General audience texts
Besides the scholarly publications listed below, I have written many texts in English and German. My more notable German texts appeared by DNIP.ch. I also maintain document collections intended for a broad audience:
Scholarly publications
Up-to-date citation counts (provided by Google Scholar). List of patents granted.
2014
Muhammad Arshad Islam; Marcel Waldvogel
Analysis of Cognitive Radio Enabled Flooding in Opportunistic Networks Journal Article
In: International Journal of Communications, Network and System Sciences, vol. 7, pp. 212-222, 2014.
Abstract | BibTeX | Tags: Mobile Networks, Opportunistic Networks | Links:
@article{islam2014cognitive,
title = {Analysis of Cognitive Radio Enabled Flooding in Opportunistic Networks},
author = {Muhammad Arshad Islam and Marcel Waldvogel},
editor = {Scientific Research},
url = {https://netfuture.ch/wp-content/uploads/2015/06/islam2014cognitive.pdf},
doi = {http://dx.doi.org/10.4236/ijcns.2014.77023},
year = {2014},
date = {2014-07-01},
urldate = {1000-01-01},
journal = {International Journal of Communications, Network and System Sciences},
volume = {7},
pages = {212-222},
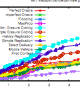
abstract = {Epidemic routing (Flooding) is considered as a simple routing protocol for opportunistic networks where the participants attempt to transmit whatever information they have to everyone who does not already have that information. However, it is plagued with disadvantages of resource scarcity as it exerts stress on available bandwidth as well as storage capacity of the devices in the network. Cognitive radio (CR) is one of the emerging technologies that can improve the bandwidth utilization by smart allocation of spectrum radio bands. Ideally speaking, a spectrum-aware cognitive radio is able to sense the local spectrum usage and adapt its own radio parameters accordingly. In this study, we have performed experiments to analyze the gains achieved by flooding protocol using cognitive radios of varying capabilities in opportunistic networks. We have performed expe- riments on three opportunistic networks obtained from real-life traces from different environments and presented results showing variance in delivery efficiency as well as cost incurred on those scenarios. Our results show that performance of flooding can be significantly improved using CRs in bandwidth-scarce environments; however, the improvement is not uniform with the increase in a number of available bands.},
keywords = {Mobile Networks, Opportunistic Networks},
pubstate = {published},
tppubtype = {article}
}
2012
Muhammad Arshad Islam; Marcel Waldvogel
Analyzing History Quality for Routing Purposes in Opportunistic Network Using Max-Flow Journal Article
In: Wireless Engineering and Technology, vol. 3, pp. 132-141, 2012.
Abstract | BibTeX | Tags: Opportunistic Networks | Links:
@article{Islam2012Analyzing,
title = {Analyzing History Quality for Routing Purposes in Opportunistic Network Using Max-Flow},
author = {Muhammad Arshad Islam and Marcel Waldvogel},
editor = {Scientific Research},
url = {https://netfuture.ch/wp-content/uploads/2018/10/islam2012analyzing.pdf},
year = {2012},
date = {2012-07-01},
urldate = {1000-01-01},
journal = {Wireless Engineering and Technology},
volume = {3},
pages = {132-141},
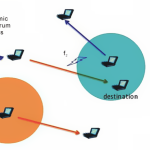
abstract = {Most of the existing opportunistic network routing protocols are based on some type of utility function that is directly or indirectly dependent on the past behavior of devices. The past behavior or history of a device is usually referred to as contacts that the device had in the past. Whatever may be the metric of history, most of these routing protocols work on the realistic premise that node mobility is not truly random. In contrast, there are several oracles based methods where such oracles assist these methods to gain access to information that is unrealistic in the real world. Although, such oracles are unrealistic, they can help to understand the nature and behavior of underlying networks. In this paper, we have analyzed the gap between these two extremes. We have performed max-flow computations on three different opportunistic networks and then compared the results by performing max-flow computations on history generated by the respective networks. We have found that the correctness of the history based prediction of history is dependent on the dense nature of the underlying network. Moreover, the history based prediction can deliver correct paths but cannot guarantee their absolute reliability.},
keywords = {Opportunistic Networks},
pubstate = {published},
tppubtype = {article}
}

2011
Muhammad Arshad Islam; Marcel Waldvogel
Prediction quality of contact history in opportunistic networks Proceedings Article
In: Wireless Days, 2011.
Abstract | BibTeX | Tags: Opportunistic Networks | Links:
@inproceedings{islam11prediction,
title = {Prediction quality of contact history in opportunistic networks},
author = {Muhammad Arshad Islam and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2013/11/islam11prediction.pdf},
year = {2011},
date = {2011-10-10},
urldate = {1000-01-01},
booktitle = {Wireless Days},
crossref = {DBLP:conf/wd/2011},
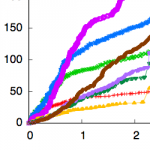
abstract = {Routing in opportunistic networks heavily relies on past behavior of the mobile devices it is formed of to predict their future and thus making routing decisions. While almost every protocol relies on this history, its prediction quality has never been studied in a realistic setting. Using extensive simulations on real traces, we are able to describe for the first time how well predictions can be. Unlike oracle-based prediction comparisons, we do not try to predict a contact, but compare the expected user result, namely message delivery probabilities. The analysis also provides guidance on the importance of multi-path routing and the path diversity required, as well as on the impact on forward error correction on the delivery probability. Our results show that the repetitive nature of path is directly proportional to the mobility extent of the devices and, consequently, history obtained from dense opportunistic networks is reliable.},
keywords = {Opportunistic Networks},
pubstate = {published},
tppubtype = {inproceedings}
}
Muhammad Arshad Islam; Marcel Waldvogel
Prediction Quality of Contact History in Opportunistic Networks Proceedings Article
In: IFIP Wireless Days 2011, 2011.
Abstract | BibTeX | Tags: Opportunistic Networks | Links:
@inproceedings{Islam2011Prediction,
title = {Prediction Quality of Contact History in Opportunistic Networks},
author = {Muhammad Arshad Islam and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2018/10/islam2011prediction.pdf},
year = {2011},
date = {2011-10-10},
urldate = {1000-01-01},
booktitle = {IFIP Wireless Days 2011},
abstract = {Routing in opportunistic networks heavily relies on past behavior of the mobile devices it is formed of to predict their future and thus making routing decisions. While almost every protocol relies on this history, its prediction quality has never been studied in a realistic setting. Using extensive simulations on real traces, we are able to describe for the first time how well predictions can be. Unlike oracle-based prediction comparisons, we do not try to predict a contact, but compare the expected user result, namely message delivery probabilities. The analysis also provides guidance on the importance of multi-path routing and the path diversity required, as well as on the impact on forward error correction on the delivery probability. Our results show that the repetitive nature of path is directly proportional to the mobility extent of the devices and, consequently, history obtained from dense opportunistic networks is reliable.},
keywords = {Opportunistic Networks},
pubstate = {published},
tppubtype = {inproceedings}
}

Arshad Islam; Marcel Waldvogel
Questioning flooding as a routing benchmark in Opportunistic Networks Proceedings Article
In: Proceedings of the Baltic Congress on Future Internet Communications, pp. 128-133, 2011.
Abstract | BibTeX | Tags: Mobile Networks, Opportunistic Networks | Links:
@inproceedings{Islam2011Questioning,
title = {Questioning flooding as a routing benchmark in Opportunistic Networks},
author = {Arshad Islam and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2011/islam11questioning.pdf},
year = {2011},
date = {2011-03-26},
urldate = {1000-01-01},
booktitle = {Proceedings of the Baltic Congress on Future Internet Communications},
pages = {128-133},
abstract = {Routing in Opportunistic Networks, as a relatively young discipline, still lacks coherent, simple and valid benchmarks. It is customary to use epidemic routing as performance benchmark for Opportunistic Networks. We identify and describe the current simulation practices that do not expose the shortcomings of flooding as an upper bound. In this paper to provide a step towards a routing benchmark, which is flexible, provides results close to an upper bound, is simple to implement, and thus might be a candidate for a common benchmark. This new method called EPO, does not suffer from bottlenecks that limit the performance of epidemic flooding, even when bandwidth is scarce. Our analysis shows that networks are not suffering from that much severe congestion as suggested by flooding and thus giving a better insight to the underlying network.},
keywords = {Mobile Networks, Opportunistic Networks},
pubstate = {published},
tppubtype = {inproceedings}
}

Arshad Islam; Marcel Waldvogel
Optimizing Message Delivery in Mobile-Opportunistic Networks Proceedings Article
In: Proceedings of the Baltic Congress on Future Internet Communications, pp. 134-141, 2011, ISBN: 978-1-4244-8511-6.
Abstract | BibTeX | Tags: Mobile Networks, Opportunistic Networks | Links:
@inproceedings{Islam2011Optimizing,
title = {Optimizing Message Delivery in Mobile-Opportunistic Networks},
author = {Arshad Islam and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2011/islam11optimizing.pdf},
isbn = {978-1-4244-8511-6},
year = {2011},
date = {2011-02-16},
urldate = {1000-01-01},
booktitle = {Proceedings of the Baltic Congress on Future Internet Communications},
pages = {134-141},
abstract = {The big challenge of routing in opportunistic mobile networks, overlooked by most researchers, is to not only find any path to the destination, but a path that is stable and powerful enough to actually carry the message. Few attempts addressed this problem, all of them under controlled scenarios, avoiding the complexity of real-world connectivity. As a result of our comparison of selected networks under a wide variety of realistic scenarios, we have not only been able to identify and describe favorable traits of protocols, but also necessary relationship of successful MON protocols with QoS routing in wired networks. We present a novel protocol, Nile, that performs both in dense as well as sparse networks. Nile is the first autonomous “controlled Hooding” protocol that keeps the link loads in check, to push replicas only on those paths that are both promising and may sustain more load. It is a multi path protocol that deploys replication based on heuristic for disjoint path calculation. Other protocols' performance, when simulated in real-world traces, highly depends on parameter choice. Nile, however, consistently performs among the top protocols without any external tuning and exerts far less overhead than other replication protocols.},
keywords = {Mobile Networks, Opportunistic Networks},
pubstate = {published},
tppubtype = {inproceedings}
}

2008
Sebastian Kay Belle; Muhammad Arshad Islam; Marcel Waldvogel
I Seek for Knowledge: Exploiting Social Properties in Mobile Ad-Hoc Networks Proceedings Article
In: In Proceedings of 1st IFIP Wireless Days 2008, pp. 1-5, 2008.
Abstract | BibTeX | Tags: Opportunistic Networks, Privacy, Social Networks | Links:
@inproceedings{Belle2008I,
title = {I Seek for Knowledge: Exploiting Social Properties in Mobile Ad-Hoc Networks},
author = {Sebastian Kay Belle and Muhammad Arshad Islam and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2008/belle08iseek.pdf},
year = {2008},
date = {2008-11-24},
urldate = {1000-01-01},
booktitle = {In Proceedings of 1st IFIP Wireless Days 2008},
pages = {1-5},
abstract = {New social networks are born each day, at a formal conference, at informal social gathering, at family reunions etc. Internet has already been playing an important role to let people socialize through online social websites. For many users, its still not the optimal way of interaction as one has to be very active updating their activities on the online profiles. With the easy access to mobile devices, modern technologies have now started to adopt to more human of socializing. As these mobile devices accompany their users almost all the time, they can record and observe their users behavior as well as gather information about their social circle. Therefore, they can help users to get information from contacts, that they potentially not even know. In this paper we put our efforts towards the initial design of such an architecture, we call \emph{Mergenet}, that will sniff for information around the user's surrounding, leveraging useful answers on their demand.
},
keywords = {Opportunistic Networks, Privacy, Social Networks},
pubstate = {published},
tppubtype = {inproceedings}
}
Sebastian Kay Belle; Marcel Waldvogel
Consistent Deniable Lying: Privacy in Mobile Social Networks Proceedings Article
In: Pervasive 2008 Workshop on Security and Privacy Issues in Mobile Phone Use (SPMU 2008), Sydney, Australia, 2008.
Abstract | BibTeX | Tags: Opportunistic Networks, Peer-to-Peer, Privacy, Security, Social Networks | Links:
@inproceedings{Belle2008Consistent,
title = {Consistent Deniable Lying: Privacy in Mobile Social Networks},
author = {Sebastian Kay Belle and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2008/belle08consistent.pdf},
year = {2008},
date = {2008-05-19},
urldate = {1000-01-01},
booktitle = {Pervasive 2008 Workshop on Security and Privacy Issues in Mobile Phone Use (SPMU 2008)},
address = {Sydney, Australia},
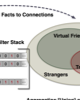
abstract = {Social networking is moving to mobile phones. This not only means continuous access, but also allows to link virtual and physical neighbourhood in novel ways. To make such systems useful, personal data such as lists of friends and interests need to be shared with more and frequently unknown people, posing a risk to your privacy. In this paper, we present our approach to social networking, Consistent Deniable Lying (CDL). Using easy-to-understand mechanisms and tuned to this environment, it enables you to meet new friends with joint interests while limiting exposure of your private data. Not only can it be generalised to include “friends of friends” (transitivity) into interest search, it allows you to plausibly refute any allegations of your claimed interests. Unlike prior work, we focus on the application to similarity finding and include the novel aspects of transitivity and deniability, which are key to success in social networks.},
keywords = {Opportunistic Networks, Peer-to-Peer, Privacy, Security, Social Networks},
pubstate = {published},
tppubtype = {inproceedings}
}
Arshad Islam; Marcel Waldvogel
Reality-Check for DTN Routing Algorithms Proceedings Article
In: ICDCSW ’08: Proceedings of the 2008 The 28th International Conference on Distributed Computing Systems Workshops, pp. 204–209, IEEE Computer Society, Washington, DC, USA, 2008, ISBN: 978-0-7695-3173-1.
Abstract | BibTeX | Tags: Opportunistic Networks | Links:
@inproceedings{Islam2008Reality-Check,
title = {Reality-Check for DTN Routing Algorithms},
author = {Arshad Islam and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2008/islam08reality.pdf},
isbn = {978-0-7695-3173-1},
year = {2008},
date = {2008-01-01},
urldate = {1000-01-01},
booktitle = {ICDCSW '08: Proceedings of the 2008 The 28th International Conference on Distributed Computing Systems Workshops},
pages = {204--209},
publisher = {IEEE Computer Society},
address = {Washington, DC, USA},
abstract = {Many applications of ad-hoc networks include intermittent connectivity. Anyone wishing to implement routing into her delay-tolerant network can select from a wide variation of options, but the choice is hard, as there is no strong comparative evidence to the relative performance of the algorithms. Every paper uses a different setting, mostly far from realistic. In our desire to improve the basis for decisions, we simulated a promising selection of DTN routing algorithms in three vastly different scenarios, all based on publicly available real-world traces. Using our open-source DTN simulator, we compare and analyse 11 routing techniques, then provide explanations for the behaviour and give advice for choosing a suitable mechanism. To our own surprise, the results challenge the conventional wisdom gained from synthetic simulations and poses the question whether the world is ready for DTNs.
},
keywords = {Opportunistic Networks},
pubstate = {published},
tppubtype = {inproceedings}
}