 While most types of malware such as viruses and botnets try to lay low for as long as they can, while doing their nasty work, ransomware is eager to do its work ASAP. Because of this, ransomware does not need to embed itself as deeply into the system. All it wants to do is to encrypt as many important files as possible without being disturbed and then display that famous notice that you have to pay some Bitcoins and hope to get your precious files back.
While most types of malware such as viruses and botnets try to lay low for as long as they can, while doing their nasty work, ransomware is eager to do its work ASAP. Because of this, ransomware does not need to embed itself as deeply into the system. All it wants to do is to encrypt as many important files as possible without being disturbed and then display that famous notice that you have to pay some Bitcoins and hope to get your precious files back.
Diesen Artikel gibt es auch auf Deutsch als “Ransomware ist anders”
We will explore these differences and their impact in the following chapters: Paying ransom, why and how ransomware works, and what we can do against it. We will also show that looking at ransomware from an entirely different angle makes things quite a bit easier and more user friendly: Try not to do the impossibly by striving for the perfect detection, which is too late anyway, as the software has already embedded itself into your system. Instead, reduce the user’s recovery effort to one click, ideally.
Should I pay ransom?
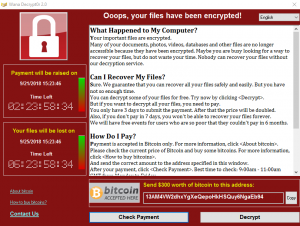 No! Please don’t! Don’t even consider it. If you already have, flush that thought down the toilet. Now. I’ll be waiting for you in the meantime.
No! Please don’t! Don’t even consider it. If you already have, flush that thought down the toilet. Now. I’ll be waiting for you in the meantime.
There are at least four reasons against paying:
- First of all, you have now way of knowing whether the other side will honor your payment. Some strains of ransomware do not include enough information for the payment process to be linked back to you and the decryption process. Paying may be futile.
- Even if the software provides a way to get back your data, you’re dealing with criminals here, if you have not yet noticed. Why should you trust those anonymous criminals? They do not even have the goal to build up a track-record of being a honest criminal. Paying may not be honored.
- Even if you are lucky enough that you will get your data back: Every single payment increases the benefit for those criminals, convincing them to start more and more attacks and convincing other teams to go into that business. Paying starts the next attacks.
- Those behind ransomware are not poor, single parents trying this as a last resort for feeding their kids. There are many people with different skills involved, teaming together to feed their greed. Paying funds organized crime. And the organizations behind them.
What should I do then?
Some ransomware has bugs that allow tailor-made cleaner software to reveal the encryption key and undo the damage. But don’t count on this. First, it might take weeks for a white-hat security guy to find that bug and spend the time to write that software. This might be fine for getting back family pictures with the stepmother. However, your company will lose income and trust, and might even get out of business. Just imagine what could go wrong in critical infrastructure, for example, a nuclear power plant. Or consider what would happen at a hospital if medical information about the patients suddenly disappears.
So we need to prepare. You probably have heard about doing backups. Not any backup will be good enough; for example, backup to a USB disk is no adequate protection, and there are easier solutions than backup. To understand how and why these countermeasures work, we first need to know how and why ransomware works.
How does ransomware get on the computer?
 Similar to other malware, ransomware can get onto your desktop computer or file server using several vectors:
Similar to other malware, ransomware can get onto your desktop computer or file server using several vectors:
- By convincing a human to install some software (a Trojan horse), maybe by someone pretending to help you by being from tech support and contacting you by mail, phone, or a message on a web site.
- By having found a security hole in your hardware, operating system, or applications and then abusing that hole to automatically install the software.
What does it do then?
Swiftness is key for the success of ransomware. That does not mean it has to start immediately. Some may wait a few hours until you are not paying attention to your computer, e.g. checking when the screensaver is activated.
But then, they do their work as fast as possible. By the time you notice anything is wrong, it should have already encrypted enough vital files to have you on the hook to pay. I.e., it reads a file, encrypts the data to a new file, and then deletes the original, possibly wiping it as well.
To ensure they are not being interrupted, some ransomware even reboots into a special mode where they have full control over your computer. While this sounds scary (and it is, as any ransomware attack), it is actually also a boon: It will not be able to access files on a corporate file server. A company suddenly having all documents inaccessible is much more devastating than just losing a single person’s work.
It is noteworthy that ransomware targets user documents, not operating system files. And during our research into ransomware, we also noticed that this encrypt-a-file workflow is often done very inefficiently: Data is being read or written more than once, with no apparent goal or result. We believe this is because different components of the ransomware are written by different groups which never talk to each other, suggesting that ransomware authoring and deploying is an organized global business.
How is ransomware activity detected?
 Traditionally, ransomware detection has been done in the classic anti-virus manner: As soon as a new strand of malware has been identified, a signature for the malware or its generated files is devised and incorporated into the anti-virus database. Several hours, sometimes days, later, your antivirus software would update the database and learn about this new strand. This often was too late. We wanted to change this by first checking what ransomware must do to get its evil work done and by taking a fresh look at what can be done on the defense side.
Traditionally, ransomware detection has been done in the classic anti-virus manner: As soon as a new strand of malware has been identified, a signature for the malware or its generated files is devised and incorporated into the anti-virus database. Several hours, sometimes days, later, your antivirus software would update the database and learn about this new strand. This often was too late. We wanted to change this by first checking what ransomware must do to get its evil work done and by taking a fresh look at what can be done on the defense side.
What were your insights?
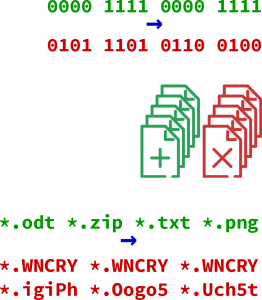 Ransomware has three main patterns:
Ransomware has three main patterns:
- One of the criteria is that a lot of files are generated and a lot of files are removed at about the same time. But this behavior may also be caused by software upgrades and many other normal activities.
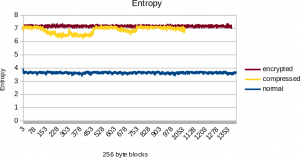
- The key is analyzing the entropy (randomness) of the file contents. Entropy is a measure for the information density and the opposite of redundancy and compressibility. Encrypting a file maximizes its entropy. Entropy also grows when compressing a file. The difference is twofold: First, encrypted content has uniform entropy with very little variations, while compressed data, images, and video shows slight variations for the entropy. Secondly, a compressed file is smaller than the original, while a file which is directly encrypted retains its size.
- Another key element of ransomware activity is that the new files have a different extension from what the file originally had. Typically, they are all the same for one particular strand of ransomware, but they could also be random new extensions. Seeing a sudden increase of previously unknown extensions is a good sign. Sometimes, they also encrypt the file names. Here again, entropy analysis is our friend.
All three measures can be immediately and most reliably detected on the computer itself, e.g., by the operating system. However, this is the very same operating system that let the malware in in the first place. So it may have already be subverted by the malware and thus might not be considered trustworthy in this respect. Therefore, we decided not to follow that route.
How to protect against ransomware, then?
A normal USB disk attached to a ransomware-infected machine could also get modified by the ransomware. So isolation is key, as Maersk has also found out.[1]Maersk had a remote location in Ghana, which—due to bad network connectivity—had not yet been infected and still contained a backup copy from before the attack.
We looked at (and dismissed) several other approaches, such as
having a modified external USB disk detect ransomware behavior. Not only is this very complicated to implement, it also completely fails when using full disk encryption, which we hope to become the standard for any disk, especially backup disks.
- Another approach, which we followed for some time, was to modify the Samba file server to include support for this. When detecting ransomware behavior, the file server would create a file system snapshot and make sure that the versions of the files before that snapshot would be available for recovery. The problems with this approach are that (a) detecting ransomware activity takes some time before being certain, and then we no longer can retroactively create a snapshot. And (b), note that existing snapshot mechanisms slow down heavily when it needs to take care of many snapshots. And (c), recovering it would be hard. So, with a heavy heart, we dismissed this option as well.
The option we decided to follow through already came with its own (1) isolation and (2) snapshotting. So we only had to make the recovery easy.
What do you do?
 We need an independent, isolated environment from the potential victim computer. And we need to go back to previous versions of overwritten or deleted files. Both, we get with many cloud storage environments. We used Nextcloud as our platform, as it is popular, it can be installed easily on small servers such as a Raspberry Pi, it is Open Source, and makes writing plugin applications easy.
We need an independent, isolated environment from the potential victim computer. And we need to go back to previous versions of overwritten or deleted files. Both, we get with many cloud storage environments. We used Nextcloud as our platform, as it is popular, it can be installed easily on small servers such as a Raspberry Pi, it is Open Source, and makes writing plugin applications easy.
We look at the following information:
- The randomness (“entropy“) of the data in uploaded files, especially how evenly distributed that randomness is inside the file. This helps distinguish an encrypted file from a compressed file or a plain file.
- The randomness of the file name extension.
- How this file is embedded into the sequence of additions, deletions, and renames of files.
 The user does not need to do anything until it notices that ransomware has been killing their files. The first thing is to do is obviously disconnect the infected machine and then remove the ransomware with dedicated software or (as is safest after any malware attack) through a re-install of the entire system.
The user does not need to do anything until it notices that ransomware has been killing their files. The first thing is to do is obviously disconnect the infected machine and then remove the ransomware with dedicated software or (as is safest after any malware attack) through a re-install of the entire system.
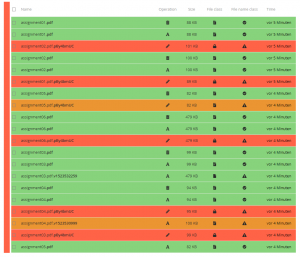
When the user activates the Ransomware recovery app, they are presented with a list of files and whether the app thinks it has been generated by the user or by ransomware. The user is the free to review this choice, if necessary.
Then, with one button press, the ransomware files are restored to the state the Nextcloud built-in Versions and Trashcan apps have stowed away. These files become then immediately become the current version in the web interface and will be synced to the computers a few seconds later.
Getting rid of the effects of ransomware effectively only requires one click!
What remains to be done?
We are very happy with the outcome so far, however, we always strive for perfection. Four things are in the making:
- First, we try to push the “undo” part to the limits: You do not even need to install the app ahead of time, you install it once you have been hit by an attack. It then uses information which is already maintained by the system to perform a post-mortem analysis. We believe this is the only way to really protect the users. Most are lazy and do not want to have to bother about this, partly also by the simple fact that the underlying technology is not per se fascinating for them, as it is for us. For example, most only start thinking seriously about backup once they have been hit by a data loss.
- Right now, the matching is not perfect. And fortunately, it does not need to be. Because the normal safety nets of trash can and per-file snapshots can be used to fix any misclassifications, be they manual or automatic, at any time. We hope that machine learning will help us improve this.
- We also need to ensure that files that are likely candidates for recovery stay put, protected both from cleanup mechanisms and from future ransomware logging into the web interface.
- It would be great to also offer this functionality for more cloud solutions and file servers.
We are always looking for help. Your are more than welcome to participate on GitHub!
See also
The software: You can install it directly from within your Nextcloud, or find more information here.
Fighting Ransomware with Guided Undo. In: Proceedings of NISK 2018, 2018.
Cost of Ransomware: Alison DeNisco Rayome, “Only 26% of US companies that paid ransomware attackers had files unlocked”, TechRepublic, 2018-03-28.
Images are licensed under CC-BY-SA 4.0 Matthias Held (images 2, 4, and 8) or Marcel Waldvogel (others).



