-
50 years of microprocessor trend data
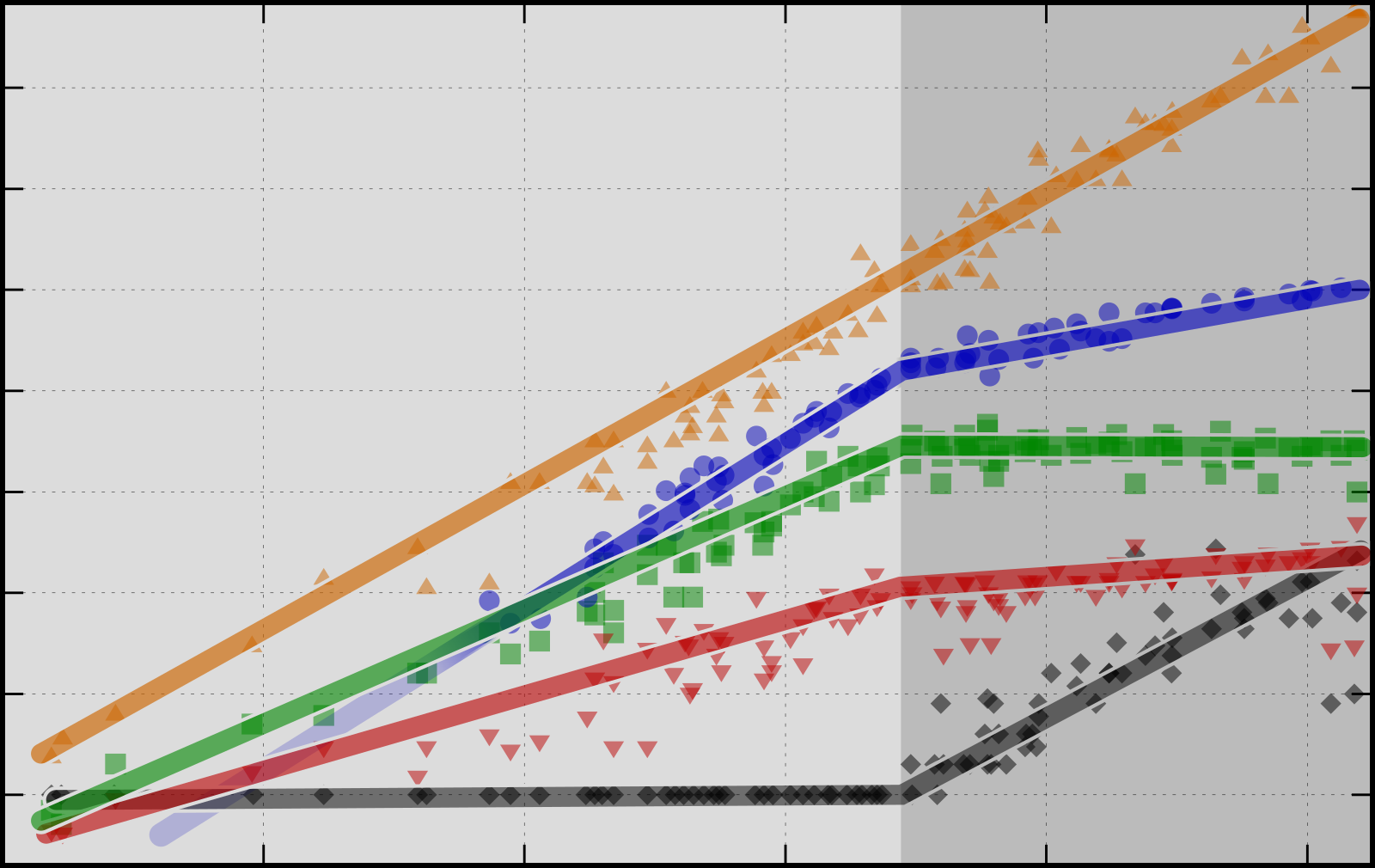
I recently wrote a (German) article including this graphic (in German). Here is an English version of it. Have fun!
-
Counting like a computer

Computers are very good at counting. But usually only within narrow limits. Here is an insight into where these limits come from and what goes wrong when they are exceeded.
-
The year in review

This is the time to catch up on what you missed during the year. For some, it is meeting the family. For others, doing snowsports. For even others, it is cuddling up and reading. This is an article for the latter.
-
Post Quantum and Homomorphic Encryption made easy
Major challenges in computer and information security are the advent of quantum computers and the need to trust your data to (cloud) service providers. New cryptography is supposed to help, but they look daunting. At their core, however, they are just children’s riddles. An introduction to Lattice cryptography and Learning With Errors.
-
Web3 is just expensive P2P
Web3 claims to be the only way to save us from commercial entities defining what we can see and what not. Yet, it does exactly this: It results in commercialized entities defining what we can see and what not.
-
Telephony of Everything: From IoT to ToE

We all know about the Internet of Things. Cool or useless gadgets, which are each controlled by their individual app on our smartphone. This is often very convenient, but not always.
-
Ransomware is different

While most types of malware such as viruses and botnets try to lay low for as long as they can, while doing their nasty work, ransomware is eager to do its work ASAP. Because of this, ransomware does not need to embed itself as deeply into the system. All it wants to do is to…


