General audience texts
Besides the scholarly publications listed below, I have written many texts in English and German. My more notable German texts appeared by DNIP.ch. I also maintain document collections intended for a broad audience:
Scholarly publications
Up-to-date citation counts (provided by Google Scholar). List of patents granted.
2014
Marcel Waldvogel; Jürgen Kollek
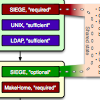
SIEGE: Service-Independent Enterprise-GradE protection against password scans Technical Report
University of Konstanz no. KN-2014-DiSy-001, 2014.
Abstract | BibTeX | Tags: Denial of Service, Intrusion Detection, Peer-to-Peer, Security, Trust | Links:
@techreport{waldvogel4siege,
title = {SIEGE: Service-Independent Enterprise-GradE protection against password scans},
author = {Marcel Waldvogel and Jürgen Kollek},
url = {https://netfuture.ch/wp-content/uploads/2014/01/waldvogel14siege.pdf},
year = {2014},
date = {2014-01-17},
urldate = {1000-01-01},
number = {KN-2014-DiSy-001},
institution = {University of Konstanz},
abstract = {Security is one of the main challenges today, complicated significantly by the heterogeneous and open academic networks with thousands of different applications. Botnet-based brute-force password scans are common security threat against the open academic networks. Common defenses are hard to maintain, error-prone and do not reliably discriminate between user error and coordinated attack. In this paper, we present a novel approach, which allows to secure many network services at once. By combining in-app tracking, local and global crowdsourcing, geographic information, and probabilistic user-bot distinction through differential password analysis, our PAM-based detection module can provide higher accuracy and faster blocking of bot- nets. In the future, we aim to make the mechanism even more generic and thus provide a distributed defense against one of the strongest threats against our infrastructure.},
keywords = {Denial of Service, Intrusion Detection, Peer-to-Peer, Security, Trust},
pubstate = {published},
tppubtype = {techreport}
}
2012
Thomas Zink; Marcel Waldvogel
BitTorrent traffic obfuscation: A chase towards semantic traffic identification Proceedings Article
In: 12th IEEE International Conference on Peer-to-Peer Computing, P2P 2012, pp. 126-137, 2012.
Abstract | BibTeX | Tags: Denial of Service, Peer-to-Peer, Security, Traffic Engineering | Links:
@inproceedings{Zink2012BitTorrent,
title = {BitTorrent traffic obfuscation: A chase towards semantic traffic identification},
author = {Thomas Zink and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2012/zink12bittorrent.pdf},
year = {2012},
date = {2012-09-03},
urldate = {1000-01-01},
booktitle = {12th IEEE International Conference on Peer-to-Peer Computing, P2P 2012},
pages = {126-137},
crossref = {DBLP:conf/p2p/2012},
abstract = {With the beginning of the 21st century emerging peer-to-peer networks ushered in a new era of large scale media exchange. Faced with ever increasing volumes of traffic, legal threats by copyright holders, and QoS demands of customers, network service providers are urged to apply traffic classification and shaping techniques. These systems usually are highly integrated to satisfy the harsh restrictions present in network infrastructure. They require constant maintenance and updates. Additionally, they have legal issues and violate both the net neutrality and end-to-end principles. On the other hand, clients see their freedom and privacy attacked. As a result, users, application programmers, and even commercial service providers laboriously strive to hide their interests and circumvent classification techniques. In this user vs. ISP war, the user side has a clear edge. While changing the network infrastructure is by nature very complex, and only slowly reacts to new conditions, updating and distributing software between users is easy and practically instantaneous. In this paper we discuss how state-of-the-art traffic classification systems can be circumvented with little effort. We present a new obfuscation extension to the BitTorrent protocol that allows signature free handshaking. The extension requires no changes to the infrastructure and is fully backwards compatible. With only little change to client software, contemporary classification techniques are rendered ineffective. We argue that future traffic classification must not rely on restricted local syntax information but instead must exploit global communication patterns and protocol semantics in order to be able to keep pace with rapid application and protocol changes.},
keywords = {Denial of Service, Peer-to-Peer, Security, Traffic Engineering},
pubstate = {published},
tppubtype = {inproceedings}
}

2007
Marcel Waldvogel; Tobias Köck
Light-weight End-to-End QoS as DoS Prevention Proceedings Article
In: Proceedings of IEEE LCN 2007, 2007.
Abstract | BibTeX | Tags: Denial of Service, Quality of Service, Security | Links:
@inproceedings{Waldvogel2007Light-weight,
title = {Light-weight End-to-End QoS as DoS Prevention},
author = {Marcel Waldvogel and Tobias Köck},
url = {https://netfuture.ch/wp-content/uploads/2006/waldvogel06light-weight.pdf},
year = {2007},
date = {2007-09-01},
urldate = {1000-01-01},
booktitle = {Proceedings of IEEE LCN 2007},
abstract = {Despite decades of QoS research and many years of DoS defence work, neither group of proponents have been able to get their results included into mainstream Internet service. It seems that demand for either solution exists, but individually, they seem to be just below the cost/ benefit threshold. This paper proposes a first step into a common solution, where combined and extended interests will hopefully allow us to surpass this threshold. While there are still some open issues, we hope to not only pro- pose a basic working mechanism but also provide fresh ideas to start thinking off the beaten path. Our main contribution is to create a lightweight, end-to-end binding between path and service, which is then used as a basis to associate fur- ther attributes and mechanisms to this binding. As a result, both DoS defence and QoS can be achieved with stateless routers and only with prior consent of receiving the end sys- tems, short, achieving several of the IntServ advantages in a DiffServ-style system, i.e., avoiding per-connection state.},
keywords = {Denial of Service, Quality of Service, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
2006
Marcel Waldvogel; Michael Muncan; Mahak Patidar
Stealth DoS Proceedings Article
In: Proceedings of IEEEslash IST Workshop on Monitoring, Attack Detection, and Mitigation (MonAM 2006), 2006.
Abstract | BibTeX | Tags: Denial of Service, Security | Links:
@inproceedings{Waldvogel2006Stealth,
title = {Stealth DoS},
author = {Marcel Waldvogel and Michael Muncan and Mahak Patidar},
url = {https://netfuture.ch/wp-content/uploads/2006/waldvogel06stealth.pdf},
year = {2006},
date = {2006-09-28},
urldate = {1000-01-01},
booktitle = {Proceedings of IEEEslash IST Workshop on Monitoring, Attack Detection, and Mitigation (MonAM 2006)},
abstract = {Users and providers increasingly disagree on what Denial of Service (DoS) is. For example, an ISP might consider large multimedia downloads an attack to overload its infrastructure or have it pay high interconnection fees. On the other hand, a user will certainly consider selective bandwidth reduction that is used by ISPs as a countermea- sure, as a DoS measure. Given the nature of their business relationship, neither side is likely to openly admit that they are fighting each other. In this paper we attempt to formalise the concept of Stealth DoS, including listing mechanisms that may be used at high speed. We concentrate on mechanisms that might be used in one particular area, voice over IP (VoIP). We start evaluating them under the different aspects, including their cost, political suitability and the likelihood for countermeasures to succeed. We expect that this will give both sides better insight on their options and plea for peace, hopefully in an attempt to avoid and open war.},
keywords = {Denial of Service, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
2004
Sean Rooney; Christopher J. Giblin; Marcel Waldvogel; Paul T. Hurley
Identifying a Distributed Denial of Service (DDoS) Attack within a Network and Defending Against such an Attack Miscellaneous
International Patent TWI332159, 2004.
Abstract | BibTeX | Tags: Denial of Service, Security | Links:
@misc{Rooney2004Identifying,
title = {Identifying a Distributed Denial of Service (DDoS) Attack within a Network and Defending Against such an Attack},
author = {Sean Rooney and Christopher J. Giblin and Marcel Waldvogel and Paul T. Hurley},
url = {https://netfuture.ch/wp-content/uploads/2017/01/us2006010389a1.pdf},
year = {2004},
date = {2004-04-05},
urldate = {1000-01-01},
abstract = {The invention provides methods, apparatus and systems for detecting distributed denial of service (DDoS) attacks within the Internet by sampling packets at a point or points in Internet backbone connections to determine a packet metric parameter. The packet metric parameter which might comprise the volume of packets received is analysed over selected time intervals with respect to specified geographical locations in which the hosts transmitting the packets are located. The expected behaviour can be employed to identify traffic distortions revealing a DDoS attack. In a complementary aspect, the invention provides a method of authenticating packets at routers in order to elevate the QoS of authenticated packets. This method can be used to block or filter packets and can be used in conjunction with the DDoS attack detection system to defend against DDoS attacks within the Internet in a distributed manner.},
howpublished = {International Patent TWI332159},
keywords = {Denial of Service, Security},
pubstate = {published},
tppubtype = {misc}
}
2003
Ramaprabhu Janakiraman; Marcel Waldvogel; Qi Zhang
Indra: A Peer-to-Peer Approach to Network Intrusion Detection and Prevention Proceedings Article
In: Proceedings of IEEE WETICE 2003, Linz, Austria, 2003.
Abstract | BibTeX | Tags: Denial of Service, Security, Trust | Links:
@inproceedings{Janakiraman2003Indra,
title = {Indra: A Peer-to-Peer Approach to Network Intrusion Detection and Prevention},
author = {Ramaprabhu Janakiraman and Marcel Waldvogel and Qi Zhang},
url = {https://netfuture.ch/wp-content/uploads/2003/janakiraman03indra.pdf},
year = {2003},
date = {2003-01-01},
urldate = {1000-01-01},
booktitle = {Proceedings of IEEE WETICE 2003},
address = {Linz, Austria},
abstract = {While the spread of the Internet has made the network ubiquitous, it has also rendered networked systems vulnerable to malicious attacks orchestrated from anywhere. These attacks or intrusions typically start with attackers infiltrating a network through a vulnerable host and then launching further attacks on the local network or Intranet. Attackers rely on increasingly sophisticated techniques like using distributed attack sources and obfuscating their network addresses. On the other hand, software that guards against them remains rooted in traditional centralized techniques, presenting an easily-targeted single point of failure. Scalable, distributed network intrusion prevention techniques are sorely needed. We propose Indra---a distributed scheme based on sharing information between trusted peers in a network to guard the network as a whole against intrusion attempts. We present initial ideas for running Indra over a peer-to-peer infrastructure to distribute up-to-date rumors, facts, and trust information in a scalable way.},
keywords = {Denial of Service, Security, Trust},
pubstate = {published},
tppubtype = {inproceedings}
}
2002
Marcel Waldvogel
GOSSIB vs. IP Traceback Rumors Proceedings Article
In: 18th Annual Computer Security Applications Conference (ACSAC 2002), pp. 5–13, 2002.
Abstract | BibTeX | Tags: Denial of Service, Security | Links:
@inproceedings{Waldvogel2002GOSSIB,
title = {GOSSIB vs. IP Traceback Rumors},
author = {Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2002/waldvogel02gossib.pdf},
year = {2002},
date = {2002-01-01},
urldate = {1000-01-01},
booktitle = {18th Annual Computer Security Applications Conference (ACSAC 2002)},
pages = {5--13},
abstract = { To identify sources of distributed denial-of-service attacks, path traceback mechanisms have been proposed. Traceback mechanisms relying on probabilistic packet marking (PPM) have received most attention, as they are easy to implement and deploy incrementally. In this paper, we introduce a new concept, namely groups of strongly similar birthdays (GOSSIB), that can be used by to obtain effects similar to a successful birthday attack on PPM schemes. The original and most widely known IP traceback mechanism, compressed edge fragment sampling (CEFS), was developed by Savage et al. We analyze the effects of an attacker using GOSSIB against CEFS and show that the attacker can seed misinformation much more effiently than the network is able to contribute real traceback information. Thus, GOSSIB will render PPM effctively useless. It can be expected that GOSSIB has similar effcts on other PPM traceback schemes and that standard modifiations to the systems will not solve the problem.},
keywords = {Denial of Service, Security},
pubstate = {published},
tppubtype = {inproceedings}
}