General audience texts
Besides the scholarly publications listed below, I have written many texts in English and German. My more notable German texts appeared by DNIP.ch. I also maintain document collections intended for a broad audience:
Scholarly publications
Up-to-date citation counts (provided by Google Scholar). List of patents granted.
2018
Sandra Domenique Ringmann; Hanno Langweg; Marcel Waldvogel
Requirements for legally compliant software based on the GDPR Proceedings Article
In: Cloud and Trusted Computing 2018 (C&TC 2018), 2018.
Abstract | BibTeX | Tags: Cloud Computing, Data Protection, GDPR, Privacy | Links:
@inproceedings{Ringmann2018Requirements,
title = {Requirements for legally compliant software based on the GDPR},
author = {Sandra Domenique Ringmann and Hanno Langweg and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2018/10/ringmann2018requirements.pdf},
year = {2018},
date = {2018-10-22},
urldate = {1000-01-01},
booktitle = {Cloud and Trusted Computing 2018 (C&TC 2018)},
abstract = {We identify 74 generic, reusable technical requirements based on the GDPR that can be applied to software products which process personal data. The requirements can be traced to corresponding articles and recitals of the GDPR and fulfil the key principles of lawfulness and transparency. Therefore, we present an approach to requirements engineering with regard to developing legally compliant software that satisfies the principles of privacy by design, privacy by default as well as security by design.},
keywords = {Cloud Computing, Data Protection, GDPR, Privacy},
pubstate = {published},
tppubtype = {inproceedings}
}
2015
Daniel Kaiser; Andreas Rain; Marcel Waldvogel; Holger Strittmatter
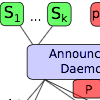
A Multicast-Avoiding Privacy Extension for the Avahi Zeroconf Daemon Proceedings Article
In: NetSys 2015, Gesellschaft für Informatik, 2015.
Abstract | BibTeX | Tags: DNS-SD, Privacy, Security, Zeroconf | Links:
@inproceedings{Kaiser2015Multicast-avoiding,
title = {A Multicast-Avoiding Privacy Extension for the Avahi Zeroconf Daemon},
author = {Daniel Kaiser and Andreas Rain and Marcel Waldvogel and Holger Strittmatter},
url = {https://netfuture.ch/wp-content/uploads/2014/12/kaiser2015multicast-avoiding.pdf
https://netfuture.ch/wp-content/uploads/2015/03/mdns-security-poster.pdf},
year = {2015},
date = {2015-03-10},
urldate = {1000-01-01},
booktitle = {NetSys 2015},
publisher = {Gesellschaft für Informatik},
abstract = {In today’s local networks, a significant amount of traffic is caused by Multicast packets, such as Multicast DNS Service Discovery (mDNS-SD), a widespread technique used for configurationless service distribution and discovery. It suffers from two major problems inherent in multicast: privacy and network load. We present a privacy extension for the Avahi Zeroconf Daemon that tackles both problems while being very efficient.},
keywords = {DNS-SD, Privacy, Security, Zeroconf},
pubstate = {published},
tppubtype = {inproceedings}
}
Marcel Waldvogel; Thomas Zink
Boost DNS Privacy, Reliability, and Efficiency with opDNS Safe Query Elimination Proceedings Article
In: NetSys 2015, Gesellschaft für Informatik, 2015.
Abstract | BibTeX | Tags: DNS, Privacy, Security | Links:
@inproceedings{Waldvogel2015Boost,
title = {Boost DNS Privacy, Reliability, and Efficiency with opDNS Safe Query Elimination},
author = {Marcel Waldvogel and Thomas Zink},
url = {https://netfuture.ch/wp-content/uploads/2014/12/waldvogel2015boost.pdf
https://netfuture.ch/wp-content/uploads/2015/03/opdns-poster.pdf},
year = {2015},
date = {2015-03-10},
urldate = {1000-01-01},
booktitle = {NetSys 2015},
publisher = {Gesellschaft für Informatik},
abstract = {SRV records, DNSSEC, and DANE among others fortify the Domain Name System as the central information hub behind the Internet. Largely hidden from the end user, an increasing number of protocol and trust decisions are contingent on DNS. Neglect or attacks on DNS have much more impact today than ever, now endangering security far beyond denial of service. Opportunistic Persistent DNS (opDNS) addresses these problems by abandoning pessimistic caching and eliminating unnecessary traffic. Today’s DNS infrastructure relies on the hosts forgetting and refreshing DNS records in relatively short time. In conjunction with TLS, opDNS greatly reduces the number of queries and in turn increases privacy, reliability, and efficiency. Even with DNS lookups all but eliminated for frequently visited secure services, changes to the server addresses will be recognized almost immediately, unlike standard DNS. We will show how end systems can take advantage of opDNS without having to wait for support by server operators or application developers, enabling the most effective way of deployment.},
keywords = {DNS, Privacy, Security},
pubstate = {published},
tppubtype = {inproceedings}
}

2014
Daniel Kaiser; Matthias Fratz; Marcel Waldvogel; Valentin Dietrich; Holger Strittmatter
Stateless DNS Technical Report
University of Konstanz Technical Report, no. KN-2014-DISY-004, 2014.
Abstract | BibTeX | Tags: DNS-SD, Multicast, Peer-to-Peer, Privacy, Zeroconf | Links:
@techreport{Kaiser2014Stateless,
title = {Stateless DNS},
author = {Daniel Kaiser and Matthias Fratz and Marcel Waldvogel and Valentin Dietrich and Holger Strittmatter},
url = {https://netfuture.ch/wp-content/uploads/2015/02/kaiser14stateless.pdf},
year = {2014},
date = {2014-12-31},
urldate = {1000-01-01},
number = {KN-2014-DISY-004},
institution = {University of Konstanz},
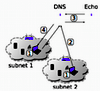
abstract = {Several network applications, like service discovery, file discovery in P2P networks, distributed hash tables, and distributed caches, use or would benefit from distributed key value stores. The Domain Name System (DNS) is a key value store which has a huge infrastructure and is accessible from almost everywhere.
Nevertheless storing information in this database makes it necessary to be authoritative for a domain or to be “registered” with a domain, e.g. via DynDNS, to be allowed to store and update resource records using
nsupdate. Applications like the ones listed above would greatly benefit from a configurationless approach, giving users a much more convenient experience.
In this report we describe a technique we call Stateless DNS, which allows to store data in the cache of the local DNS server. It works without any infrastructure updates; it just needs our very simple, configurationless echo DNS server that can parse special queries containing information desired to be stored, process this information, and generate DNS answers in a way that the DNS cache that was asked the special query will store the desired information. Because all this happens in the authority zone of our echo DNS server, we do not cause cache poisoning. Our tests show that Stateless DNS works with a huge number of public DNS servers.},
type = {Technical Report},
keywords = {DNS-SD, Multicast, Peer-to-Peer, Privacy, Zeroconf},
pubstate = {published},
tppubtype = {techreport}
}
Nevertheless storing information in this database makes it necessary to be authoritative for a domain or to be “registered” with a domain, e.g. via DynDNS, to be allowed to store and update resource records using
nsupdate. Applications like the ones listed above would greatly benefit from a configurationless approach, giving users a much more convenient experience.
In this report we describe a technique we call Stateless DNS, which allows to store data in the cache of the local DNS server. It works without any infrastructure updates; it just needs our very simple, configurationless echo DNS server that can parse special queries containing information desired to be stored, process this information, and generate DNS answers in a way that the DNS cache that was asked the special query will store the desired information. Because all this happens in the authority zone of our echo DNS server, we do not cause cache poisoning. Our tests show that Stateless DNS works with a huge number of public DNS servers.
Daniel Kaiser; Marcel Waldvogel
Adding Privacy to Multicast DNS Service Discovery Proceedings Article
In: Proceedings of IEEE TrustCom 2014 (IEEE EFINS 2014 workshop), 2014.
Abstract | BibTeX | Tags: DNS-SD, Multicast, Peer-to-Peer, Privacy, Service Discovery, Social Networks, Trust, Zeroconf | Links:
@inproceedings{Kaiser2014Adding,
title = {Adding Privacy to Multicast DNS Service Discovery},
author = {Daniel Kaiser and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2014/08/Kaiser2014Adding.pdf},
year = {2014},
date = {2014-09-24},
urldate = {1000-01-01},
booktitle = {Proceedings of IEEE TrustCom 2014 (IEEE EFINS 2014 workshop)},
abstract = {Multicast DNS Service Discovery (mDNS-SD), made fashionable through Apple’s \emph{Bonjour}, is a prevalent technique allowing service distribution and discovery in local networks without configuration (Zeroconf). Possible application areas are device synchronization, instant messaging, VoIP, file and screen sharing. It is very convenient for users, because they can connect to and offer services when they enter a network without any manual configuration. However, it requires the public exposure of the offering and requesting identities along with information about the offered and requested services, even when services do not need to be public. Some of the information published by the announcements can be very revealing, including complete lists of family members. In this paper we discuss the privacy problems arising when using mDNS-SD and present our privacy extension, which allows hiding all information published while still not requiring any network configuration except for an initial pairing. A key feature of our solution is the ease of upgrading existing systems, a must for widespread deployment and acceptance. To show the feasibility of our mDNS-SD privacy extension, we developed an implementation based on the open-source \emph{Avahi} daemon.},
keywords = {DNS-SD, Multicast, Peer-to-Peer, Privacy, Service Discovery, Social Networks, Trust, Zeroconf},
pubstate = {published},
tppubtype = {inproceedings}
}
Daniel Kaiser; Marcel Waldvogel
Efficient Privacy Preserving Multicast DNS Service Discovery Proceedings Article
In: Workshop on Privacy-Preserving Cyberspace Safety and Security (CSS), 2014.
Abstract | BibTeX | Tags: DNS-SD, Multicast, Privacy, Service Discovery, Zeroconf | Links:
@inproceedings{Kaiser2014Efficient,
title = {Efficient Privacy Preserving Multicast DNS Service Discovery},
author = {Daniel Kaiser and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2014/08/Kaiser2014Efficient.pdf},
year = {2014},
date = {2014-08-23},
urldate = {1000-01-01},
booktitle = {Workshop on Privacy-Preserving Cyberspace Safety and Security (CSS)},
abstract = {In today’s local networks a significant amount of traffic is caused by Multicast DNS Service Discovery (mDNS-SD), a prevalent technique used for configurationless service distribution and discovery. It allows users to offer and use services like device synchronization, file sharing, and chat, when joining a local network without any manual configuration. While this is very convenient, it requires the public exposure of the offering and requesting identities along with information about the offered and requested services, even when services do not need to be public. Some of the information published by the announcements can be very revealing, including complete lists of family members. Another problem is the huge amount of multicast traffic caused, which is especially relevant for large WiFi networks.
In this paper we present a privacy extension that does not publish private information and reduces the number of packets sent while still not requiring any network configuration except for an initial pairing per pair of users. A key feature of our solution is the ease of upgrading existing systems, a must for widespread deployment and acceptance. We developed an implementation based on the open-source Avahi daemon to show the feasibility of our privacy extension. Our solution grants tunable privacy and reduces multicast traffic without affecting user experience.},
keywords = {DNS-SD, Multicast, Privacy, Service Discovery, Zeroconf},
pubstate = {published},
tppubtype = {inproceedings}
}
In this paper we present a privacy extension that does not publish private information and reduces the number of packets sent while still not requiring any network configuration except for an initial pairing per pair of users. A key feature of our solution is the ease of upgrading existing systems, a must for widespread deployment and acceptance. We developed an implementation based on the open-source Avahi daemon to show the feasibility of our privacy extension. Our solution grants tunable privacy and reduces multicast traffic without affecting user experience.
Marcel Waldvogel; Klaus Herberth; Daniel Scharon
Chat in Forschung und Lehre? Sicher! Journal Article
In: DFN-Mitteilungen, no. 86, pp. 38-41, 2014, ISSN: 0177-6894.
Abstract | BibTeX | Tags: Federated Services, Privacy, Security, Social Networks, Video Chat, Web Applications, XMPP | Links:
@article{Waldvogel2014Chat,
title = {Chat in Forschung und Lehre? Sicher!},
author = {Marcel Waldvogel and Klaus Herberth and Daniel Scharon},
url = {https://netfuture.ch/wp-content/uploads/2014/05/Waldvogel2014Chat.pdf
https://www.dfn.de/publikationen/dfnmitteilungen/},
issn = {0177-6894},
year = {2014},
date = {2014-05-23},
urldate = {1000-01-01},
journal = {DFN-Mitteilungen},
number = {86},
pages = {38-41},
abstract = {Instant Messaging, Audio- und Videoanrufe, kurz Chat, ist aus unserem täglichen Leben nicht mehr wegzudenken. Die meisten nutzen dafür geschlossene Systeme, die für den Privatgebrauch bequem sind, für den dienstlichen Einsatz in Forschung und Lehre aber an Datenschutz und Privatsphäre scheitern. Das muss nicht so sein: Auf Basis des offenen, föderierten Extensible Messaging and Presence Protocols (XMPP) bietet WISEchat webbasiert und -integriert die Sicherheit, den Komfort und die Erweiterbarkeit, die eine moderne Hochschule braucht. Die Hintergründe, Vorteile und Zukunftssicherheit erläutern wir anhand einiger konkreter Beispiele.},
keywords = {Federated Services, Privacy, Security, Social Networks, Video Chat, Web Applications, XMPP},
pubstate = {published},
tppubtype = {article}
}
Klaus Herberth; Daniel Kaiser; Daniel Scharon; Marcel Waldvogel
Interaktive Webseiten für effiziente Kooperation auf Basis offener Standards Technical Report
University of Konstanz no. KN-2014-DiSy-002, 2014.
Abstract | BibTeX | Tags: Collaboration, Privacy, Security, Social Networks, Video Chat, Web Applications, XMPP | Links:
@techreport{herberth14interaktive,
title = {Interaktive Webseiten für effiziente Kooperation auf Basis offener Standards},
author = {Klaus Herberth and Daniel Kaiser and Daniel Scharon and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2014/01/herberth14interaktive.pdf},
year = {2014},
date = {2014-01-18},
urldate = {1000-01-01},
number = {KN-2014-DiSy-002},
institution = {University of Konstanz},
abstract = {Homepages von Forschern, Informationsseiten der Verwaltung, Support- und Beratungsseiten, Webmail oder sonstige Groupware begleiten uns bei der täglichen Arbeit im akademischen Umfeld. Unmittelbare Rückfragen zu den Inhalten oder Interaktionen sind jedoch weiterhin nicht möglich; eine Integration von Direktkontakten wäre häufig angenehm und hilfreich. Swoosch, unsere Javascript-Bibliothek auf Basis der offenen Standards XMPP, HTML5 und WebRTC, bietet hier Abhilfe. Auf einfachste Weise lassen sich so bestehende Webseiten und -anwendungen transparent um Funktionen für Instant Messaging inklusive Videokonferenz erweitern und neue Beratungs- und Kommunikationskanäle eröffnen, bei denen die Privatsphäre durch Ende-zu-Ende-Verschlüsselung gesichert ist. Die Erfahrungen in den Testinstallationen zeigten nahtlose Integration, niedrige Eintrittsschwelle, Geschwindigkeit und Benutzerfreundlichkeit. Durch die inhärente Föderation von XMPP ist der Dienst auch über die Organisationsgrenzen hinaus einsetzbar. Dank seiner offenen Standards ist Swoosch beinahe beliebig integrier- und erweiterbar.},
keywords = {Collaboration, Privacy, Security, Social Networks, Video Chat, Web Applications, XMPP},
pubstate = {published},
tppubtype = {techreport}
}
2012
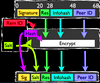
Thomas Zink; Marcel Waldvogel
Efficient BitTorrent handshake obfuscation Proceedings Article
In: Proceedings of the First Workshop on P2P and Dependability, ACM, 2012, ISBN: 978-1-4503-1148-9.
Abstract | BibTeX | Tags: Peer-to-Peer, Privacy, Security, Traffic Engineering | Links:
@inproceedings{Zink2012Efficient,
title = {Efficient BitTorrent handshake obfuscation},
author = {Thomas Zink and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2015/02/zink2012efficient.pdf},
isbn = {978-1-4503-1148-9},
year = {2012},
date = {2012-05-08},
urldate = {1000-01-01},
booktitle = {Proceedings of the First Workshop on P2P and Dependability},
publisher = {ACM},
abstract = {During the last decade, large scale media distribution populated peer-to-peer applications. Faced with ever increasing volumes of traffic, legal threats by copyright holders, and QoS demands of customers, network service providers are urged to apply traffic classification and shaping techniques. These highly integrated systems require constant maintenance, introduce legal issues, and violate both the net neutrality and end-to-end principles.
Clients see their freedom and privacy attacked. Users, application programmers, and even commercial service providers laboriously strive to hide their interests and circumvent classification techniques. While changing the network infrastructure is by nature very complex, and it reacts only slowly to new conditions, updating and distributing software between users is easy and practically instantaneous.
We present a new obfuscation extension to the BitTorrent protocol, which allows signature free handshaking. The extension requires no changes to the infrastructure and is fully backwards compatible. With only little change to client software, contemporary classification techniques can be rendered ineffective.},
keywords = {Peer-to-Peer, Privacy, Security, Traffic Engineering},
pubstate = {published},
tppubtype = {inproceedings}
}
Clients see their freedom and privacy attacked. Users, application programmers, and even commercial service providers laboriously strive to hide their interests and circumvent classification techniques. While changing the network infrastructure is by nature very complex, and it reacts only slowly to new conditions, updating and distributing software between users is easy and practically instantaneous.
We present a new obfuscation extension to the BitTorrent protocol, which allows signature free handshaking. The extension requires no changes to the infrastructure and is fully backwards compatible. With only little change to client software, contemporary classification techniques can be rendered ineffective.
2010
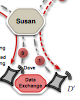
Sebastian Kay Belle; Oliver Haase; Marcel Waldvogel
CallForge: Call Anonymity in Cellular Networks Technical Report
University of Konstanz 2010.
Abstract | BibTeX | Tags: Mobile Networks, Privacy, Security | Links:
@techreport{Belle2010CallForge,
title = {CallForge: Call Anonymity in Cellular Networks},
author = {Sebastian Kay Belle and Oliver Haase and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2010/belle10callforge.pdf},
year = {2010},
date = {2010-05-19},
urldate = {1000-01-01},
booktitle = {PERVASIVE 2008 Workshop on Security and Privacy in Spontaneous Interaction and Mobile Phone Use (SPMU 2008)},
institution = {University of Konstanz},
abstract = {In cellular networks, the locations of all subscribers are continously tracked even when they only passively carry their mobile devices with them. This privacy sensitive data can be an invaluable source of information, not only for benevolent parties. We therefore present CallForge, the concept of a location management scheme that preserves the subscribers' anonymity -- in many cases even while they participate in a phone call -- as well as a theoretical analysis of the approach. CallForge improves on PathForge, a previously presented location management scheme, and as such is based on ID switching that we have combined with the emulation of a media break within a single call set-up procedure. We have analyzed and compared the anonymity of PathForge and CallForges, and shown that CallForge consistently provides superior anonymity. CallForge can be implemented entirely in the end device and run on existing network infrastructure without any modifications.},
keywords = {Mobile Networks, Privacy, Security},
pubstate = {published},
tppubtype = {techreport}
}
2009
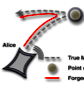
Sebastian Kay Belle; Marcel Waldvogel
PathForge: Faithful Anonymization of Movement Data Proceedings Article
In: Proceedings of the 1st ACM workshop on Networking, systems, and applications for mobile handhelds (MobiHeld ’09), pp. 63-64, 2009.
Abstract | BibTeX | Tags: Mobile Networks, Privacy, Security | Links:
@inproceedings{Belle2009PathForge,
title = {PathForge: Faithful Anonymization of Movement Data},
author = {Sebastian Kay Belle and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2009/belle09pathforge.pdf},
year = {2009},
date = {2009-08-17},
urldate = {1000-01-01},
booktitle = {Proceedings of the 1st ACM workshop on Networking, systems, and applications for mobile handhelds (MobiHeld '09)},
pages = {63-64},
abstract = {For most mobile networks, providers need the current position of their users to provide efficient service. The resulting motion data is not only an invaluable source for analyzing traffic or flow patterns, but also for tracking an individual's whereabouts, even without their knowledge. Today, many carry at least one mobile networked device with them wherever they go, day and night. The resulting motion data can be used to reveal the most intimate details of our lives, making this information extremely privacy sensitive. In this paper, we present PathForge, a lightweight solution, which not only fulfills the provider's efficiency requirement, but continues to allow flow pattern analysis, yet provides full privacy for users when not actively involved in a call.},
keywords = {Mobile Networks, Privacy, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
2008
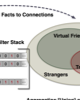
Sebastian Kay Belle; Muhammad Arshad Islam; Marcel Waldvogel
I Seek for Knowledge: Exploiting Social Properties in Mobile Ad-Hoc Networks Proceedings Article
In: In Proceedings of 1st IFIP Wireless Days 2008, pp. 1-5, 2008.
Abstract | BibTeX | Tags: Opportunistic Networks, Privacy, Social Networks | Links:
@inproceedings{Belle2008I,
title = {I Seek for Knowledge: Exploiting Social Properties in Mobile Ad-Hoc Networks},
author = {Sebastian Kay Belle and Muhammad Arshad Islam and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2008/belle08iseek.pdf},
year = {2008},
date = {2008-11-24},
urldate = {1000-01-01},
booktitle = {In Proceedings of 1st IFIP Wireless Days 2008},
pages = {1-5},
abstract = {New social networks are born each day, at a formal conference, at informal social gathering, at family reunions etc. Internet has already been playing an important role to let people socialize through online social websites. For many users, its still not the optimal way of interaction as one has to be very active updating their activities on the online profiles. With the easy access to mobile devices, modern technologies have now started to adopt to more human of socializing. As these mobile devices accompany their users almost all the time, they can record and observe their users behavior as well as gather information about their social circle. Therefore, they can help users to get information from contacts, that they potentially not even know. In this paper we put our efforts towards the initial design of such an architecture, we call \emph{Mergenet}, that will sniff for information around the user's surrounding, leveraging useful answers on their demand.
},
keywords = {Opportunistic Networks, Privacy, Social Networks},
pubstate = {published},
tppubtype = {inproceedings}
}
Sebastian Kay Belle; Marcel Waldvogel
Consistent Deniable Lying: Privacy in Mobile Social Networks Proceedings Article
In: Pervasive 2008 Workshop on Security and Privacy Issues in Mobile Phone Use (SPMU 2008), Sydney, Australia, 2008.
Abstract | BibTeX | Tags: Opportunistic Networks, Peer-to-Peer, Privacy, Security, Social Networks | Links:
@inproceedings{Belle2008Consistent,
title = {Consistent Deniable Lying: Privacy in Mobile Social Networks},
author = {Sebastian Kay Belle and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2008/belle08consistent.pdf},
year = {2008},
date = {2008-05-19},
urldate = {1000-01-01},
booktitle = {Pervasive 2008 Workshop on Security and Privacy Issues in Mobile Phone Use (SPMU 2008)},
address = {Sydney, Australia},
abstract = {Social networking is moving to mobile phones. This not only means continuous access, but also allows to link virtual and physical neighbourhood in novel ways. To make such systems useful, personal data such as lists of friends and interests need to be shared with more and frequently unknown people, posing a risk to your privacy. In this paper, we present our approach to social networking, Consistent Deniable Lying (CDL). Using easy-to-understand mechanisms and tuned to this environment, it enables you to meet new friends with joint interests while limiting exposure of your private data. Not only can it be generalised to include “friends of friends” (transitivity) into interest search, it allows you to plausibly refute any allegations of your claimed interests. Unlike prior work, we focus on the application to similarity finding and include the novel aspects of transitivity and deniability, which are key to success in social networks.},
keywords = {Opportunistic Networks, Peer-to-Peer, Privacy, Security, Social Networks},
pubstate = {published},
tppubtype = {inproceedings}
}