General audience texts
Besides the scholarly publications listed below, I have written many texts in English and German. My more notable German texts appeared by DNIP.ch. I also maintain document collections intended for a broad audience:
Scholarly publications
Up-to-date citation counts (provided by Google Scholar). List of patents granted.
2018
Matthias Held; Marcel Waldvogel
Fighting Ransomware with Guided Undo Proceedings Article
In: Proceedings of NISK 2018, 2018.
Abstract | BibTeX | Tags: Cloud Storage, Intrusion Detection, Ransomware, Replication, Security, Usability, Web Applications | Links:
@inproceedings{Held2018FightingRansomware,
title = {Fighting Ransomware with Guided Undo},
author = {Matthias Held and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2018/07/held2018fightingransomware.pdf
https://netfuture.ch/wp-content/uploads/2018/09/ransomware_detection.pdf
https://netfuture.ch/wp-content/uploads/2018/09/2018-ransomware.odp},
year = {2018},
date = {2018-09-18},
urldate = {1000-01-01},
booktitle = {Proceedings of NISK 2018},
abstract = {Ransomware attacks are rare, yet catastrophic. On closer inspection, they differ from other malware infections: Given appropriate preparation, they do not need to be caught on first sight, but can be undone later. However, current ransomware protection follows the beaten path of anti-malware copying their fallacies. We show how the move to personal cloud storage allows for a paradigm shift in ransomware protection: exceptional attack isolation, perfect elimination of false positive alerts, and simplified recovery.
In this paper, we analyze the necessary operations for ransomware, extend existing ransomware taxonomy, and verify them against real-world malware samples. We analyze the costs and benefits of moving ransomware detection to versioned personal cloud storage. Our content, meta data, and behavior analysis paired with a `guilt by association' capability greatly improve the false positive rate, but the guided undo make this rate all but inconsequential. Even though the user now carries a new burden, it comes with clear responsibilities and benefits, while being freed from questionable duties, resulting in a win-win situation for user experience and detection quality.
},
keywords = {Cloud Storage, Intrusion Detection, Ransomware, Replication, Security, Usability, Web Applications},
pubstate = {published},
tppubtype = {inproceedings}
}
In this paper, we analyze the necessary operations for ransomware, extend existing ransomware taxonomy, and verify them against real-world malware samples. We analyze the costs and benefits of moving ransomware detection to versioned personal cloud storage. Our content, meta data, and behavior analysis paired with a `guilt by association’ capability greatly improve the false positive rate, but the guided undo make this rate all but inconsequential. Even though the user now carries a new burden, it comes with clear responsibilities and benefits, while being freed from questionable duties, resulting in a win-win situation for user experience and detection quality.
2014
Marcel Waldvogel; Jürgen Kollek
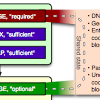
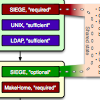
SIEGE: Service-Independent Enterprise-GradE protection against password scans Journal Article
In: DFN-Mitteilungen, no. 87, pp. 40–46, 2014, ISSN: 0177-6894.
Abstract | BibTeX | Tags: Federated Services, Intrusion Detection, Security | Links:
@article{Waldvogel2014SIEGE-DFN,
title = {SIEGE: Service-Independent Enterprise-GradE protection against password scans},
author = {Marcel Waldvogel and Jürgen Kollek},
editor = {Kai Hoelzner},
url = {https://netfuture.ch/wp-content/uploads/2014/12/SIEGE-DFN.pdf
https://www.dfn.de/fileadmin/5Presse/DFNMitteilungen/DFN_Mitteilungen_87.pdf},
issn = {0177-6894},
year = {2014},
date = {2014-11-30},
urldate = {1000-01-01},
journal = {DFN-Mitteilungen},
number = {87},
pages = {40--46},
abstract = {Security is one of the main challenges today, complicated significantly by the heterogeneous and open academic networks with thousands of different applications. Botnet-based brute-force password scans are a common security threat against the open academic networks. Common de- fenses are hard to maintain, error-prone and do not reliably discriminate between user error and coordinated attack. In this paper, we present a novel approach, which allows to secure many net- work services at once. By combining in-app tracking, local and global crowdsourcing, geographic information, and probabilistic user-bot distinction through differential password analysis, our PAM-based detection module can provide higher accuracy and faster blocking of botnets. In the future, we aim to make the mechanism even more generic and thus provide a distributed defense for our infrastructure against one of the strongest threats.},
keywords = {Federated Services, Intrusion Detection, Security},
pubstate = {published},
tppubtype = {article}
}
Marcel Waldvogel; Jürgen Kollek
SIEGE: Service-Independent Enterprise-GradE protection against password scans Proceedings Article
In: Müller, Paul; Neumair, Bernhard; Reiser, Helmut; Dreo Rodosek, Gabi (Ed.): 7. DFN-Forum Kommunikationstechnologien — Beiträge der Fachtagung, Gesellschaft für Informatik, 2014.
Abstract | BibTeX | Tags: Federated Services, Identity Management, Intrusion Detection, Passwords, Peer, Security | Links:
@inproceedings{Waldvogel2014SIEGE,
title = {SIEGE: Service-Independent Enterprise-GradE protection against password scans},
author = {Marcel Waldvogel and Jürgen Kollek},
editor = {Paul Müller and Bernhard Neumair and
Helmut Reiser and Dreo Rodosek, Gabi},
url = {https://netfuture.ch/wp-content/uploads/2014/08/Waldvogel2014SIEGE.pdf
https://netfuture.ch/wp-content/uploads/2014/08/Waldvogel2014SIEGE-slides.pdf},
year = {2014},
date = {2014-06-16},
urldate = {1000-01-01},
booktitle = {7. DFN-Forum Kommunikationstechnologien -- Beiträge der Fachtagung},
publisher = {Gesellschaft für Informatik},
series = {Lecture Notes in Informatics},
abstract = {Security is one of the main challenges today, complicated significantly by the heterogeneous and open academic networks with thousands of different applications. Botnet-based brute-force password scans are a common security threat against the open academic networks. Common defenses are hard to maintain, error-prone and do not reliably discriminate between user error and coordinated attack. In this paper, we present a novel approach, which allows to secure many network services at once. By combining in-app tracking, local and global crowdsourcing, geographic information, and probabilistic user-bot distinction through differential password analysis, our PAM-based detection module can provide higher accuracy and faster blocking of botnets. In the future, we aim to make the mechanism even more generic and thus provide a distributed defense against one of the strongest threats against our infrastructure.},
keywords = {Federated Services, Identity Management, Intrusion Detection, Passwords, Peer, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
Marcel Waldvogel; Jürgen Kollek
SIEGE: Service-Independent Enterprise-GradE protection against password scans Technical Report
University of Konstanz no. KN-2014-DiSy-001, 2014.
Abstract | BibTeX | Tags: Denial of Service, Intrusion Detection, Peer-to-Peer, Security, Trust | Links:
@techreport{waldvogel4siege,
title = {SIEGE: Service-Independent Enterprise-GradE protection against password scans},
author = {Marcel Waldvogel and Jürgen Kollek},
url = {https://netfuture.ch/wp-content/uploads/2014/01/waldvogel14siege.pdf},
year = {2014},
date = {2014-01-17},
urldate = {1000-01-01},
number = {KN-2014-DiSy-001},
institution = {University of Konstanz},
abstract = {Security is one of the main challenges today, complicated significantly by the heterogeneous and open academic networks with thousands of different applications. Botnet-based brute-force password scans are common security threat against the open academic networks. Common defenses are hard to maintain, error-prone and do not reliably discriminate between user error and coordinated attack. In this paper, we present a novel approach, which allows to secure many network services at once. By combining in-app tracking, local and global crowdsourcing, geographic information, and probabilistic user-bot distinction through differential password analysis, our PAM-based detection module can provide higher accuracy and faster blocking of bot- nets. In the future, we aim to make the mechanism even more generic and thus provide a distributed defense against one of the strongest threats against our infrastructure.},
keywords = {Denial of Service, Intrusion Detection, Peer-to-Peer, Security, Trust},
pubstate = {published},
tppubtype = {techreport}
}
2009
Florian Mansmann; Fabian Fischer; Daniel A. Keim; Stephan Pietzko; Marcel Waldvogel
Interactive Analysis of NetFlows for Misuse Detection in Large IP Networks Proceedings Article
In: DFN-Forum Kommunikationstechnologie, Garching (Munich), Germany, 2009.
Abstract | BibTeX | Tags: Intrusion Detection, Security | Links:
@inproceedings{Mansmann2009Interactive,
title = {Interactive Analysis of NetFlows for Misuse Detection in Large IP Networks},
author = {Florian Mansmann and Fabian Fischer and Daniel A. Keim and Stephan Pietzko and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2009/mansmann09interactive.pdf},
year = {2009},
date = {2009-05-01},
urldate = {1000-01-01},
booktitle = {DFN-Forum Kommunikationstechnologie},
address = {Garching (Munich), Germany},
abstract = {While more and more applications require higher network bandwidth, there is also a tendency that large portions of this bandwidth are misused for dubious purposes, such as unauthorized VoIP, file sharing, or criminal botnet activity. Automatie intrusion detection methods can detcct a large portion of such misuse, but novel patterns can only be detected by humans. Moreover, interpretation of large amounts of alerts imposes new challenges on the analysts. The goal of this paper is to preseot the visual analysis system NFlowVis to interactively detcct unwanted usage of the network infrastructure either by pivoting NetFlows using IOS alerts or by specifying usage patterns, such as sets of suspicious port numbers. Thereby, our work focuses on providing a scalable approach to store and retrieve large quantities of Netflows by means of a database management system.},
keywords = {Intrusion Detection, Security},
pubstate = {published},
tppubtype = {inproceedings}
}

2008
Fabian Fischer; Florian Mansmann; Daniel A. Keim; Stephan Pietzko; Marcel Waldvogel
Large-scale Network Monitoring for Visual Analysis of Attacks Proceedings Article
In: 5th International Workshop on Visualization for Cyber Security (VizSEC 2008), Cambridge, MA, USA, 2008.
Abstract | BibTeX | Tags: Intrusion Detection, Security | Links:
@inproceedings{Fischer2008Large-scale,
title = {Large-scale Network Monitoring for Visual Analysis of Attacks},
author = {Fabian Fischer and Florian Mansmann and Daniel A. Keim and Stephan Pietzko and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2008/fischer08large-scale.pdf},
year = {2008},
date = {2008-08-15},
urldate = {1000-01-01},
booktitle = {5th International Workshop on Visualization for Cyber Security (VizSEC 2008)},
address = {Cambridge, MA, USA},
abstract = {The importance of the Internet and our dependency on computer networks are steadily growing, which results in high costs and substantial consequences in case of successful intrusions, stolen data, and interrupted services. At the same time, a trend towards massive attacks against the network infrastructure is noticeable. Therefore, monitoring large networks has become an important field in practice and research. Through monitoring systems, attacks can be detected and analyzed to gain knowledge of how to better protect the network in the future. In the scope of this paper, we present a system to analyze NetFlow data using a relational database system. NetFlow records are linked with alerts from an intrusion detection system to enable efficient exploration of suspicious activity within the monitored network. Within the system, the monitored network is mapped to a TreeMap visualization, the attackers are arranged at the borders and linked using splines parameterized with prefix information. In a series of case studies, we demonstrate how the tool can be used to judge the relevance of alerts, to reveal massive distributed attacks, and to analyze service usage within a network.},
keywords = {Intrusion Detection, Security},
pubstate = {published},
tppubtype = {inproceedings}
}


