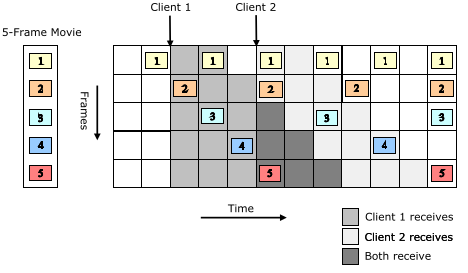
-
A Comparative Analysis of NAT Hole Punching
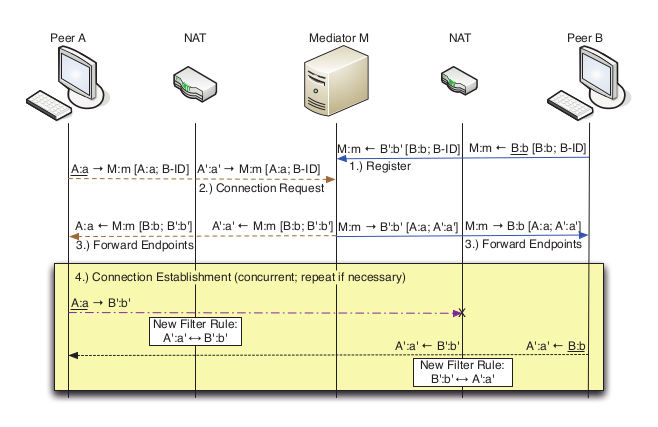
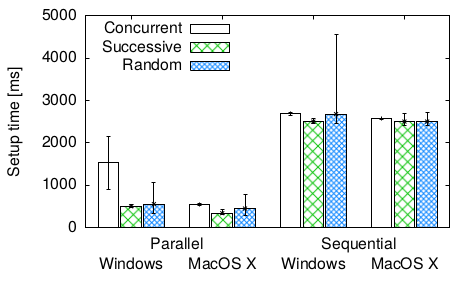
-
NAT Hole Punching Revisited
-
Analysis and Efficient Classification of P2P File Sharing Traffic
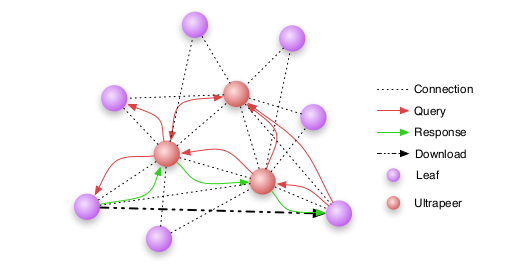
-
Replica Placement and Location using Distributed Hash Tables
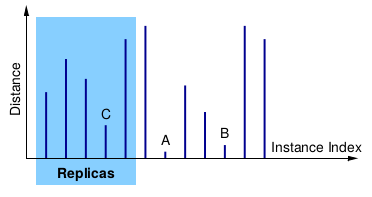
-
Bringing Efficient Advanced Queries to Distributed Hash Tables
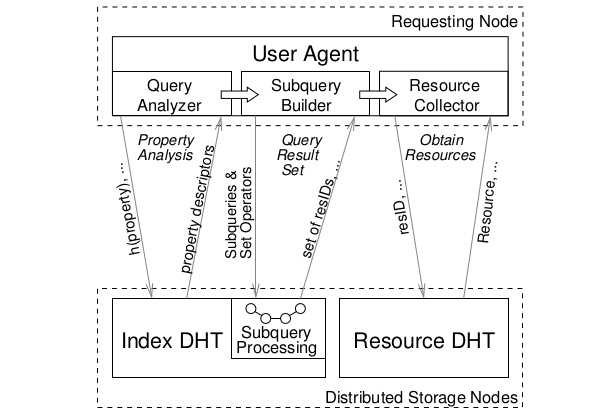
-
Establishing Trust in Distributed Storage Providers
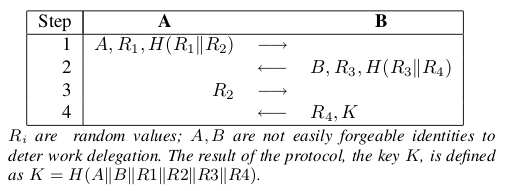
-
Dynamic Replica Management in Distributed Hash Tables
-
Indra: A Peer-to-Peer Approach to Network Intrusion Detection and Prevention
-
Efficient Topology-Aware Overlay Network