-
Counting like a computer

Computers are very good at counting. But usually only within narrow limits. Here is an insight into where these limits come from and what goes wrong when they are exceeded.
-
SMTP Smuggling Status

«SMTP Smuggling» is a vulnerability that allows to circumvent some mail checks at the receiver and therefore will allow additional spam and/or phishing messages through. Here is the list of what we currently know.
-
Post Quantum and Homomorphic Encryption made easy
Major challenges in computer and information security are the advent of quantum computers and the need to trust your data to (cloud) service providers. New cryptography is supposed to help, but they look daunting. At their core, however, they are just children’s riddles. An introduction to Lattice cryptography and Learning With Errors.
-
«The Cloud» does not exist
What is cloud anyway? And why are not all clouds the same? An overview to create clarity. The topic of the cloud is currently on everyone’s lips again, and decisions are pending in many places. Clarity is essential for assessing the impact on individuals, the economy and society. That’s why we’re starting a small series…
-
Offline digital cash?
The question of using digital money in the event of a network outage comes up again and again. Here is an overview of the options and their pros and cons.
-
NTS and dynamic IP addresses
Good news is that NTS relies on DNS names, no longer “naked” IP addresses. But what happens when the DNS name changes, pointing to a different IP address? A look at the protocol, the Chrony source, and the implications.
-
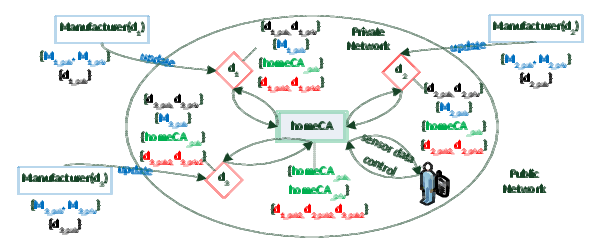
HomeCA: Scalable Secure IoT Network Integration
-
Ransomware is different

While most types of malware such as viruses and botnets try to lay low for as long as they can, while doing their nasty work, ransomware is eager to do its work ASAP. Because of this, ransomware does not need to embed itself as deeply into the system. All it wants to do is to…
