General audience texts
Besides the scholarly publications listed below, I have written many texts in English and German. My more notable German texts appeared by DNIP.ch. I also maintain document collections intended for a broad audience:
Scholarly publications
Up-to-date citation counts (provided by Google Scholar). List of patents granted.
2017
Marcel Waldvogel; Thomas Zink
X.509 User Certificate-based Two-Factor Authentication for Web Applications Proceedings Article
In: Müller, Paul; Neumair, Bernhard; Reiser, Helmut; Dreo Rodosek, Gabi (Ed.): 10. DFN-Forum Kommunikationstechnologien, 2017.
Abstract | BibTeX | Tags: Federated Services, Identity Management, Passwords, Security, Usability, Web Applications, X.509 | Links:
@inproceedings{Waldvogel-X509,
title = {X.509 User Certificate-based Two-Factor Authentication for Web Applications},
author = {Marcel Waldvogel and Thomas Zink},
editor = {Paul Müller and Bernhard Neumair and Helmut Reiser and Dreo Rodosek, Gabi},
url = {https://netfuture.ch/wp-content/uploads/2018/05/x509auth.pdf
},
year = {2017},
date = {2017-05-30},
urldate = {1000-01-01},
booktitle = {10. DFN-Forum Kommunikationstechnologien},
abstract = {An appealing property to researchers, educators, and students is the openness of the physical environment and IT infrastructure of their organizations. However, to the IT administration, this creates challenges way beyond those of a single-purpose business or administration. Especially the personally identifiable information or the power of the critical functions behind these logins, such as financial transactions or manipulating user accounts, require extra protection in the heterogeneous educational environment with single-sign-on. However, most web-based environments still lack a reasonable second-factor protection or at least the enforcement of it for privileged operations without hindering normal usage.
In this paper we introduce a novel and surprisingly simple yet extremely flexible way to implement two-factor authentication based on X.509 user certificates in web applications. Our solution requires only a few lines of code in web server configuration and none in the application source code for basic protection. Furthermore, since it is based on X.509 certificates, it can be easily combined with smartcards or USB cryptotokens to further enhance security.},
keywords = {Federated Services, Identity Management, Passwords, Security, Usability, Web Applications, X.509},
pubstate = {published},
tppubtype = {inproceedings}
}
In this paper we introduce a novel and surprisingly simple yet extremely flexible way to implement two-factor authentication based on X.509 user certificates in web applications. Our solution requires only a few lines of code in web server configuration and none in the application source code for basic protection. Furthermore, since it is based on X.509 certificates, it can be easily combined with smartcards or USB cryptotokens to further enhance security.
Thomas Zink; Marcel Waldvogel
X.509 User Certificate-based Two-Factor Authentication for Web Applications Technical Report
Distributed Systems Laboratory, University of Konstanz no. KN-2017-DISY-03, 2017.
Abstract | BibTeX | Tags: Certificates, Identity Management, Security, Two-Factor Authentication, Usability, Web Applications, X509 | Links:
@techreport{Zink2017X509,
title = {X.509 User Certificate-based Two-Factor Authentication for Web Applications},
author = {Thomas Zink and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2017/03/kn-2017-disy-03.pdf},
year = {2017},
date = {2017-03-14},
urldate = {1000-01-01},
number = {KN-2017-DISY-03},
institution = {Distributed Systems Laboratory, University of Konstanz},
abstract = {An appealing property to researchers, educators, and students is the openness
of the physical environment and IT infrastructure of their organizations. How-
ever, to the IT administration, this creates challenges way beyond those of a
single-purpose business or administration. Especially the personally identifiable
information or the power of the critical functions behind these logins, such as
financial transactions or manipulating user accounts, require extra protection in
the heterogeneous educational environment with single-sign-on. However, most
web-based environments still lack a reasonable second-factor protection or at
least the enforcement of it for privileged operations without hindering normal
usage.
In this paper we introduce a novel and surprisingly simple yet extremely flex-
ible way to implement two-factor authentication based on X.509 user certificates
in web applications. Our solution requires only a few lines of code in web server
configuration and none in the application source code for basic protection. Fur-
thermore, since it is based on X.509 certificates, it can be easily combined with
smartcards or USB cryptotokens to further enhance security.},
keywords = {Certificates, Identity Management, Security, Two-Factor Authentication, Usability, Web Applications, X509},
pubstate = {published},
tppubtype = {techreport}
}
of the physical environment and IT infrastructure of their organizations. How-
ever, to the IT administration, this creates challenges way beyond those of a
single-purpose business or administration. Especially the personally identifiable
information or the power of the critical functions behind these logins, such as
financial transactions or manipulating user accounts, require extra protection in
the heterogeneous educational environment with single-sign-on. However, most
web-based environments still lack a reasonable second-factor protection or at
least the enforcement of it for privileged operations without hindering normal
usage.
In this paper we introduce a novel and surprisingly simple yet extremely flex-
ible way to implement two-factor authentication based on X.509 user certificates
in web applications. Our solution requires only a few lines of code in web server
configuration and none in the application source code for basic protection. Fur-
thermore, since it is based on X.509 certificates, it can be easily combined with
smartcards or USB cryptotokens to further enhance security.
2014
Marcel Waldvogel; Jürgen Kollek
SIEGE: Service-Independent Enterprise-GradE protection against password scans Proceedings Article
In: Müller, Paul; Neumair, Bernhard; Reiser, Helmut; Dreo Rodosek, Gabi (Ed.): 7. DFN-Forum Kommunikationstechnologien — Beiträge der Fachtagung, Gesellschaft für Informatik, 2014.
Abstract | BibTeX | Tags: Federated Services, Identity Management, Intrusion Detection, Passwords, Peer, Security | Links:
@inproceedings{Waldvogel2014SIEGE,
title = {SIEGE: Service-Independent Enterprise-GradE protection against password scans},
author = {Marcel Waldvogel and Jürgen Kollek},
editor = {Paul Müller and Bernhard Neumair and
Helmut Reiser and Dreo Rodosek, Gabi},
url = {https://netfuture.ch/wp-content/uploads/2014/08/Waldvogel2014SIEGE.pdf
https://netfuture.ch/wp-content/uploads/2014/08/Waldvogel2014SIEGE-slides.pdf},
year = {2014},
date = {2014-06-16},
urldate = {1000-01-01},
booktitle = {7. DFN-Forum Kommunikationstechnologien -- Beiträge der Fachtagung},
publisher = {Gesellschaft für Informatik},
series = {Lecture Notes in Informatics},
abstract = {Security is one of the main challenges today, complicated significantly by the heterogeneous and open academic networks with thousands of different applications. Botnet-based brute-force password scans are a common security threat against the open academic networks. Common defenses are hard to maintain, error-prone and do not reliably discriminate between user error and coordinated attack. In this paper, we present a novel approach, which allows to secure many network services at once. By combining in-app tracking, local and global crowdsourcing, geographic information, and probabilistic user-bot distinction through differential password analysis, our PAM-based detection module can provide higher accuracy and faster blocking of botnets. In the future, we aim to make the mechanism even more generic and thus provide a distributed defense against one of the strongest threats against our infrastructure.},
keywords = {Federated Services, Identity Management, Intrusion Detection, Passwords, Peer, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
2012
Michael Simon; Marcel Waldvogel; Sven Schober; Saher Semaan; Martin Nussbaumer
bwIDM: Föderieren auch nicht-webbasierter Dienste auf Basis von SAML Proceedings Article
In: 5. DFN-Forum Kommunikationstechnologien: Verteilte Systeme im Wissenschaftsbereich, pp. 119-128, 2012.
Abstract | BibTeX | Tags: Cloud Storage, Identity Management, Security | Links:
@inproceedings{Simon2012bwIDM,
title = {bwIDM: Föderieren auch nicht-webbasierter Dienste auf Basis von SAML},
author = {Michael Simon and Marcel Waldvogel and Sven Schober and Saher Semaan and Martin Nussbaumer},
url = {https://netfuture.ch/wp-content/uploads/2012/simon12bwidm.pdf},
year = {2012},
date = {2012-05-20},
urldate = {1000-01-01},
booktitle = {5. DFN-Forum Kommunikationstechnologien: Verteilte Systeme im Wissenschaftsbereich},
pages = {119-128},
crossref = {DBLP:conf/dfn/2012},
abstract = {Zur organisationsübergreifenden Nutzung von IT-Diensten werden Dienstföderationen gebildet. Dabei kann das Nutzerkonto der sogenannten Heimateinrichtung auch zum Zugriff auf nicht-lokale Dienste genutzt werden. Während die Integration webbasierter Dienste in Föderationen mit SAML und beispielsweise Shibboleth mittlerweile in vielen Anwendungsbereichen allgegenwärtig ist, fällt die Integration nicht-webbasierter IT-Dienste schwer. Existierende Ansätze, mit denen sich prinzipiell auch nicht-webbasierte Dienste integrieren lassen, erfüllen essentielle Anforderungen nicht und/oder sind nach ihrem heutigen Entwicklungsstand noch nicht betriebsfähig. In diesem Papier werden zwei Verfahren für nicht-webbasierte, föderative Dienstzugriffe (Moonshot und PAM/ECP) evaluiert und notwendige Erweiterungen zur Sicherstellung der Betriebsfa ̈higkeit vorgestellt. Ein implementierter Proof-of-Concept zeigt die Umsetzbarkeit der Lösung.},
keywords = {Cloud Storage, Identity Management, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
2011
Pascal Gienger; Marcel Waldvogel
Polybius: Secure Web Single-Sign-On for Legacy Applications Proceedings Article
In: 4. DFN-Forum Kommunikationstechnologien, 2011.
Abstract | BibTeX | Tags: Cloud Storage, Identity Management, Security, Trust, Web Applications | Links:
@inproceedings{Gienger2011Polybius,
title = {Polybius: Secure Web Single-Sign-On for Legacy Applications},
author = {Pascal Gienger and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2011/gienger11polybius.pdf},
year = {2011},
date = {2011-06-20},
urldate = {1000-01-01},
booktitle = {4. DFN-Forum Kommunikationstechnologien},
abstract = {Web-based interfaces to applications in all domains of university life are surging. Given the diverse demands in and the histories of universities, combined with the rapid IT industry developments, all attempts at a sole all-encompassing platform for single-sign-on (SSO) will remain futile. In this paper, we present an architecture for a meta-SSO, which is able to seamlessly integrate with a wide variety of existing local sign-in and SSO mechanisms. It is therefore an excellent candidate for a university-wide all-purpose SSO system. Among the highlights are: No passwords are ever stored on disk, neither in the browser nor in the gateway; its basics have been implemented in a simple, yet versatile Apache module; and it can help reducing the impact of security problems anywhere in the system. It could even form the basis for secure inter-university collaborations and mutual outsourcing.},
keywords = {Cloud Storage, Identity Management, Security, Trust, Web Applications},
pubstate = {published},
tppubtype = {inproceedings}
}
Sebastian Graf; Vyacheslav Zholudev; Lukas Lewandowski; Marcel Waldvogel
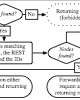
Hecate: Managing Authorization with RESTful XML Proceedings Article
In: Proceedings of WS-REST 2011, 2011.
Abstract | BibTeX | Tags: Identity Management, Security, XML | Links:
@inproceedings{Graf2011Hecate,
title = {Hecate: Managing Authorization with RESTful XML},
author = {Sebastian Graf and Vyacheslav Zholudev and Lukas Lewandowski and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2011/graf11hecate.pdf},
year = {2011},
date = {2011-03-28},
urldate = {1000-01-01},
booktitle = {Proceedings of WS-REST 2011},
abstract = {The potentials of REST offers new ways for communications between louse coupled entities featured through the Web of Things. The binding of the disjunct components of this architecture creates security issues, such as the centralized authorization techniques respecting the independence of the underlying entities. This results in the question how authorization is performed respecting the flexibility of REST without any knowledge about the underlying resources. Nevertheless, possible knowledge about these resources should enable the authorization workflow to offer finer-granular permissions on substructures of the resources. With our new approach - named Hecate - we offer a framework to assure simplified handling while keeping the potentials and flexibility of REST. We have designed an architecture based on XML with a flexible authorization mechanism on the one hand and optional resource-awareness on the other hand. The flexibility within the authorization work-flow bases on permission sets respecting the HTTP verbs. Additional in-depth knowledge of the entity optionally extends these permissions with resource-aware filters. Hecate offers not only great benefits because of its flexibility, but also because of the optional extensibility proved within the two reference implementations. With Hecate, we show that a centralized authorization mechanism combining independence and optional resource-based filtering extends the flexibility of REST rather than restricting it.},
keywords = {Identity Management, Security, XML},
pubstate = {published},
tppubtype = {inproceedings}
}