General audience texts
Besides the scholarly publications listed below, I have written many texts in English and German. My more notable German texts appeared by DNIP.ch. I also maintain document collections intended for a broad audience:
Scholarly publications
Up-to-date citation counts (provided by Google Scholar). List of patents granted.
2018
Matthias Held; Marcel Waldvogel
Fighting Ransomware with Guided Undo Proceedings Article
In: Proceedings of NISK 2018, 2018.
Abstract | BibTeX | Tags: Cloud Storage, Intrusion Detection, Ransomware, Replication, Security, Usability, Web Applications | Links:
@inproceedings{Held2018FightingRansomware,
title = {Fighting Ransomware with Guided Undo},
author = {Matthias Held and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2018/07/held2018fightingransomware.pdf
https://netfuture.ch/wp-content/uploads/2018/09/ransomware_detection.pdf
https://netfuture.ch/wp-content/uploads/2018/09/2018-ransomware.odp},
year = {2018},
date = {2018-09-18},
urldate = {1000-01-01},
booktitle = {Proceedings of NISK 2018},
abstract = {Ransomware attacks are rare, yet catastrophic. On closer inspection, they differ from other malware infections: Given appropriate preparation, they do not need to be caught on first sight, but can be undone later. However, current ransomware protection follows the beaten path of anti-malware copying their fallacies. We show how the move to personal cloud storage allows for a paradigm shift in ransomware protection: exceptional attack isolation, perfect elimination of false positive alerts, and simplified recovery.
In this paper, we analyze the necessary operations for ransomware, extend existing ransomware taxonomy, and verify them against real-world malware samples. We analyze the costs and benefits of moving ransomware detection to versioned personal cloud storage. Our content, meta data, and behavior analysis paired with a `guilt by association' capability greatly improve the false positive rate, but the guided undo make this rate all but inconsequential. Even though the user now carries a new burden, it comes with clear responsibilities and benefits, while being freed from questionable duties, resulting in a win-win situation for user experience and detection quality.
},
keywords = {Cloud Storage, Intrusion Detection, Ransomware, Replication, Security, Usability, Web Applications},
pubstate = {published},
tppubtype = {inproceedings}
}
In this paper, we analyze the necessary operations for ransomware, extend existing ransomware taxonomy, and verify them against real-world malware samples. We analyze the costs and benefits of moving ransomware detection to versioned personal cloud storage. Our content, meta data, and behavior analysis paired with a `guilt by association’ capability greatly improve the false positive rate, but the guided undo make this rate all but inconsequential. Even though the user now carries a new burden, it comes with clear responsibilities and benefits, while being freed from questionable duties, resulting in a win-win situation for user experience and detection quality.
2013
Sebastian Graf; Wolfgang Miller; Marcel Waldvogel
Utilizing Photo Sharing Websites for Cloud Storage Backends Technical Report
University of Konstanz, Distributed Systems Laboratory no. KN-2013-DiSy-02, 2013.
Abstract | BibTeX | Tags: Cloud Storage | Links:
@techreport{Graf2013PhotoSharing,
title = {Utilizing Photo Sharing Websites for Cloud Storage Backends},
author = {Sebastian Graf and Wolfgang Miller and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2013/03/graf13photo-sharing.pdf},
year = {2013},
date = {2013-08-14},
urldate = {1000-01-01},
number = {KN-2013-DiSy-02},
institution = {University of Konstanz, Distributed Systems Laboratory},
abstract = {Cloud Storages combine high availability with the unencessity to maintain any own infrastructure and all-time availability. A wide field of different providers offer a flexible portfolio for any technical need and financial possibility. Yet, the possibilities of different cloud storage providers have all one issue in common: Basic storage is cheap whereas the costs increase with the storage consumed adhering the pay-as-you-go paradigm. Photo sharing websites such as Facebook, Picasa-Web, and Flickr leverage from own cloud infrastructure and offer unlimited storage for less or no charge. Obviously pictures can be used to store information in, which has been used for steganography and watermarking at low data rates. We propose a general framework for storing large amounts of data, its data density and error-correcting mechanisms tunable to the properties of the photo sharing website of your choice. Our cost-performance-analysis shows that photo sharing websites compare favorably to professional cloud storage services such as Amazon S3. Thanks to the integration of our software as a backend to the widely-used jClouds framework, everyone can now use photo sharing websites as one component for low-cost purposes, including archival.},
keywords = {Cloud Storage},
pubstate = {published},
tppubtype = {techreport}
}

Sebastian Graf; Andreas Rain; Daniel Scharon; Marcel Waldvogel
Utilizing Cloud Storages for iSCSI: Is Security really expensive? Technical Report
University of Konstanz, Distributed Systems Laboratory no. KN-2013-DiSy-01, 2013.
Abstract | BibTeX | Tags: Cloud Storage, Security | Links:
@techreport{Graf2013iSCSI,
title = {Utilizing Cloud Storages for iSCSI: Is Security really expensive?},
author = {Sebastian Graf and Andreas Rain and Daniel Scharon and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2013/08/graf13isci.pdf},
year = {2013},
date = {2013-03-03},
urldate = {1000-01-01},
number = {KN-2013-DiSy-01},
institution = {University of Konstanz, Distributed Systems Laboratory},
abstract = {Cloud storage promises unlimited, flexible and cheap storages, including all-time availability and accessibility with the help of various technologies. Free-of-charge offers for endusers allure customers the same way as professional, pay-as-you-go storages do. The delocalization of the data provokes security concerns especially regarding the confidentiality of the data. Even though encryption offers a straight-forward solution to this problem, the performance questions its applicability when it comes to the utilization of professional storage-approaches like iSCSI. In this white-paper, we propose a utilization of NoSQL-based cloud-storages like Amazon S3 or Microsoft Azure for iSCSI. We evaluate the costs of a direct, bucket-based encryption and show, that in complex systems like iSCSI, the distance to the cloud represents the bottleneck instead of the encryption. Performance-boosting techniques like prefetching and caching improve the access and result in no practical overhead within such an utilization. Based on our own developed fully Java-based iSCSI target (jSCSI) and jClouds, our prototype represents, to the best of our knowledge, the first, free available, cloud-deployable iSCSI.},
keywords = {Cloud Storage, Security},
pubstate = {published},
tppubtype = {techreport}
}
2012
Sebastian Graf; Patrick Lang; Stefan A. Hohenadel; Marcel Waldvogel
Versatile Key Management for Secure Cloud Storage Proceedings Article
In: IEEE 31st Symposium on Reliable Distributed Systems, SRDS 2012, pp. 469-474, 2012.
BibTeX | Tags: Cloud Storage, Security | Links:
@inproceedings{Graf2012Versatile,
title = {Versatile Key Management for Secure Cloud Storage},
author = {Sebastian Graf and Patrick Lang and Stefan A. Hohenadel and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2012/graf12versatile.pdf},
year = {2012},
date = {2012-10-08},
urldate = {1000-01-01},
booktitle = {IEEE 31st Symposium on Reliable Distributed Systems, SRDS 2012},
pages = {469-474},
crossref = {DBLP:conf/srds/2012},
keywords = {Cloud Storage, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
Sebastian Graf; Jörg Eisele; Marcel Waldvogel; Marc Strittmatter
A Legal and Technical Perspective on Secure Cloud Storage Proceedings Article
In: 5. DFN-Forum Kommunikationstechnologien: Verteilte Systeme im Wissenschaftsbereich, pp. 63-72, 2012.
Abstract | BibTeX | Tags: Cloud Storage, Security | Links:
@inproceedings{Graf2012Legal,
title = {A Legal and Technical Perspective on Secure Cloud Storage},
author = {Sebastian Graf and Jörg Eisele and Marcel Waldvogel and Marc Strittmatter},
url = {https://netfuture.ch/wp-content/uploads/2012/graf12legal.pdf},
year = {2012},
date = {2012-05-20},
urldate = {1000-01-01},
booktitle = {5. DFN-Forum Kommunikationstechnologien: Verteilte Systeme im Wissenschaftsbereich},
pages = {63-72},
crossref = {DBLP:conf/dfn/2012},
abstract = {Cloud infrastructures are nowadays an irreplaceable component within modern IT-infrastructures.
Due to their representing abstraction regarding the physical execution framework from the deployment of the service, clouds not offer valuable attributes like scalability, environmental protection by best utilization of hardware resources, pay-as-you-go billing but also problem fields especially when it comes to the storage of confidential data. More concise, secure utilization of common cloud infrastructures like provided by Google, Microsoft or Amazon generate not only an indistinguishable impact to computer science but also to law science. As a consequence, based upon the confidentially of the data and the different methods and parties able to access this information, the safeness of the data must not only be provided by applying technical security measures upon the cloud-stored information but also by the investigation of legal issues going along with the flexibility of the cloud. To fill this gap, our contribution bases upon two pillars:<ul><li>We discuss legal issues going along with the storage of (especially confidential) data on cloud infrastructures provided by third parties.</li><li>Besides the legal issues, we further investigate technical measures how to ensure secure data storage on a technical level utilizing the benefits of cloud infrastructures (namely the scalability and availability).</li></ul>Based upon these investigations, we propose a technical model for secure cloud storage and interpret the measures against common aspects from the area of jurisprudence. Besides, we show that the area of jurisprudence still offers many open issues related to cloud based storage which represent a challenge for end-users as well as complex institutions like universities.},
keywords = {Cloud Storage, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
Due to their representing abstraction regarding the physical execution framework from the deployment of the service, clouds not offer valuable attributes like scalability, environmental protection by best utilization of hardware resources, pay-as-you-go billing but also problem fields especially when it comes to the storage of confidential data. More concise, secure utilization of common cloud infrastructures like provided by Google, Microsoft or Amazon generate not only an indistinguishable impact to computer science but also to law science. As a consequence, based upon the confidentially of the data and the different methods and parties able to access this information, the safeness of the data must not only be provided by applying technical security measures upon the cloud-stored information but also by the investigation of legal issues going along with the flexibility of the cloud. To fill this gap, our contribution bases upon two pillars:
- We discuss legal issues going along with the storage of (especially confidential) data on cloud infrastructures provided by third parties.
- Besides the legal issues, we further investigate technical measures how to ensure secure data storage on a technical level utilizing the benefits of cloud infrastructures (namely the scalability and availability).

Michael Simon; Marcel Waldvogel; Sven Schober; Saher Semaan; Martin Nussbaumer
bwIDM: Föderieren auch nicht-webbasierter Dienste auf Basis von SAML Proceedings Article
In: 5. DFN-Forum Kommunikationstechnologien: Verteilte Systeme im Wissenschaftsbereich, pp. 119-128, 2012.
Abstract | BibTeX | Tags: Cloud Storage, Identity Management, Security | Links:
@inproceedings{Simon2012bwIDM,
title = {bwIDM: Föderieren auch nicht-webbasierter Dienste auf Basis von SAML},
author = {Michael Simon and Marcel Waldvogel and Sven Schober and Saher Semaan and Martin Nussbaumer},
url = {https://netfuture.ch/wp-content/uploads/2012/simon12bwidm.pdf},
year = {2012},
date = {2012-05-20},
urldate = {1000-01-01},
booktitle = {5. DFN-Forum Kommunikationstechnologien: Verteilte Systeme im Wissenschaftsbereich},
pages = {119-128},
crossref = {DBLP:conf/dfn/2012},
abstract = {Zur organisationsübergreifenden Nutzung von IT-Diensten werden Dienstföderationen gebildet. Dabei kann das Nutzerkonto der sogenannten Heimateinrichtung auch zum Zugriff auf nicht-lokale Dienste genutzt werden. Während die Integration webbasierter Dienste in Föderationen mit SAML und beispielsweise Shibboleth mittlerweile in vielen Anwendungsbereichen allgegenwärtig ist, fällt die Integration nicht-webbasierter IT-Dienste schwer. Existierende Ansätze, mit denen sich prinzipiell auch nicht-webbasierte Dienste integrieren lassen, erfüllen essentielle Anforderungen nicht und/oder sind nach ihrem heutigen Entwicklungsstand noch nicht betriebsfähig. In diesem Papier werden zwei Verfahren für nicht-webbasierte, föderative Dienstzugriffe (Moonshot und PAM/ECP) evaluiert und notwendige Erweiterungen zur Sicherstellung der Betriebsfa ̈higkeit vorgestellt. Ein implementierter Proof-of-Concept zeigt die Umsetzbarkeit der Lösung.},
keywords = {Cloud Storage, Identity Management, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
2011
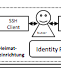
Pascal Gienger; Marcel Waldvogel
Polybius: Secure Web Single-Sign-On for Legacy Applications Proceedings Article
In: 4. DFN-Forum Kommunikationstechnologien, 2011.
Abstract | BibTeX | Tags: Cloud Storage, Identity Management, Security, Trust, Web Applications | Links:
@inproceedings{Gienger2011Polybius,
title = {Polybius: Secure Web Single-Sign-On for Legacy Applications},
author = {Pascal Gienger and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2011/gienger11polybius.pdf},
year = {2011},
date = {2011-06-20},
urldate = {1000-01-01},
booktitle = {4. DFN-Forum Kommunikationstechnologien},
abstract = {Web-based interfaces to applications in all domains of university life are surging. Given the diverse demands in and the histories of universities, combined with the rapid IT industry developments, all attempts at a sole all-encompassing platform for single-sign-on (SSO) will remain futile. In this paper, we present an architecture for a meta-SSO, which is able to seamlessly integrate with a wide variety of existing local sign-in and SSO mechanisms. It is therefore an excellent candidate for a university-wide all-purpose SSO system. Among the highlights are: No passwords are ever stored on disk, neither in the browser nor in the gateway; its basics have been implemented in a simple, yet versatile Apache module; and it can help reducing the impact of security problems anywhere in the system. It could even form the basis for secure inter-university collaborations and mutual outsourcing.},
keywords = {Cloud Storage, Identity Management, Security, Trust, Web Applications},
pubstate = {published},
tppubtype = {inproceedings}
}
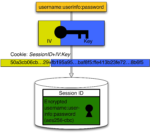
Sebastian Graf; Marc Kramis; Marcel Waldvogel
Treetank, Designing A Versioned XML Storage Proceedings Article
In: XML Prague ’11, 2011.
Abstract | BibTeX | Tags: Cloud Storage, XML | Links:
@inproceedings{Graf2011Treetank,
title = {Treetank, Designing A Versioned XML Storage},
author = {Sebastian Graf and Marc Kramis and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2011/graf11treetank.pdf},
year = {2011},
date = {2011-03-26},
urldate = {1000-01-01},
booktitle = {XML Prague '11},
abstract = {XML underlies the same constant modification scenarios like any other resource especially in flexible environments like the WWW. Therefore, intelligent handling of versioned XML is mandatory. Due to the structural nature of XML, the efficient storage of changes in the data and therefor in the tree needs new paradigms regarding efficient storage and effective retrieval operations. We present a node granular XML versioning approach which relies on the independence of the storage and the versioning system. Different layers which have the ability to satisfy specific aspects of a node-granular versioning storage guarantee this independence. Results prove that our architecture offers efficient handling of consecutive changes within all modification scenarios while not restricting XML regarding its usage. Hence, our prototype system handles even huge XML instances while ensuring equal access to each revision of the data.},
keywords = {Cloud Storage, XML},
pubstate = {published},
tppubtype = {inproceedings}
}
2008
Sebastian Graf; Marc Kramis; Marcel Waldvogel
Distributing XML with Focus on Parallel Evaluation Proceedings Article
In: Sixth International Workshop on Databases, Information Systems and Peer-to-Peer Computing (DBISP2P 2008), pp. 55-67, 2008.
Abstract | BibTeX | Tags: Cloud Storage, XML | Links:
@inproceedings{Graf2008Distributing,
title = {Distributing XML with Focus on Parallel Evaluation},
author = {Sebastian Graf and Marc Kramis and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2008/graf08distributing.pdf},
year = {2008},
date = {2008-08-23},
urldate = {1000-01-01},
booktitle = {Sixth International Workshop on Databases, Information Systems and Peer-to-Peer Computing (DBISP2P 2008)},
pages = {55-67},
abstract = {In contrast to relational databases the distribution of document-centric XML is not well researched. While there are some suggestions on how to split and distribute large XML documents, these approaches do not consider the parallel query evaluation. In this paper, we present and compare five different algorithms to search after suitable split nodes in
a large XML document. We then describe how to distribute extractable substructures over a fixed number of peers and how to query these peers in parallel to retrieve the final result. In addition, we analyse the impact of our splitting algorithms with respect to scalability for two different XPath expression classes on three well-known XML data sets. We conclude this paper with an outlook on future work, including result ordering during parallel query execution and dynamic re-distribution of XML fragments to new peers due to updates.},
keywords = {Cloud Storage, XML},
pubstate = {published},
tppubtype = {inproceedings}
}
a large XML document. We then describe how to distribute extractable substructures over a fixed number of peers and how to query these peers in parallel to retrieve the final result. In addition, we analyse the impact of our splitting algorithms with respect to scalability for two different XPath expression classes on three well-known XML data sets. We conclude this paper with an outlook on future work, including result ordering during parallel query execution and dynamic re-distribution of XML fragments to new peers due to updates.
2007
Marc Kramis; Volker Wildi; Bastian Lemke; Sebastian Graf; Halldór Janetzko; Marcel Waldvogel
jSCSI – A Java iSCSI Initiator Proceedings Article
In: Paper for: Jazoon’07 – Internationale Konferenz für Java-Technologie, Universität Konstanz, 2007.
Abstract | BibTeX | Tags: Cloud Storage | Links:
@inproceedings{Kramis07jscsi,
title = {jSCSI – A Java iSCSI Initiator},
author = {Marc Kramis and Volker Wildi and Bastian Lemke and Sebastian Graf and Halldór Janetzko and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2013/12/jscsi_slides.pdf},
year = {2007},
date = {2007-01-01},
urldate = {1000-01-01},
booktitle = {Paper for: Jazoon'07 – Internationale Konferenz für Java-Technologie},
publisher = {Universität Konstanz},
abstract = {Accessing persistent storage from Java usually means talking to the file system through the frugal Java file system abstraction, i.e., the File class. Currently, there is no platform-independent way to directly talk to a single local or remote storage device, yet alone a device pool. jSCSI aims to fill this gap by implementing the iSCSI protocol right in Java. We believe that firstly, Java is mature enough to cleanly implement well-performing low-level storage protocols and secondly, that it would be very convenient to plug a terabyte-sized iSCSI RAID into the local network and immediately connect to it from any JVM.},
keywords = {Cloud Storage},
pubstate = {published},
tppubtype = {inproceedings}
}

2003
Germano Caronni; Marcel Waldvogel
Establishing Trust in Distributed Storage Providers Proceedings Article
In: Proceedings of Third IEEE International Conference on Peer-to-Peer Computing (P2P 2003), 2003.
Abstract | BibTeX | Tags: Cloud Storage, Peer-to-Peer, Replication, Trust | Links:
@inproceedings{Caronni2003Establishing,
title = {Establishing Trust in Distributed Storage Providers},
author = {Germano Caronni and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2003/caronni03establishing.pdf},
year = {2003},
date = {2003-09-01},
urldate = {1000-01-01},
booktitle = {Proceedings of Third IEEE International Conference on Peer-to-Peer Computing (P2P 2003)},
abstract = {Corporate IT as well as individuals show increasing interest in reliable outsourcing of storage infrastructure. Decentralized solutions with their resilience against partial outages are among the most attractive approaches. Irrespective of the form of the relationship, be it based on a contract or on the more flexible cooperative model, the problem of verifying whether someone promising to store one's data actually does so remains to be solved, especially in the presence of multiple replicas. In this paper, we introduce a lightweight mechanism that allows the \textit{data originator} or a dedicated \textit{verification agent} to build up trust in the \textit{replica holder} by means of protocols that do not require prior trust or key establishment. We show how naive versions of the protocol do not prevent cheating, and then strengthen it by adding means that make it economically attractive to be honest. This provides a foundation for further work in providing trustworthy distributed storage.},
keywords = {Cloud Storage, Peer-to-Peer, Replication, Trust},
pubstate = {published},
tppubtype = {inproceedings}
}