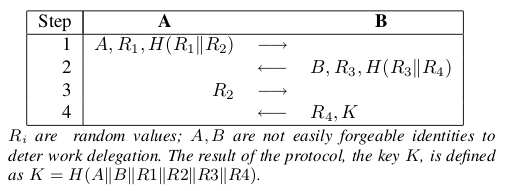
-
Stealth DoS
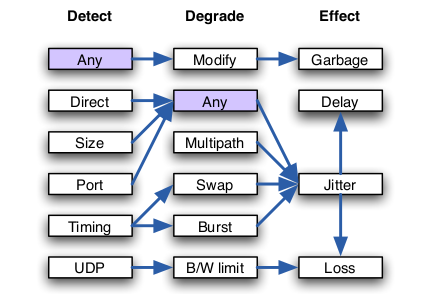
-
Pushing XPath Accelerator to its Limits
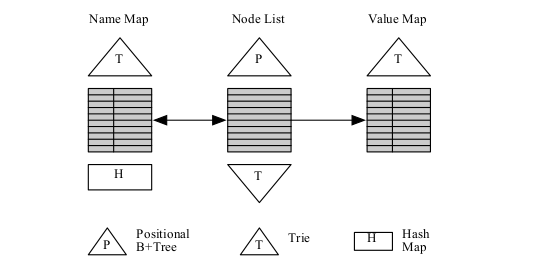
-
Bringing Efficient Advanced Queries to Distributed Hash Tables
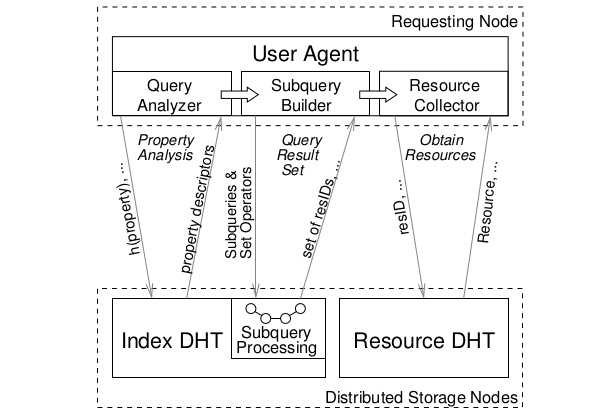
-
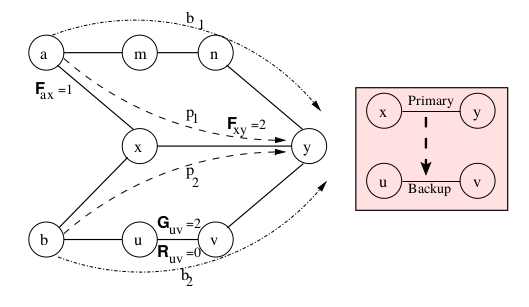
Routing Bandwidth Guaranteed Paths with Restoration in Label Switched Networks
-
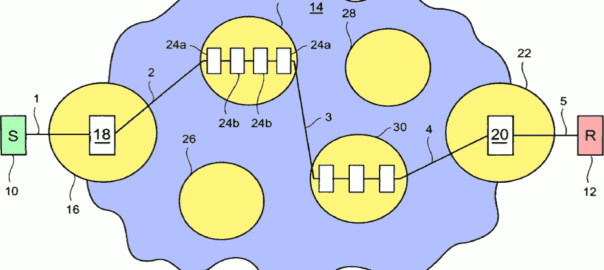
Identifying a Distributed Denial of Service (DDoS) attack within a network and defending against such an attack
-
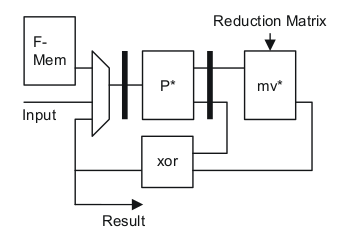
Fast and Flexible CRC Calculation
-
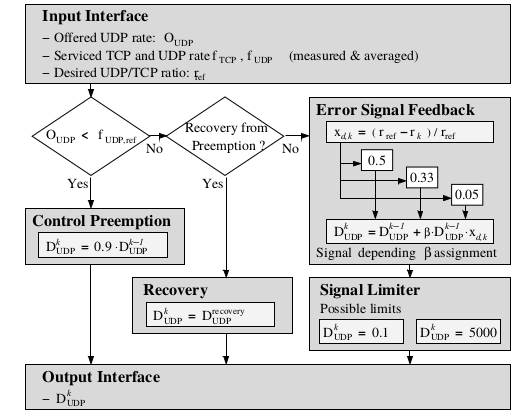
Closed-Loop Congestion Control for Mixed Responsive and Non-Responsive Traffic
-
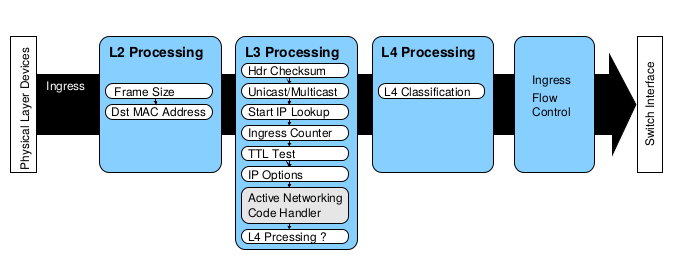
The Role of Network Processors in Active Networks
-
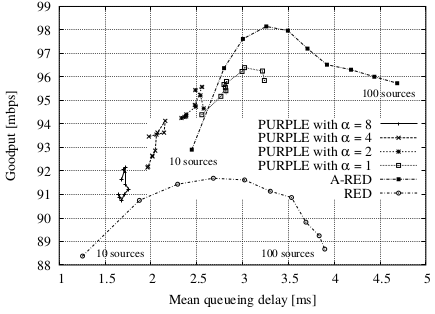
PURPLE: Predictive Active Queue Management Utilizing Congestion Information
-
Establishing Trust in Distributed Storage Providers