-
Counting like a computer

Computers are very good at counting. But usually only within narrow limits. Here is an insight into where these limits come from and what goes wrong when they are exceeded.
-
Kensington PowerPointer for Linux LibreOffice

Navigating the slides works perfectly with the Kensington PowerPointer for LibreOffice under Linux, no questions asked. The extra functions (“laserpointing”, drawing, and screen blanking) are not well supported. Here is how to fix them.
-
How to block AI crawlers with robots.txt

If you wanted your web page excluded from being crawled or indexed by search engines and other robots, robots.txt was your tool of choice, with some additional stuff like <meta name=”robots” value=”noindex” /> or <a href=”…” rel=”nofollow”> sprinkled in. It is getting more complicated with AI crawlers. Let’s have a look.
-
chrony NTS certificate reload
The chrony NTS daemon has no way to automatically reload its NTS certificate. A quick hack fixes this.
-
Data lifecycle questions, not only for Blockchains
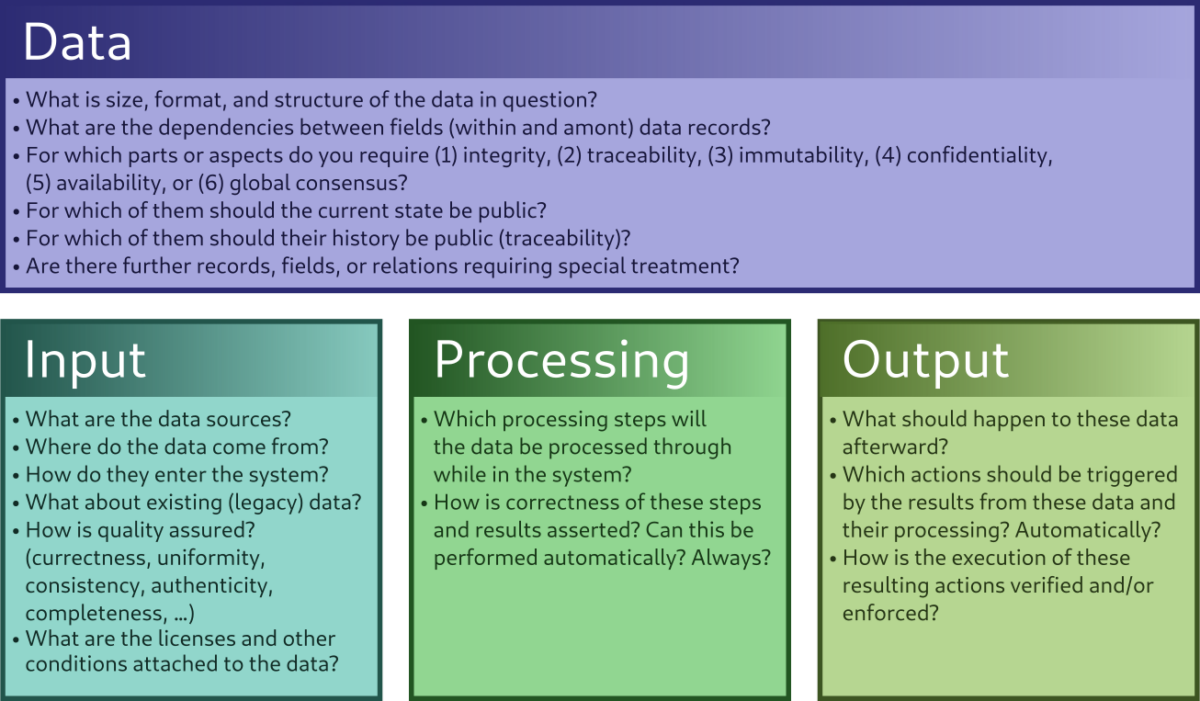
In any data-centric applications, understanding the data lifecycle (also as part of the product lifecycle) is important, especially when trust or traceability are also goals. If Blockchain should play a role, then the requirements associated with the data lifecycle can even become a decisive factor: Either adapt the data model or the processes, or, if…
-
Network Time Security: NTS articles overview
NTP, the Network Time Protocol, is the way most computers and mobile devices obtain their time through. NTS (Network Time Security) is to NTP what HTTPS is to HTTP. It also is as easy to upgrade as upgrading to HTTPS is these days: No effort for the client, just adding a certificate for the server.…
-
Debugging NTS problems
Debugging is hard, debugging security protocols doubly so. And there are not many tools and how-to’s availabe for NTS yet. So, here’s a (short) list of NTS problems I have seen and some tricks for debugging them.
-
NTS and dynamic IP addresses
Good news is that NTS relies on DNS names, no longer “naked” IP addresses. But what happens when the DNS name changes, pointing to a different IP address? A look at the protocol, the Chrony source, and the implications.
-
Configuring an NTS-capable NTP server

The choice of Network Time Protocol (NTP) servers supporting NTS is still very limited. Here is some advice to get it to run smooth and trustworty.
