Bevorzugen Sie Deutsch? Einige Artikel und mehr über mich gibt es auch in meiner Muttersprache.
Today, any device is networked, not only our personal devices, but anything from the fridge to the power plant. This implies endless possibilities, but also possibilities galore for anything to go wrong. Decades of thorough theoretical and hands-on experience enables me to guide you toward the right solution for anything networked. Learn more…
Recent technical essays
- Intel BE201: Getting Bluetooth to work on my Vivobook 14 Flip with Linux
 While trying to connect a Bluetooth device to my Asus Vivobook 14 Flip running under Debian Trixie, I noticed that Bluetooth did not work. Here’s an easy way to fix it.
While trying to connect a Bluetooth device to my Asus Vivobook 14 Flip running under Debian Trixie, I noticed that Bluetooth did not work. Here’s an easy way to fix it. - Tablet mode unrecognized on Asus Vivobook 14 Flip under Linux: Workaround
 My recently purchased Asus Vivobook 14 Flip (TP3407SA) does not flip into tablet (aka “slate”) mode when flipping the lid over. Here is a workaround for Gnome under Debian Trixie.
My recently purchased Asus Vivobook 14 Flip (TP3407SA) does not flip into tablet (aka “slate”) mode when flipping the lid over. Here is a workaround for Gnome under Debian Trixie. - No sound on Asus Vivobook 14 Flip under Linux: Fixed
 I recently purchased an Asus Vivobook 14 Flip (Model TP3407SA) for use under Linux. One of the obstacles I ran into: Playing sounds resulted in no audio, the device remained mute. However, it had worked under Windows. Time to investigate.
I recently purchased an Asus Vivobook 14 Flip (Model TP3407SA) for use under Linux. One of the obstacles I ran into: Playing sounds resulted in no audio, the device remained mute. However, it had worked under Windows. Time to investigate. - Obtaining TLS certificate information on the command line
 Here are a few helpful commands if you want to inspect and dump certificates for analysis or debugging:
Here are a few helpful commands if you want to inspect and dump certificates for analysis or debugging: - 50 years of microprocessor trend data
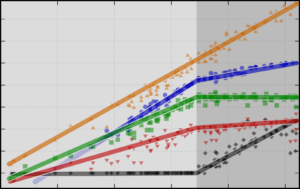 I recently wrote a (German) article including this graphic (in German). Here is an English version of it. Have fun!
I recently wrote a (German) article including this graphic (in German). Here is an English version of it. Have fun! - Compact Archive for WordPress
 The default WordPress «Archive» block becomes very long and narrow, when months accumulate. Here is an easy way to make it more compact.
The default WordPress «Archive» block becomes very long and narrow, when months accumulate. Here is an easy way to make it more compact. - DEFCON Voting Village 23 Panel
 There was a DEFCON Voting Village panel «If I can shop online, why can’t I vote online?» which I found extremely important to read or listen to. Not just for me, in fact, for anyone talking about electronic voting. Here… Read more: DEFCON Voting Village 23 Panel
There was a DEFCON Voting Village panel «If I can shop online, why can’t I vote online?» which I found extremely important to read or listen to. Not just for me, in fact, for anyone talking about electronic voting. Here… Read more: DEFCON Voting Village 23 Panel - Counting like a computer
 Computers are very good at counting. But usually only within narrow limits. Here is an insight into where these limits come from and what goes wrong when they are exceeded.
Computers are very good at counting. But usually only within narrow limits. Here is an insight into where these limits come from and what goes wrong when they are exceeded.
Let’s stay in touch!

Receive a mail whenever I publish a new post.
About 1-2 Mails per month, no Spam.
Archiv
- October 2025
- October 2024
- July 2024
- February 2024
- January 2024
- December 2023
- November 2023
- July 2023
- March 2023
- February 2023
- January 2023
- December 2022
- November 2022
- October 2022
- June 2022
- May 2022
- April 2022
- March 2022
- February 2022
- January 2022
- December 2021
- November 2021
- September 2021
- April 2021
- March 2021
- May 2020
- September 2019
- March 2019
- February 2019
- October 2018
- September 2018
- July 2018
- May 2018
- January 2018
- November 2017
- September 2017
- August 2017
- July 2017
- June 2017
- May 2017
- March 2017
- February 2017
- October 2016
- September 2016
- August 2016
- July 2016
- June 2016
- March 2016
- February 2016
- September 2015
- May 2015
- April 2015
- March 2015
- February 2015
- December 2014
- November 2014
- October 2014
- September 2014
- August 2014
- July 2014
- June 2014
- May 2014
- January 2014
- November 2013
- October 2013
- September 2013
- August 2013
- July 2013
- June 2013
- March 2013
- November 2012
- October 2012
- September 2012
- July 2012
- May 2012
- November 2011
- October 2011
- June 2011
- March 2011
- February 2011
- November 2010
- May 2010
- April 2010
- August 2009
- July 2009
- May 2009
- April 2009
- November 2008
- August 2008
- June 2008
- May 2008
- October 2007
- September 2007
- January 2007
- October 2006
- September 2006
- June 2006
- November 2004
- October 2004
- April 2004
- January 2004
- December 2003
- October 2003
- September 2003
- July 2003
- June 2003
- March 2003
- January 2003
- December 2002
- October 2002
- June 2002
- April 2002
- February 2002
- January 2002
- November 2001
- September 2001
- August 2001
- June 2001
- May 2001
- March 2001
- November 2000
- July 2000
- April 2000
- September 1999
- August 1999
- September 1998
- June 1998
- August 1997
- May 1997
- September 1995
- July 1989
Themen
Apache (4) Blockchain (17) Cloud Storage (12) Data Protection (5) Denial of Service (8) DNS (11) DNS-SD (6) DNSSEC (6) Fast Routers (20) Federated Services (6) Forwarding Lookups (4) FPGA (4) Hash Tables (8) Identity Management (6) Internet of Things (8) Intrusion Detection (6) JSXC (10) Linux (23) Mac OS X (5) Mobile Networks (7) MPLS (4) Multicast (15) Network Processors (4) NTP (6) NTS (6) Opportunistic Networks (9) Peer-to-Peer (23) Privacy (16) Quality of Service (9) Replication (4) Security (55) Service Discovery (5) Social Networks (8) Timestamps (6) TLS (8) TLS Interposer (6) Traffic Engineering (9) Trust (8) Ubuntu (7) Usability (6) Web Applications (11) WISEchat (5) XML (8) XMPP (11) Zeroconf (6)
