General audience texts
Besides the scholarly publications listed below, I have written many texts in English and German. My more notable German texts appeared by DNIP.ch. I also maintain document collections intended for a broad audience:
Scholarly publications
Up-to-date citation counts (provided by Google Scholar). List of patents granted.
2017
Robert Müller; Marcel Waldvogel; Daniel Kaiser
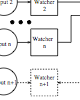
HomeCA: Scalable Secure IoT Network Integration Technical Report
Distributed Systems Laboratory, University of Konstanz no. KN-2017-DISY-01, 2017.
Abstract | BibTeX | Tags: Internet of Things, Security, Trust | Links:
@techreport{Mueller2017HomeCA,
title = {HomeCA: Scalable Secure IoT Network Integration},
author = {Robert Müller and Marcel Waldvogel and Daniel Kaiser},
url = {https://netfuture.ch/wp-content/uploads/2017/03/kn-2017-disy-01.pdf},
year = {2017},
date = {2017-03-12},
urldate = {1000-01-01},
number = {KN-2017-DISY-01},
institution = {Distributed Systems Laboratory, University of Konstanz},
abstract = {The sheer number of devices in the Internet of Things (IoT) makes efficient
device integration into a user’s home or corporate network a nightmare. More and
more owners lose control over their devices, often due to badly chosen security
defaults, software bugs, or broken protocols. The lack of user interface and the
long period of device usage increase the plight. We identify several root causes,
resulting in HomeCA, a comprehensive set of secure, vendor-neutral practices
based on existing protocols and open standards. These practices avoid most of
the common pitfalls, allow long-term permission management and secure usage,
and include support for automatic device integration. We also present a protocol
for ensuring secure key updates when acquiring device ownership.},
keywords = {Internet of Things, Security, Trust},
pubstate = {published},
tppubtype = {techreport}
}
device integration into a user’s home or corporate network a nightmare. More and
more owners lose control over their devices, often due to badly chosen security
defaults, software bugs, or broken protocols. The lack of user interface and the
long period of device usage increase the plight. We identify several root causes,
resulting in HomeCA, a comprehensive set of secure, vendor-neutral practices
based on existing protocols and open standards. These practices avoid most of
the common pitfalls, allow long-term permission management and secure usage,
and include support for automatic device integration. We also present a protocol
for ensuring secure key updates when acquiring device ownership.
2014
Daniel Kaiser; Marcel Waldvogel
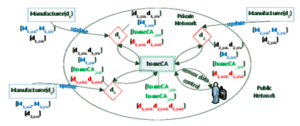
Adding Privacy to Multicast DNS Service Discovery Proceedings Article
In: Proceedings of IEEE TrustCom 2014 (IEEE EFINS 2014 workshop), 2014.
Abstract | BibTeX | Tags: DNS-SD, Multicast, Peer-to-Peer, Privacy, Service Discovery, Social Networks, Trust, Zeroconf | Links:
@inproceedings{Kaiser2014Adding,
title = {Adding Privacy to Multicast DNS Service Discovery},
author = {Daniel Kaiser and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2014/08/Kaiser2014Adding.pdf},
year = {2014},
date = {2014-09-24},
urldate = {1000-01-01},
booktitle = {Proceedings of IEEE TrustCom 2014 (IEEE EFINS 2014 workshop)},
abstract = {Multicast DNS Service Discovery (mDNS-SD), made fashionable through Apple’s \emph{Bonjour}, is a prevalent technique allowing service distribution and discovery in local networks without configuration (Zeroconf). Possible application areas are device synchronization, instant messaging, VoIP, file and screen sharing. It is very convenient for users, because they can connect to and offer services when they enter a network without any manual configuration. However, it requires the public exposure of the offering and requesting identities along with information about the offered and requested services, even when services do not need to be public. Some of the information published by the announcements can be very revealing, including complete lists of family members. In this paper we discuss the privacy problems arising when using mDNS-SD and present our privacy extension, which allows hiding all information published while still not requiring any network configuration except for an initial pairing. A key feature of our solution is the ease of upgrading existing systems, a must for widespread deployment and acceptance. To show the feasibility of our mDNS-SD privacy extension, we developed an implementation based on the open-source \emph{Avahi} daemon.},
keywords = {DNS-SD, Multicast, Peer-to-Peer, Privacy, Service Discovery, Social Networks, Trust, Zeroconf},
pubstate = {published},
tppubtype = {inproceedings}
}
Marcel Waldvogel; Jürgen Kollek
SIEGE: Service-Independent Enterprise-GradE protection against password scans Technical Report
University of Konstanz no. KN-2014-DiSy-001, 2014.
Abstract | BibTeX | Tags: Denial of Service, Intrusion Detection, Peer-to-Peer, Security, Trust | Links:
@techreport{waldvogel4siege,
title = {SIEGE: Service-Independent Enterprise-GradE protection against password scans},
author = {Marcel Waldvogel and Jürgen Kollek},
url = {https://netfuture.ch/wp-content/uploads/2014/01/waldvogel14siege.pdf},
year = {2014},
date = {2014-01-17},
urldate = {1000-01-01},
number = {KN-2014-DiSy-001},
institution = {University of Konstanz},
abstract = {Security is one of the main challenges today, complicated significantly by the heterogeneous and open academic networks with thousands of different applications. Botnet-based brute-force password scans are common security threat against the open academic networks. Common defenses are hard to maintain, error-prone and do not reliably discriminate between user error and coordinated attack. In this paper, we present a novel approach, which allows to secure many network services at once. By combining in-app tracking, local and global crowdsourcing, geographic information, and probabilistic user-bot distinction through differential password analysis, our PAM-based detection module can provide higher accuracy and faster blocking of bot- nets. In the future, we aim to make the mechanism even more generic and thus provide a distributed defense against one of the strongest threats against our infrastructure.},
keywords = {Denial of Service, Intrusion Detection, Peer-to-Peer, Security, Trust},
pubstate = {published},
tppubtype = {techreport}
}
2011
Pascal Gienger; Marcel Waldvogel
Polybius: Secure Web Single-Sign-On for Legacy Applications Proceedings Article
In: 4. DFN-Forum Kommunikationstechnologien, 2011.
Abstract | BibTeX | Tags: Cloud Storage, Identity Management, Security, Trust, Web Applications | Links:
@inproceedings{Gienger2011Polybius,
title = {Polybius: Secure Web Single-Sign-On for Legacy Applications},
author = {Pascal Gienger and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2011/gienger11polybius.pdf},
year = {2011},
date = {2011-06-20},
urldate = {1000-01-01},
booktitle = {4. DFN-Forum Kommunikationstechnologien},
abstract = {Web-based interfaces to applications in all domains of university life are surging. Given the diverse demands in and the histories of universities, combined with the rapid IT industry developments, all attempts at a sole all-encompassing platform for single-sign-on (SSO) will remain futile. In this paper, we present an architecture for a meta-SSO, which is able to seamlessly integrate with a wide variety of existing local sign-in and SSO mechanisms. It is therefore an excellent candidate for a university-wide all-purpose SSO system. Among the highlights are: No passwords are ever stored on disk, neither in the browser nor in the gateway; its basics have been implemented in a simple, yet versatile Apache module; and it can help reducing the impact of security problems anywhere in the system. It could even form the basis for secure inter-university collaborations and mutual outsourcing.},
keywords = {Cloud Storage, Identity Management, Security, Trust, Web Applications},
pubstate = {published},
tppubtype = {inproceedings}
}
2003
Germano Caronni; Marcel Waldvogel
Establishing Trust in Distributed Storage Providers Proceedings Article
In: Proceedings of Third IEEE International Conference on Peer-to-Peer Computing (P2P 2003), 2003.
Abstract | BibTeX | Tags: Cloud Storage, Peer-to-Peer, Replication, Trust | Links:
@inproceedings{Caronni2003Establishing,
title = {Establishing Trust in Distributed Storage Providers},
author = {Germano Caronni and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2003/caronni03establishing.pdf},
year = {2003},
date = {2003-09-01},
urldate = {1000-01-01},
booktitle = {Proceedings of Third IEEE International Conference on Peer-to-Peer Computing (P2P 2003)},
abstract = {Corporate IT as well as individuals show increasing interest in reliable outsourcing of storage infrastructure. Decentralized solutions with their resilience against partial outages are among the most attractive approaches. Irrespective of the form of the relationship, be it based on a contract or on the more flexible cooperative model, the problem of verifying whether someone promising to store one's data actually does so remains to be solved, especially in the presence of multiple replicas. In this paper, we introduce a lightweight mechanism that allows the \textit{data originator} or a dedicated \textit{verification agent} to build up trust in the \textit{replica holder} by means of protocols that do not require prior trust or key establishment. We show how naive versions of the protocol do not prevent cheating, and then strengthen it by adding means that make it economically attractive to be honest. This provides a foundation for further work in providing trustworthy distributed storage.},
keywords = {Cloud Storage, Peer-to-Peer, Replication, Trust},
pubstate = {published},
tppubtype = {inproceedings}
}
Ramaprabhu Janakiraman; Marcel Waldvogel; Qi Zhang
Indra: A Peer-to-Peer Approach to Network Intrusion Detection and Prevention Proceedings Article
In: Proceedings of IEEE WETICE 2003, Linz, Austria, 2003.
Abstract | BibTeX | Tags: Denial of Service, Security, Trust | Links:
@inproceedings{Janakiraman2003Indra,
title = {Indra: A Peer-to-Peer Approach to Network Intrusion Detection and Prevention},
author = {Ramaprabhu Janakiraman and Marcel Waldvogel and Qi Zhang},
url = {https://netfuture.ch/wp-content/uploads/2003/janakiraman03indra.pdf},
year = {2003},
date = {2003-01-01},
urldate = {1000-01-01},
booktitle = {Proceedings of IEEE WETICE 2003},
address = {Linz, Austria},
abstract = {While the spread of the Internet has made the network ubiquitous, it has also rendered networked systems vulnerable to malicious attacks orchestrated from anywhere. These attacks or intrusions typically start with attackers infiltrating a network through a vulnerable host and then launching further attacks on the local network or Intranet. Attackers rely on increasingly sophisticated techniques like using distributed attack sources and obfuscating their network addresses. On the other hand, software that guards against them remains rooted in traditional centralized techniques, presenting an easily-targeted single point of failure. Scalable, distributed network intrusion prevention techniques are sorely needed. We propose Indra---a distributed scheme based on sharing information between trusted peers in a network to guard the network as a whole against intrusion attempts. We present initial ideas for running Indra over a peer-to-peer infrastructure to distribute up-to-date rumors, facts, and trust information in a scalable way.},
keywords = {Denial of Service, Security, Trust},
pubstate = {published},
tppubtype = {inproceedings}
}