that process ATM cells, AAL5 frames, Internet Protocol (IP) packets and UDP datagrams directly in hardware. },
keywords = {Fast Routers, FPGA},
pubstate = {published},
tppubtype = {inproceedings}
}

Florian Braun; Marcel Waldvogel
Fast Incremental CRC Updates for IP over ATM networks Proceedings Article
In: Proceedings of 2001 IEEE Workshop on High Performance Switching and Routing (HPSR 2001), Dallas, TX, USA, 2001.
Abstract | BibTeX | Tags: CRC, Fast Routers | Links:
@inproceedings{Braun2001Fast,
title = {Fast Incremental CRC Updates for IP over ATM networks},
author = {Florian Braun and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2001/braun01fast.pdf},
year = {2001},
date = {2001-01-01},
urldate = {1000-01-01},
booktitle = {Proceedings of 2001 IEEE Workshop on High Performance Switching and Routing (HPSR 2001)},
address = {Dallas, TX, USA},
abstract = {In response to the increasing network speeds, many operations in IP routers and similar devices are being made more efficient. With the advances in other areas of packet processing, the verification and regeneration of cyclic redundancy check (CRC) codes of the data link layer is likely to become a bottleneck in the near future. In this paper, we present a mechanism to defer CRC verification without compromising reliability. This opens the possibility of incremental updates of the CRC. We introduce a new high-speed technique and present efficient implementations, speeding up CRC processing by a factor of 15. Although the paper and analysis focuses on IP over ATM, the scheme applies to a much wider set of network protocols.},
keywords = {CRC, Fast Routers},
pubstate = {published},
tppubtype = {inproceedings}
}
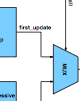
Florian Braun; Marcel Waldvogel
Fast Incremental CRC Updates for IP over ATM networks Technical Report
Washington University in St. Louis no. WUCS-01-08, 2001.
BibTeX | Tags: CRC, Fast Routers
@techreport{Braun2001Fast-techreport,
title = {Fast Incremental CRC Updates for IP over ATM networks},
author = {Florian Braun and Marcel Waldvogel},
year = {2001},
date = {2001-01-01},
urldate = {1000-01-01},
number = {WUCS-01-08},
institution = {Washington University in St. Louis},
keywords = {CRC, Fast Routers},
pubstate = {published},
tppubtype = {techreport}
}

Florian Braun; Marcel Waldvogel; John Lockwood
OBIWAN — An Internet Protocol Router in Reconfigurable Hardware Technical Report
Washington University in St. Louis no. WU-CS-01-11, 2001.
BibTeX | Tags: Fast Routers, FPGA
@techreport{Braun2001OBIWAN-techreport,
title = {OBIWAN -- An Internet Protocol Router in Reconfigurable Hardware},
author = {Florian Braun and Marcel Waldvogel and John Lockwood},
year = {2001},
date = {2001-01-01},
urldate = {1000-01-01},
number = {WU-CS-01-11},
institution = {Washington University in St. Louis},
keywords = {Fast Routers, FPGA},
pubstate = {published},
tppubtype = {techreport}
}
Sherlia Shi; Jon Turner; Marcel Waldvogel
Dimensioning Server Access Bandwidth and Multicast Routing in Overlay Networks Proceedings Article
In: Prceedings of NOSSDAV 2001, pp. 83-92, 2001.
Abstract | BibTeX | Tags: Multicast, Traffic Engineering | Links:
@inproceedings{Shi2001Dimensioning,
title = {Dimensioning Server Access Bandwidth and Multicast Routing in Overlay Networks},
author = {Sherlia Shi and Jon Turner and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2001/shi01dimensioning.pdf},
year = {2001},
date = {2001-01-01},
urldate = {1000-01-01},
booktitle = {Prceedings of NOSSDAV 2001},
pages = {83-92},
abstract = { Application-level multicast is a new mechanism for enabling multicast in the Internet. Driven by the fast growth of network audio/video streams, application-level multicast has become increasingly important for its efficiency of data delivery and its ability of providing value-added services to satisfy application specific requirements. From a network design perspective, application-level multicast differs drastically from traditional IP multicast in its network cost model and routing strategies. We present these differences and formulate them as a network design problem consisting of two parts: one is bandwidth assignment in the overlay network, the other is load-balancing multicast routing with delay constraints. We use analytical methods and simulations to show that our design solution is a valid and cost-effective approach. Simulation results show that we are able to achieve network utilization within 10% of the best possible utilization while keeping the session rejection rate low.},
keywords = {Multicast, Traffic Engineering},
pubstate = {published},
tppubtype = {inproceedings}
}
Marcel Waldvogel; Wei Deng; Ramaprabhu Janakiraman
Fuzzycast: Media Broadcasting for Multiple Asynchronous Receivers Technical Report
Washington University in St. Louis, Missouri, USA no. WUCS-01-02, 2001.
BibTeX | Tags: Multicast, Video-on-Demand
@techreport{Waldvogel2001Media-techreport,
title = {Fuzzycast: Media Broadcasting for Multiple Asynchronous Receivers},
author = {Marcel Waldvogel and Wei Deng and Ramaprabhu Janakiraman},
year = {2001},
date = {2001-01-01},
urldate = {1000-01-01},
number = {WUCS-01-02},
institution = {Washington University in St. Louis, Missouri, USA},
keywords = {Multicast, Video-on-Demand},
pubstate = {published},
tppubtype = {techreport}
}
Marcel Waldvogel; Ramaprabhu Janakiraman
Efficient Media-on-demand over Multiple Multicast Groups Proceedings Article
In: Proceedings of Globecom 2001, San Antonio, Texas, USA, 2001.
Abstract | BibTeX | Tags: Multicast, Video-on-Demand | Links:
@inproceedings{Waldvogel2001Efficient,
title = {Efficient Media-on-demand over Multiple Multicast Groups},
author = {Marcel Waldvogel and Ramaprabhu Janakiraman},
url = {https://netfuture.ch/wp-content/uploads/2004/norden04routing1.pdf},
year = {2001},
date = {2001-01-01},
urldate = {1000-01-01},
booktitle = {Proceedings of Globecom 2001},
address = {San Antonio, Texas, USA},
abstract = { Using multicast for serving popular movies on demand reduces load on the server and the network by eliminating redundant packet transmission. To permit clients to arrive at times of their choosing, periodic rebroadcast is necessary. In addition, splitting the transmission over multiple multicast groups reduces the cost of rebroadcasting by allowing clients to unsubscribe from groups in which they are no longer interested.</p><p>The focus of this paper is to develop techniques for efficient Media-on-Demand delivery to asynchronous clients over multiple multicast groups. We start by describing an existing periodic multicast technique that is near-optimal in terms of server bandwidth. Given a small number of groups $alpha$, we then show how to distribute content over these groups in a way that minimizes network impact. We present a theoretical analysis of the performance gains and compare these predictions with simulations over real and generated network topologies. We find that using even a small number of multicast groups provides significant reduction in overall network bandwidth.},
keywords = {Multicast, Video-on-Demand},
pubstate = {published},
tppubtype = {inproceedings}
}

Marcel Waldvogel; Ramaprabhu Janakiraman; Wei Deng
Fuzzycast: Media Broadcasting for Multiple Asynchronous Receivers Technical Report
Washington University in St. Louis, Department of Computer Science 2001.
BibTeX | Tags: Multicast, Video-on-Demand
@techreport{Waldvogel2001Fuzzycast:-techreport,
title = {Fuzzycast: Media Broadcasting for Multiple Asynchronous Receivers},
author = {Marcel Waldvogel and Ramaprabhu Janakiraman and Wei Deng},
year = {2001},
date = {2001-01-01},
urldate = {1000-01-01},
institution = {Washington University in St. Louis, Department of Computer Science},
keywords = {Multicast, Video-on-Demand},
pubstate = {published},
tppubtype = {techreport}
}

Marcel Waldvogel; Radhesh Mohandas; Sherlia Shi
EKA: Efficient Keyserver using ALMI Proceedings Article
In: Proceedings of IEEE WET ICE Workshop on Enterprise Security, pp. 237-246, Cambridge, MA, USA, 2001.
Abstract | BibTeX | Tags: Multicast, Security | Links:
@inproceedings{Waldvogel2001EKA,
title = {EKA: Efficient Keyserver using ALMI},
author = {Marcel Waldvogel and Radhesh Mohandas and Sherlia Shi},
url = {https://netfuture.ch/wp-content/uploads/2001/waldvogel01eka.pdf},
year = {2001},
date = {2001-01-01},
urldate = {1000-01-01},
booktitle = {Proceedings of IEEE WET ICE Workshop on Enterprise Security},
pages = {237-246},
address = {Cambridge, MA, USA},
abstract = { The keyserver network serves as a repository of OpenPGP keys, providing replication throughout the Internet. It currently uses an inefficient and insufficient protocol to keep its nodes synchronized: highly redundant network traffic and excessive overhead due to several thousand e-mail messages per day. Under these conditions, even short network outages cause massive mail server overloads and losses, resulting in continuously diverging databases. In this paper, we present a new protocol to achieve complete synchronization efficiently and automatically, drastically reducing the need for manual intervention. Our protocol transmits only the updates and uses multicast to optimize the amount of data sent. Since support for native multicast is not widely available in the underlying network and current Internet multicast does not scale well, we base our keyserver on ALMI. ALMI is a middleware for reliable applicationlevel multicast, providing scalable join/leave notification of neighbors, significantly reducing the complexity of the application. As a part of this work, we have also implemented a keyserver software which uses our protocol and an efficient RDBMS back-end to hold the keys. },
keywords = {Multicast, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
2000
Marcel Waldvogel
Multi-Dimensional Prefix Matching Using Line Search Proceedings Article
In: Proceedings of IEEE Local Computer Networks, pp. 200-207, Tampa, FL, USA, 2000.
Abstract | BibTeX | Tags: Fast Routers, Hash Tables, Quality of Service | Links:
@inproceedings{Waldvogel2000Multi-Dimensional,
title = {Multi-Dimensional Prefix Matching Using Line Search},
author = {Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2000/waldvogel00multidimensional.pdf},
year = {2000},
date = {2000-11-01},
urldate = {1000-01-01},
booktitle = {Proceedings of IEEE Local Computer Networks},
pages = {200-207},
address = {Tampa, FL, USA},
abstract = {With the increasing popularity of firewalls, virtual private networks (VPNs) and Quality of Service (QoS) routing, packet classification becomes increasingly important in the Internet. The high-performance solutions known so far strongly rely on certain properties of the filter database to match against, such as a small number of distinct prefixes or the absence of conflicts. In this paper, we present Line Search as a two-dimensional generalization of the one-dimensional binary search on prefix lengths, exploiting the advantage given by the different approach therein. This algorithm also works best on the filter databases that are expected to occur most often, but degrades gracefully when these assumptions no longer hold. We also show how to efficiently extend the algorithm to a complete five-dimensional Internet Protocol (IP) and transport header match.},
keywords = {Fast Routers, Hash Tables, Quality of Service},
pubstate = {published},
tppubtype = {inproceedings}
}
Marcel Waldvogel
Fast Longest Prefix Matching: Algorithms, Analysis, and Applications PhD Thesis
ETH Zürich, 2000.
BibTeX | Tags: Fast Routers, FPGA
@phdthesis{Waldvogel2000Fasta,
title = {Fast Longest Prefix Matching: Algorithms, Analysis, and Applications},
author = {Marcel Waldvogel},
year = {2000},
date = {2000-05-01},
urldate = {1000-01-01},
number = {13266},
school = {ETH Zürich},
keywords = {Fast Routers, FPGA},
pubstate = {published},
tppubtype = {phdthesis}
}

Sherlia Shi; Marcel Waldvogel
A Rate-based End-to-end Multicast Congestion Control Protocol Proceedings Article
In: Proceedings of ISCC 2000, pp. 678-686, Antibes, France, 2000.
Abstract | BibTeX | Tags: Multicast, Quality of Service | Links:
@inproceedings{Shi2000Rate-based,
title = {A Rate-based End-to-end Multicast Congestion Control Protocol},
author = {Sherlia Shi and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2000/shi00ratebased.pdf},
year = {2000},
date = {2000-01-01},
urldate = {1000-01-01},
booktitle = {Proceedings of ISCC 2000},
pages = {678-686},
address = {Antibes, France},
abstract = {Current reliable multicast protocols do not have scalable congestion control mechanisms and this deficiency leads to concerns that multicast deployment may endanger stability of the network. In this paper, we present a sender-based approach for multicast congestion control targeted towards reliable bulk data transfer. We assume that there are a few bottleneck links in a large scale multicast group at any time period and these bottlenecks persist long enough to be identified and adapted to. Our work focus on dynamically identifying the worst congested path in the multicast tree and obtaining TCP-friendly throughput on this selected path. We devise novel selection (amongst receivers) and aggregation (over time) methods to achieve our goal. The response time of our protocol is then compatible to TCP once the worst path is identified. Only when switching between worst paths, the protocol response time is relaxed to multiple RTTs (less than 10) for the reasons of scalability and stability. We use the network simulator (NS2) to validate and evaluate our congestion control algorithm with both drop-tail and RED gateways. },
keywords = {Multicast, Quality of Service},
pubstate = {published},
tppubtype = {inproceedings}
}
Sherlia Shi; Marcel Waldvogel
A Rate-based End-to-end Multicast Congestion Control Protocol Technical Report
Department of Computer Science, Washington University in St. Louis no. WUCS-00-03, 2000.
BibTeX | Tags: Multicast, Quality of Service | Links:
@techreport{Shi2000Rate-based-techreport,
title = {A Rate-based End-to-end Multicast Congestion Control Protocol},
author = {Sherlia Shi and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2000/shi00ratebased-techreport.pdf},
year = {2000},
date = {2000-01-01},
urldate = {1000-01-01},
number = {WUCS-00-03},
institution = {Department of Computer Science, Washington University in St. Louis},
keywords = {Multicast, Quality of Service},
pubstate = {published},
tppubtype = {techreport}
}

Jonathan Turner; George Varghese; Marcel Waldvogel
Scalable High Speed IP Routing Lookups Miscellaneous
U.S. Patent Number 6,018,524, 2000.
BibTeX | Tags: Fast Routers, Hash Tables
@misc{Turner2000Scalable,
title = {Scalable High Speed IP Routing Lookups},
author = {Jonathan Turner and George Varghese and Marcel Waldvogel},
year = {2000},
date = {2000-01-01},
urldate = {1000-01-01},
howpublished = {U.S. Patent Number 6,018,524},
keywords = {Fast Routers, Hash Tables},
pubstate = {published},
tppubtype = {misc}
}

Marcel Waldvogel
Fast Longest Prefix Matching: Algorithms, Analysis, and Applications Book
Shaker Verlag, Aachen, Germany, 2000.
Abstract | BibTeX | Tags: Fast Routers, Hash Tables | Links:
@book{Waldvogel2000Fast,
title = {Fast Longest Prefix Matching: Algorithms, Analysis, and Applications},
author = {Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2000/waldvogel00fast.pdf},
year = {2000},
date = {2000-01-01},
urldate = {1000-01-01},
publisher = {Shaker Verlag},
address = {Aachen, Germany},
abstract = {Many current problems demand efficient best matching algorithms. Network devices alone show several applications. They need to determine a \emph{longest matching prefix} for packet routing or establishment of virtual circuits. In integrated services packet networks, packets need to be classified by trying to find the \emph{most specific match} from a large number of patterns, each possibly containing wildcards at arbitrary positions. Other areas of applications include such diverse areas as geographical information systems (GIS) and persistent databases.
We describe a class of best matching algorithms based on slicing perpendicular to the patterns and performing a modified binary search over these slices. We also analyze their complexity and performance. We then introduce schemes that allow the algorithm to ``learn'' the structure of the database and adapt itself to it. Furthermore, we show how to efficiently implement our algorithm both using general-purpose hardware and using software running on popular personal computers and workstations.
The research presented herein was originally driven by current demands in the Internet. Since the advent of the World Wide Web, the number of users, hosts, domains, and networks connected to the Internet seems to be exploding. Not surprisingly, network traffic at major exchange points is doubling every few months. The Internet is a packet network, where each data packet is passed from a router to the next in the chain, until it reaches destination. For versatility and efficient utilization of the available transmission bandwidth, each router performs its decision where to forward a packet as independent of the other routers and the other packets for the same destination as possible.
Five key factors are required to keep pace if the Internet is to continue to provide good service:
<ol>
<li>higher link speeds,</li>
<li>better router data throughput,</li>
<li>faster packet forwarding rates,</li>
<li>quick adaptation to topology and load changes, and</li>
<li>the support for Quality-of-Service (QoS).</li>
</ol>
Solutions for the first two are readily available: fiber-optic cables using wavelength-division multiplexing (WDM) and switching backplane interconnects. We present longest matching prefix techniques which help solving the other three factors. They allow for a high rate of forwarding decisions, quick updates, and can be extended to classify packets based on multiple fields.
The best known longest matching prefix solutions require memory accesses proportional to the length of the addresses. Our new algorithm uses binary search on hash tables organized by prefix lengths and scales very well as address and routing table sizes increase: independent of the table size, it requires a worst case time of log_{2}(\textit{address bits\textit{) hash lookups. Thus only 5 hash lookups are needed for the current Internet protocol version 4 (IPv4) with 32 address bits and 7 for the upcoming IPv6 with 128 address bits. We also introduce \emph{mutating binary search} and other optimizations that, operating on the largest available databases, reduce the worst case to 4 hashes and allow the majority of addresses to be found with at most 2 hashes. We expect similar improvements to hold for IPv6.
We extend these results to find the best match for a tuple of multiple fields of the packet's header, as required for QoS support. We also show the versatility of the resulting algorithms by using it for such diverse applications as geographical information systems, memory management, garbage collection, persistent object-oriented databases, keeping distributed databases synchronized, and performing web-server access control.},
keywords = {Fast Routers, Hash Tables},
pubstate = {published},
tppubtype = {book}
}
We describe a class of best matching algorithms based on slicing perpendicular to the patterns and performing a modified binary search over these slices. We also analyze their complexity and performance. We then introduce schemes that allow the algorithm to “learn” the structure of the database and adapt itself to it. Furthermore, we show how to efficiently implement our algorithm both using general-purpose hardware and using software running on popular personal computers and workstations.
The research presented herein was originally driven by current demands in the Internet. Since the advent of the World Wide Web, the number of users, hosts, domains, and networks connected to the Internet seems to be exploding. Not surprisingly, network traffic at major exchange points is doubling every few months. The Internet is a packet network, where each data packet is passed from a router to the next in the chain, until it reaches destination. For versatility and efficient utilization of the available transmission bandwidth, each router performs its decision where to forward a packet as independent of the other routers and the other packets for the same destination as possible.
Five key factors are required to keep pace if the Internet is to continue to provide good service:
- higher link speeds,
- better router data throughput,
- faster packet forwarding rates,
- quick adaptation to topology and load changes, and
- the support for Quality-of-Service (QoS).
Solutions for the first two are readily available: fiber-optic cables using wavelength-division multiplexing (WDM) and switching backplane interconnects. We present longest matching prefix techniques which help solving the other three factors. They allow for a high rate of forwarding decisions, quick updates, and can be extended to classify packets based on multiple fields.
The best known longest matching prefix solutions require memory accesses proportional to the length of the addresses. Our new algorithm uses binary search on hash tables organized by prefix lengths and scales very well as address and routing table sizes increase: independent of the table size, it requires a worst case time of log2(address bits) hash lookups. Thus only 5 hash lookups are needed for the current Internet protocol version 4 (IPv4) with 32 address bits and 7 for the upcoming IPv6 with 128 address bits. We also introduce mutating binary search and other optimizations that, operating on the largest available databases, reduce the worst case to 4 hashes and allow the majority of addresses to be found with at most 2 hashes. We expect similar improvements to hold for IPv6.
We extend these results to find the best match for a tuple of multiple fields of the packet’s header, as required for QoS support. We also show the versatility of the resulting algorithms by using it for such diverse applications as geographical information systems, memory management, garbage collection, persistent object-oriented databases, keeping distributed databases synchronized, and performing web-server access control.

1999
Marcel Waldvogel; Germano Caronni; Dan Sun; Nathalie Weiler; Bernhard Plattner
The VersaKey Framework: Versatile Group Key Management Journal Article
In: IEEE Journal on Selected Areas in Communications, vol. 17, no. 9, pp. 1614-1631, 1999.
Abstract | BibTeX | Tags: Multicast, Security | Links:
@article{Waldvogel1999VersaKey,
title = {The VersaKey Framework: Versatile Group Key Management},
author = {Marcel Waldvogel and Germano Caronni and Dan Sun and Nathalie Weiler and Bernhard Plattner},
url = {https://netfuture.ch/wp-content/uploads/1999/waldvogel99versakey.pdf},
year = {1999},
date = {1999-09-16},
urldate = {1000-01-01},
journal = {IEEE Journal on Selected Areas in Communications},
volume = {17},
number = {9},
pages = {1614-1631},
abstract = { Middleware supporting secure applications in a distributed environment faces several challenges. Scalable security in the context of multicasting or broadcasting is especially hard when privacy and authenticity is to be assured to highly dynamic groups where the application allows participants to join and leave at any time. Unicast security is well-known and has widely advanced into production state. But proposals for multicast security solutions that have been published so far are complex, often require trust in network components or are inefficient. In this paper, we propose a framework of new approaches for achieving scalable security in IP multicasting. Our solutions assure that that newly joining members are not able to understand past group traffic, and that leaving members may not follow future communication. For versatility, our framework supports a range of closely related schemes for key management, ranging from tightly centralized to fully distributed and even allows switching between these schemes on-the-fly with low overhead. Operations have low complexity (O(log \textit{N}) for joins and leaves), thus granting scalability even for very large groups. We also present a novel concurrency-enabling scheme, which was devised for fully distributed key management. In this paper we discuss the requirements for secure multicasting, present our flexible system, and evaluate its properties, based on the existing prototype implementation.},
keywords = {Multicast, Security},
pubstate = {published},
tppubtype = {article}
}
Milind M. Buddhikot; Subhash Suri; Marcel Waldvogel
Space Decomposition Techniques for Fast Layer-4 Switching Proceedings Article
In: Touch, Joseph D.; Sterbenz, James P. G. (Ed.): Protocols for High Speed Networks IV (Proceedings of PfHSN ’99), pp. 25-41, Kluwer Academic Publishers, Salem, MA, USA, 1999, ISBN: 0-7923-8690-6.
Abstract | BibTeX | Tags: Fast Routers, Quality of Service, Traffic Engineering | Links:
@inproceedings{Buddhikot1999Space,
title = {Space Decomposition Techniques for Fast Layer-4 Switching},
author = {Milind M. Buddhikot and Subhash Suri and Marcel Waldvogel},
editor = {Joseph D. Touch and James P. G. Sterbenz},
url = {https://netfuture.ch/wp-content/uploads/1999/buddhikot99space.pdf},
isbn = {0-7923-8690-6},
year = {1999},
date = {1999-01-01},
urldate = {1000-01-01},
booktitle = {Protocols for High Speed Networks IV (Proceedings of PfHSN '99)},
pages = {25-41},
publisher = {Kluwer Academic Publishers},
address = {Salem, MA, USA},
abstract = { Packet classification is the problem of matching each incoming packet at a router against a database of filters, which specify forwarding rules for the packets. The filters are a powerful and uniform way to implement new network services such as firewalls, Network Address Translation (NAT), Virtual Private Networks (VPN), and per-flow or class-based Quality of Service (QOS) guarantees. While several schemes have been proposed recently that can perform packet classification at high speeds, none of them achieves fast worst-case time for adding or deleting filters from the database. In this paper, we present a new scheme, based on space decomposition, whose search time is comparable to the best existing schemes, but which also offers fast worst-case filter update time. The three key ideas in this algorithm are as follows: (1) innovative data-structure based on quadtrees for a hierarchical representation of the recursively decomposed search space, (2) fractional cascading and precomputation to improve packet classification time, and (3) prefix partitioning to improve update time. Depending on the actual requirements of the system this algorithm is deployed in, a single parameter can be used to tradeoff search time for update time. Also, this algorithm is amenable to fast software and hardware implementation.},
keywords = {Fast Routers, Quality of Service, Traffic Engineering},
pubstate = {published},
tppubtype = {inproceedings}
}
Burkhard Stiller; Christina Class; Marcel Waldvogel; Germano Caronni; Daniel Bauer
A Flexible Middleware for Multimedia Communication: Design, Implementation, and Experience Journal Article
In: IEEE Journal on Selected Areas in Communications, vol. 17, no. 9, pp. 1580-1598, 1999.
Abstract | BibTeX | Tags: Middleware, Quality of Service | Links:
@article{Stiller1999Flexible,
title = {A Flexible Middleware for Multimedia Communication: Design, Implementation, and Experience},
author = {Burkhard Stiller and Christina Class and Marcel Waldvogel and Germano Caronni and Daniel Bauer},
url = {https://netfuture.ch/wp-content/uploads/1999/stiller99flexible.pdf},
year = {1999},
date = {1999-01-01},
urldate = {1000-01-01},
journal = {IEEE Journal on Selected Areas in Communications},
volume = {17},
number = {9},
pages = {1580-1598},
abstract = {Distributed multimedia applications require a variety of com-munication services. These services and different application requirements have to be provided and supported within (1) end-systems in an efficient and integrated manner, combining the precise specification of Quality-of-Service (QoS) requirements, application interfaces, multicast support, and security features, and within (2) the network. The Da CaPo++ system presented here provides an efficient end-system middleware for multimedia applications, capable of handling various types of applications in a modular fashion. Application needs and communication demands are specified by values in terms of QoS attributes and functional properties, such as encryption requirements or multicast support. Da CaPo++ automatically configures suitable communication protocols, provides for an efficient run-time support, and offers an easy-to-use, object-oriented application programming interface. While its applicability to real-life applications was shown by prototype implementations, performance evaluations have been carried out yielding practical experiences and numerical results.},
keywords = {Middleware, Quality of Service},
pubstate = {published},
tppubtype = {article}
}
1998
V. Srinivasan; George Varghese; Subhash Suri; Marcel Waldvogel
Fast and Scalable Layer Four Switching Proceedings Article
In: Proceedings of ACM SIGCOMM, pp. 191-202, 1998.
Abstract | BibTeX | Tags: Fast Routers, Hash Tables, Quality of Service | Links:
@inproceedings{Srinivasan1998Fast,
title = {Fast and Scalable Layer Four Switching},
author = {V. Srinivasan and George Varghese and Subhash Suri and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/1998/srinivasan98fast.pdf},
year = {1998},
date = {1998-09-01},
urldate = {1000-01-01},
booktitle = {Proceedings of ACM SIGCOMM},
pages = {191-202},
abstract = { In Layer Four switching, the route and resources allocated to a packet are determined by the destination address as well as other header fields of the packet such as source address, TCP and UDP port numbers. Layer Four switching unifies firewall processing, RSVP style resource reservation filters, QoS Routing, and normal unicast and multicast forwarding into a single framework. In this framework, the forwarding database of a router consists of a potentially large number of filters on key header fields. A given packet header can match multiple filters, so each filter is given a cost, and the packet is forwarded using the least cost matching filter. In this paper, we describe two new algorithms for solving the least cost matching filter problem at high speeds. Our first algorithm is based on a grid-of-tries construction and works optimally for processing filters consisting of two prefix fields (such as destination-source filters) using linear space. Our second algorithm, cross-producting, provides fast lookup times for arbitrary filters but potentially requires large storage. We describe a combination scheme that combines the advantages of both schemes. The combination scheme can be optimized to handle pure destination prefix filters in 4 memory accesses, destination-source filters in 8 memory accesses worst case, and all other filters in 11 memory accesses in the typical case.},
keywords = {Fast Routers, Hash Tables, Quality of Service},
pubstate = {published},
tppubtype = {inproceedings}
}
Marcel Waldvogel; George Varghese; Jon Turner; Bernhard Plattner
Scalable Best Matching Prefix Lookups Proceedings Article
In: Proceedings of PODC ’98, pp. 311, Puerto Vallarta, México, 1998.
Abstract | BibTeX | Tags: Fast Routers | Links:
@inproceedings{Waldvogel1998Scalable,
title = {Scalable Best Matching Prefix Lookups},
author = {Marcel Waldvogel and George Varghese and Jon Turner and Bernhard Plattner},
url = {https://netfuture.ch/wp-content/uploads/1998/waldvogel98scalable.pdf},
year = {1998},
date = {1998-06-30},
urldate = {1000-01-01},
booktitle = {Proceedings of PODC '98},
pages = {311},
address = {Puerto Vallarta, México},
abstract = {All global routing protocols use hierarchies to allow scaling to a world wide community while keeping the routing database size manageable. Databases of variable length prefixes are a powerful tool for providing this in a flexible manner, but require a Longest Prefix Matching algorithm. In this paper, we report a fundamentally new solution that is both algorithmically interesting and practical.
Our scheme is based on doing binary search on hash tables organized by prefix lengths, and scales very well as address and routing table sizes increase: independent of the table size, it requires a worst case time of log_{2}(\textit{address bits}) hash lookups. With the current Internet Protocol, which uses 32 bit addresses, at most 5 hash lookups are needed; for the upcoming 128 bit addresses of the next generation Internet Protocol (IPv6), 7 lookups suffice. Several refinements, including specializing the Binary Search with every match, considerably reduce the average number of hash search steps to less than 2.},
keywords = {Fast Routers},
pubstate = {published},
tppubtype = {inproceedings}
}
Our scheme is based on doing binary search on hash tables organized by prefix lengths, and scales very well as address and routing table sizes increase: independent of the table size, it requires a worst case time of log2(address bits) hash lookups. With the current Internet Protocol, which uses 32 bit addresses, at most 5 hash lookups are needed; for the upcoming 128 bit addresses of the next generation Internet Protocol (IPv6), 7 lookups suffice. Several refinements, including specializing the Binary Search with every match, considerably reduce the average number of hash search steps to less than 2.

Germano Caronni; Marcel Waldvogel; Dan Sun; Bernhard Plattner
Efficient Security for Large and Dynamic Multicast Groups Proceedings Article
In: Proceedings of the IEEE 7th International Workshop on Enabling Technologies: Infrastructure for Collaborative Enterprises (WET ICE ’98), Palo Alto, CA, USA, 1998.
Abstract | BibTeX | Tags: Multicast, Security | Links:
@inproceedings{Caronni1998Efficient,
title = {Efficient Security for Large and Dynamic Multicast Groups},
author = {Germano Caronni and Marcel Waldvogel and Dan Sun and Bernhard Plattner},
url = {https://netfuture.ch/wp-content/uploads/1998/caronni98efficient.pdf},
year = {1998},
date = {1998-06-01},
urldate = {1000-01-01},
booktitle = {Proceedings of the IEEE 7th International Workshop on Enabling Technologies: Infrastructure for Collaborative Enterprises (WET ICE '98)},
address = {Palo Alto, CA, USA},
abstract = { Proposals for multicast security that have been published so far are complex, often require trust in network components or are inefficient. In this paper we propose a series of novel approaches for achieving scalable security in IP multicast, providing privacy and authentication on a group-wide basis. They can be employed to efficiently secure multi-party applications where members of highly dynamic groups of arbitrary size may participate. Supporting dynamic groups implies that newly joining members must not be able to understand past group communications, and that leaving members may not follow future communications. Key changes are required for all group members when a leave or join occurs, which poses a problem if groups are large. The algorithms presented here require no trust in third parties, support either centralized or fully distributed management of keying material, and have low complexity (O(log N) or less). This grants scalability even for large groups. },
keywords = {Multicast, Security},
pubstate = {published},
tppubtype = {inproceedings}
}

Germano Caronni; Marcel Waldvogel; Dan Sun; Bernhard Plattner
Efficient Security for Large and Dynamic Multicast Groups Technical Report
TIK, ETH Zürich no. TIK-41, 1998.
BibTeX | Tags: Multicast, Security
@techreport{Caronni1998Efficient-techreport,
title = {Efficient Security for Large and Dynamic Multicast Groups},
author = {Germano Caronni and Marcel Waldvogel and Dan Sun and Bernhard Plattner},
year = {1998},
date = {1998-01-01},
urldate = {1000-01-01},
number = {TIK-41},
institution = {TIK, ETH Zürich},
keywords = {Multicast, Security},
pubstate = {published},
tppubtype = {techreport}
}

Germano Caronni; Marcel Waldvogel; Dan Sun; Nathalie Weiler; Bernhard Plattner
VersaKey: Versatile Key Management for Large and Dynamic Multicast Groups Technical Report
TIK, ETH Zürich no. TIK-57, 1998.
BibTeX | Tags: Multicast, Security
@techreport{Caronni1998VersaKey-techreport,
title = {VersaKey: Versatile Key Management for Large and Dynamic Multicast Groups},
author = {Germano Caronni and Marcel Waldvogel and Dan Sun and Nathalie Weiler and Bernhard Plattner},
year = {1998},
date = {1998-01-01},
urldate = {1000-01-01},
number = {TIK-57},
institution = {TIK, ETH Zürich},
keywords = {Multicast, Security},
pubstate = {published},
tppubtype = {techreport}
}

1997
Marcel Waldvogel; George Varghese; Jon Turner; Bernhard Plattner
Scalable High Speed IP Routing Table Lookups Proceedings Article
In: Proceedings of ACM SIGCOMM, pp. 25-36, 1997.
Abstract | BibTeX | Tags: Fast Routers, Hash Tables | Links:
@inproceedings{Waldvogel1997Scalable,
title = {Scalable High Speed IP Routing Table Lookups},
author = {Marcel Waldvogel and George Varghese and Jon Turner and Bernhard Plattner},
url = {https://netfuture.ch/wp-content/uploads/1997/waldvogel97scalable.pdf},
year = {1997},
date = {1997-08-28},
urldate = {1000-01-01},
booktitle = {Proceedings of ACM SIGCOMM},
pages = {25-36},
abstract = {Internet address lookup is a challenging problem because of increasing routing table sizes, increased traffic, higher speed links, and the migration to 128 bit IPv6 addresses. IP routing lookup requires computing the best matching prefix, for which standard solutions like hashing were believed to be inapplicable. The best existing solution we know of, BSD radix tries, scales badly as IP moves to 128 bit addresses. Our paper describes a new algorithm for best matching prefix using binary search on hash tables organized by prefix lengths. Our scheme scales very well as address and routing table sizes increase: independent of the table size, it requires a worst case time of log_{2}(\textit{address bits}) hash lookups. Thus only 5 hash lookups are needed for IPv4 and 7 for IPv6. We also introduce Mutating Binary Search and other optimizations that, for a typical IPv4 backbone router with over 33,000 entries, considerably reduce the average number of hashes to less than 2, of which one hash can be simplified to an indexed array access. We expect similar average case behavior for IPv6.},
keywords = {Fast Routers, Hash Tables},
pubstate = {published},
tppubtype = {inproceedings}
}

Daniel S. Decasper; Marcel Waldvogel; Zubin Dittia; Adiseshu Hari; Guru Parulkar; Bernhard Plattner
Crossbow — A Toolkit for Integrated Services over Cell Switched IPv6 Proceedings Article
In: Proceedings of the IEEE ATM ’97 workshop, Lisboa, Portugal, 1997.
Abstract | BibTeX | Tags: Fast Routers, Quality of Service | Links:
@inproceedings{Decasper1997Crossbow,
title = {Crossbow --- A Toolkit for Integrated Services over Cell Switched IPv6},
author = {Daniel S. Decasper and Marcel Waldvogel and Zubin Dittia and Adiseshu Hari and Guru Parulkar and Bernhard Plattner},
url = {https://netfuture.ch/wp-content/uploads/1997/decasper97crossbow.pdf},
year = {1997},
date = {1997-05-01},
urldate = {1000-01-01},
booktitle = {Proceedings of the IEEE ATM '97 workshop},
address = {Lisboa, Portugal},
abstract = {The project Crossbow provides a framework to investigate services and mechanisms including resource management and packet scheduling for multimedia/multicast applications. In particular the Internet Protocol version 6 (IPv6, IP next generation, IPng) protocol suite on top of ATM is considered to demonstrate possible synergy between ATM and IPv6. The presented architecture includes IPv6 and RSVP, running on BSD Unix using the 1.2 Gbps APIC (ATM Port Interconnect Controller) chip, as well as support for Ethernet networks.},
keywords = {Fast Routers, Quality of Service},
pubstate = {published},
tppubtype = {inproceedings}
}
1991
Stuart Haber; W. Scott Stornetta
How to Time-Stamp a Digital Document Journal Article
In: Journal of Cryptology, vol. 3, iss. 2, pp. 99-111, 1991.
Abstract | BibTeX | Tags: | Links:
@article{Haber-Stornetta-1991,
title = {How to Time-Stamp a Digital Document},
author = {Stuart Haber and W. Scott Stornetta},
url = {https://netfuture.ch/wp-content/uploads/2022/02/haber_stornetta.pdf},
year = {1991},
date = {1991-04-01},
journal = {Journal of Cryptology},
volume = {3},
issue = {2},
pages = {99-111},
abstract = {The prospect of a world in which all text, audio, picture, and video documents are in digital form on easily modifiable media raises the issue of how to certify when a document was created or last changed. The problem is to time-stamp the data, not the medium. We propose computationally practical procedures for digital time-stamping of such documents so that it is infeasible for a user either to back-date or to forward-date his document, even with the collusion of a time-stamping service. Our procedures maintain complete privacy of the documents themselves, and require no record-keeping by the time-stamping service.},
keywords = {},
pubstate = {published},
tppubtype = {article}
}
1989
Waldvogel, Marcel
Guck mal da! Journal Article
In: 68000er, vol. 07, pp. 98ff., 1989.
@article{Waldvogel89Guck,
title = {Guck mal da!},
author = {Waldvogel, Marcel},
editor = {Markt&Technik},
year = {1989},
date = {1989-07-01},
urldate = {1000-01-01},
journal = {68000er},
volume = {07},
pages = {98ff.},
keywords = {Atari ST},
pubstate = {published},
tppubtype = {article}
}
1000
Marcel Waldvogel
Guck Book Section
In: Glaser, Peter (Ed.): Kopier mich!, Zweitausendeins, 1000.
BibTeX | Tags: Atari ST, Software | Links:
@incollection{Waldvogel1991Guck,
title = {Guck},
author = {Marcel Waldvogel},
editor = {Peter Glaser},
url = {https://netfuture.ch/wp-content/uploads/2017/01/guck.pdf
https://netfuture.ch/wp-content/uploads/2017/01/guck.tar.gz
http://data.onb.ac.at/rec/AC04429672},
year = {1000},
date = {1000-01-01},
urldate = {1000-01-01},
booktitle = {Kopier mich!},
publisher = {Zweitausendeins},
keywords = {Atari ST, Software},
pubstate = {published},
tppubtype = {incollection}
}


