General audience texts
Besides the scholarly publications listed below, I have written many texts in English and German. My more notable German texts appeared by DNIP.ch. I also maintain document collections intended for a broad audience:
Scholarly publications
Up-to-date citation counts (provided by Google Scholar). List of patents granted.
2018
Marcel Waldvogel; Thomas Zink
Einfache Zwei-Faktor-Authentisierung Journal Article
In: Digma, vol. 2018, no. 3, 2018, ISSN: 2270000414598.
Abstract | BibTeX | Tags: Passwords, Security, Two-Factor Authentication, Usability | Links:
@article{Waldvogel2018Einfache-2FA,
title = {Einfache Zwei-Faktor-Authentisierung},
author = {Marcel Waldvogel and Thomas Zink},
url = {https://netfuture.ch/wp-content/uploads/2018/09/einfache-zwei-faktor-authentisierung.pdf},
issn = {2270000414598},
year = {2018},
date = {2018-09-30},
urldate = {1000-01-01},
journal = {Digma},
volume = {2018},
number = {3},
abstract = {Der Trend zu Kundennähe und architektonischen Offenheit in Firmen und Behörden führt zu zusätzlichen Herausforderungen bei Datenschutz und -sicherheit. Viel zu häufig fehlen Know-How, Quellcode oder Ressourcen, um die betroffenen Anwendungen an die neuen Sicherheitsanforderungen anzupassen. Wir zeigen auf, wie gerade in diesen Fällen eine Zwei-Faktor-Authentisierung mittels X.509-Zertifikaten eine schnell umsetzbare, einfache, komfortable und trotzdem starke und erweiterbare Sicherheitskomponente sein kann, z.T. ohne Eingriff in die Anwendung.},
keywords = {Passwords, Security, Two-Factor Authentication, Usability},
pubstate = {published},
tppubtype = {article}
}

Matthias Held; Marcel Waldvogel
Fighting Ransomware with Guided Undo Proceedings Article
In: Proceedings of NISK 2018, 2018.
Abstract | BibTeX | Tags: Cloud Storage, Intrusion Detection, Ransomware, Replication, Security, Usability, Web Applications | Links:
@inproceedings{Held2018FightingRansomware,
title = {Fighting Ransomware with Guided Undo},
author = {Matthias Held and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2018/07/held2018fightingransomware.pdf
https://netfuture.ch/wp-content/uploads/2018/09/ransomware_detection.pdf
https://netfuture.ch/wp-content/uploads/2018/09/2018-ransomware.odp},
year = {2018},
date = {2018-09-18},
urldate = {1000-01-01},
booktitle = {Proceedings of NISK 2018},
abstract = {Ransomware attacks are rare, yet catastrophic. On closer inspection, they differ from other malware infections: Given appropriate preparation, they do not need to be caught on first sight, but can be undone later. However, current ransomware protection follows the beaten path of anti-malware copying their fallacies. We show how the move to personal cloud storage allows for a paradigm shift in ransomware protection: exceptional attack isolation, perfect elimination of false positive alerts, and simplified recovery.
In this paper, we analyze the necessary operations for ransomware, extend existing ransomware taxonomy, and verify them against real-world malware samples. We analyze the costs and benefits of moving ransomware detection to versioned personal cloud storage. Our content, meta data, and behavior analysis paired with a `guilt by association' capability greatly improve the false positive rate, but the guided undo make this rate all but inconsequential. Even though the user now carries a new burden, it comes with clear responsibilities and benefits, while being freed from questionable duties, resulting in a win-win situation for user experience and detection quality.
},
keywords = {Cloud Storage, Intrusion Detection, Ransomware, Replication, Security, Usability, Web Applications},
pubstate = {published},
tppubtype = {inproceedings}
}
In this paper, we analyze the necessary operations for ransomware, extend existing ransomware taxonomy, and verify them against real-world malware samples. We analyze the costs and benefits of moving ransomware detection to versioned personal cloud storage. Our content, meta data, and behavior analysis paired with a `guilt by association’ capability greatly improve the false positive rate, but the guided undo make this rate all but inconsequential. Even though the user now carries a new burden, it comes with clear responsibilities and benefits, while being freed from questionable duties, resulting in a win-win situation for user experience and detection quality.
2017
Robert Müller; Marcel Waldvogel; Corinna Schmitt
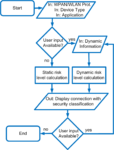
MoDeNA: Enhancing User Security for Devices in Wireless Personal and Local Area Networks Proceedings Article
In: Proceedings of AIMS 2017, 2017.
Abstract | BibTeX | Tags: Internet of Things, Mobile Networks, Security, Usability | Links:
@inproceedings{Müller2017MoDeNA-AIMS,
title = {MoDeNA: Enhancing User Security for Devices in Wireless Personal and Local Area Networks},
author = {Robert Müller and Marcel Waldvogel and Corinna Schmitt},
url = {https://netfuture.ch/wp-content/uploads/2017/07/mueller2017modena.pdf
https://netfuture.ch/wp-content/uploads/2017/07/modena_presentation_aims_2017_07_12.pdf},
year = {2017},
date = {2017-07-10},
urldate = {1000-01-01},
booktitle = {Proceedings of AIMS 2017},
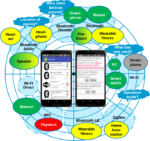
abstract = {Today most used devices are connected with each other building the Internet of Things (IoT). A variety of protocols are used depending on the underlying network infrastructure, application (e.g., Smart City, eHealth), and device capability. The judgment of the security feeling of the data sharing depends on personal settings (e.g., easy to use, encrypted transmission, anonymization support). MoDeNA – a Mobile Device Network Assistant – was developed offering an opportunity for understanding the judgment of security by bringing the user’s concerns and their technology understanding of used devices and protocols into relation. MoDeNA provides a transparent overview over the used wireless security of the user’s device giving concrete advices for improving the connection security and usability of mobile device security.},
keywords = {Internet of Things, Mobile Networks, Security, Usability},
pubstate = {published},
tppubtype = {inproceedings}
}
Marcel Waldvogel; Thomas Zink
X.509 User Certificate-based Two-Factor Authentication for Web Applications Proceedings Article
In: Müller, Paul; Neumair, Bernhard; Reiser, Helmut; Dreo Rodosek, Gabi (Ed.): 10. DFN-Forum Kommunikationstechnologien, 2017.
Abstract | BibTeX | Tags: Federated Services, Identity Management, Passwords, Security, Usability, Web Applications, X.509 | Links:
@inproceedings{Waldvogel-X509,
title = {X.509 User Certificate-based Two-Factor Authentication for Web Applications},
author = {Marcel Waldvogel and Thomas Zink},
editor = {Paul Müller and Bernhard Neumair and Helmut Reiser and Dreo Rodosek, Gabi},
url = {https://netfuture.ch/wp-content/uploads/2018/05/x509auth.pdf
},
year = {2017},
date = {2017-05-30},
urldate = {1000-01-01},
booktitle = {10. DFN-Forum Kommunikationstechnologien},
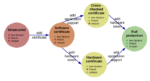
abstract = {An appealing property to researchers, educators, and students is the openness of the physical environment and IT infrastructure of their organizations. However, to the IT administration, this creates challenges way beyond those of a single-purpose business or administration. Especially the personally identifiable information or the power of the critical functions behind these logins, such as financial transactions or manipulating user accounts, require extra protection in the heterogeneous educational environment with single-sign-on. However, most web-based environments still lack a reasonable second-factor protection or at least the enforcement of it for privileged operations without hindering normal usage.
In this paper we introduce a novel and surprisingly simple yet extremely flexible way to implement two-factor authentication based on X.509 user certificates in web applications. Our solution requires only a few lines of code in web server configuration and none in the application source code for basic protection. Furthermore, since it is based on X.509 certificates, it can be easily combined with smartcards or USB cryptotokens to further enhance security.},
keywords = {Federated Services, Identity Management, Passwords, Security, Usability, Web Applications, X.509},
pubstate = {published},
tppubtype = {inproceedings}
}
In this paper we introduce a novel and surprisingly simple yet extremely flexible way to implement two-factor authentication based on X.509 user certificates in web applications. Our solution requires only a few lines of code in web server configuration and none in the application source code for basic protection. Furthermore, since it is based on X.509 certificates, it can be easily combined with smartcards or USB cryptotokens to further enhance security.
Thomas Zink; Marcel Waldvogel
X.509 User Certificate-based Two-Factor Authentication for Web Applications Technical Report
Distributed Systems Laboratory, University of Konstanz no. KN-2017-DISY-03, 2017.
Abstract | BibTeX | Tags: Certificates, Identity Management, Security, Two-Factor Authentication, Usability, Web Applications, X509 | Links:
@techreport{Zink2017X509,
title = {X.509 User Certificate-based Two-Factor Authentication for Web Applications},
author = {Thomas Zink and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2017/03/kn-2017-disy-03.pdf},
year = {2017},
date = {2017-03-14},
urldate = {1000-01-01},
number = {KN-2017-DISY-03},
institution = {Distributed Systems Laboratory, University of Konstanz},
abstract = {An appealing property to researchers, educators, and students is the openness
of the physical environment and IT infrastructure of their organizations. How-
ever, to the IT administration, this creates challenges way beyond those of a
single-purpose business or administration. Especially the personally identifiable
information or the power of the critical functions behind these logins, such as
financial transactions or manipulating user accounts, require extra protection in
the heterogeneous educational environment with single-sign-on. However, most
web-based environments still lack a reasonable second-factor protection or at
least the enforcement of it for privileged operations without hindering normal
usage.
In this paper we introduce a novel and surprisingly simple yet extremely flex-
ible way to implement two-factor authentication based on X.509 user certificates
in web applications. Our solution requires only a few lines of code in web server
configuration and none in the application source code for basic protection. Fur-
thermore, since it is based on X.509 certificates, it can be easily combined with
smartcards or USB cryptotokens to further enhance security.},
keywords = {Certificates, Identity Management, Security, Two-Factor Authentication, Usability, Web Applications, X509},
pubstate = {published},
tppubtype = {techreport}
}
of the physical environment and IT infrastructure of their organizations. How-
ever, to the IT administration, this creates challenges way beyond those of a
single-purpose business or administration. Especially the personally identifiable
information or the power of the critical functions behind these logins, such as
financial transactions or manipulating user accounts, require extra protection in
the heterogeneous educational environment with single-sign-on. However, most
web-based environments still lack a reasonable second-factor protection or at
least the enforcement of it for privileged operations without hindering normal
usage.
In this paper we introduce a novel and surprisingly simple yet extremely flex-
ible way to implement two-factor authentication based on X.509 user certificates
in web applications. Our solution requires only a few lines of code in web server
configuration and none in the application source code for basic protection. Fur-
thermore, since it is based on X.509 certificates, it can be easily combined with
smartcards or USB cryptotokens to further enhance security.
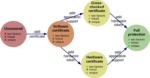
Robert Müller; Marcel Waldvogel; Corinna Schmitt
MoDeNA: Enhancing User Security for Devices in Wireless Personal and Local Area Networks Technical Report
Distributed Systems Laboratory, University of Konstanz no. KN-2017-DISY-02, 2017.
Abstract | BibTeX | Tags: Internet of Things, Security, Usability, Wireless, WPAN | Links:
@techreport{Mueller2017MoDeNA,
title = {MoDeNA: Enhancing User Security for Devices in Wireless Personal and Local Area Networks},
author = {Robert Müller and Marcel Waldvogel and Corinna Schmitt},
url = {https://netfuture.ch/wp-content/uploads/2017/03/kn-2017-disy-02.pdf},
year = {2017},
date = {2017-03-13},
urldate = {1000-01-01},
number = {KN-2017-DISY-02},
institution = {Distributed Systems Laboratory, University of Konstanz},
abstract = {Today most used devices are connected with each other building the Internet
of Things (IoT). They communicate with each other directly and share data with
a plethora of other devices indirectly by using the underlying network infrastruc-
ture. In both cases a variety of protocols are used depending on infrastructure,
application (e.g., Smart City, eHealth), and device capability. But the overall
concept of the data sharing is to do it in a secure manner so that different users
(e.g., consumer, facilities, provider) can gain benefits. But what does “secure
manner” means? This is a big question between the stakeholders, especially when
talking of wireless personal and local area networks (WPANs) and wireless local
area networks (WLAN), because the judgment of the security feeling depends
on personal settings (e.g., easy to use, encrypted transmission, anonymization
support). Therefore, MoDeNA – a Mobile Device Network Assistant – was de-
veloped offering an opportunity for understanding the judgment of security by
bringing the user’s concerns and their technology understanding of used devices
and protocols into relation. MoDeNA provides a transparent overview over the
used wireless security of the user’s device giving concrete advices for improving
the connection security, helping to improve usability of mobile device security. As
a use-case the smart city environment is used, because this is the most common
area, where many different WPAN and WLAN connections exist, supported by
different underlying infrastructures, and where secure data transmission is es-
sential, because it is an “open communication area”.},
keywords = {Internet of Things, Security, Usability, Wireless, WPAN},
pubstate = {published},
tppubtype = {techreport}
}
of Things (IoT). They communicate with each other directly and share data with
a plethora of other devices indirectly by using the underlying network infrastruc-
ture. In both cases a variety of protocols are used depending on infrastructure,
application (e.g., Smart City, eHealth), and device capability. But the overall
concept of the data sharing is to do it in a secure manner so that different users
(e.g., consumer, facilities, provider) can gain benefits. But what does “secure
manner” means? This is a big question between the stakeholders, especially when
talking of wireless personal and local area networks (WPANs) and wireless local
area networks (WLAN), because the judgment of the security feeling depends
on personal settings (e.g., easy to use, encrypted transmission, anonymization
support). Therefore, MoDeNA – a Mobile Device Network Assistant – was de-
veloped offering an opportunity for understanding the judgment of security by
bringing the user’s concerns and their technology understanding of used devices
and protocols into relation. MoDeNA provides a transparent overview over the
used wireless security of the user’s device giving concrete advices for improving
the connection security, helping to improve usability of mobile device security. As
a use-case the smart city environment is used, because this is the most common
area, where many different WPAN and WLAN connections exist, supported by
different underlying infrastructures, and where secure data transmission is es-
sential, because it is an “open communication area”.