-
A SIP library is born

Inspired by Andrijan Möcker’s “Überallklingel” (Everywhere Bell), I decided to create my own. However, I wanted to use it with a motion sensor and therefore to be able to turn it off and on again, when necessary. I also felt that using Asterisk was overkill and it could be done quickly and much easier with…
-
Telephony of Everything: From IoT to ToE

We all know about the Internet of Things. Cool or useless gadgets, which are each controlled by their individual app on our smartphone. This is often very convenient, but not always.
-
Ransomware is different

While most types of malware such as viruses and botnets try to lay low for as long as they can, while doing their nasty work, ransomware is eager to do its work ASAP. Because of this, ransomware does not need to embed itself as deeply into the system. All it wants to do is to…
-
Modern ejabberd configuration

ejabberd is one of the most widely used XMPP servers. It is easy to get it running for text-based messaging with a few configuration changes. However, to obtain a smoothly running modern feature set is harder. The configuration documentation is detailed, but even for a seasoned systems administrator or XMPP guru, a lot of questions…
-
DNSSEC: Beware during algorithm transitions
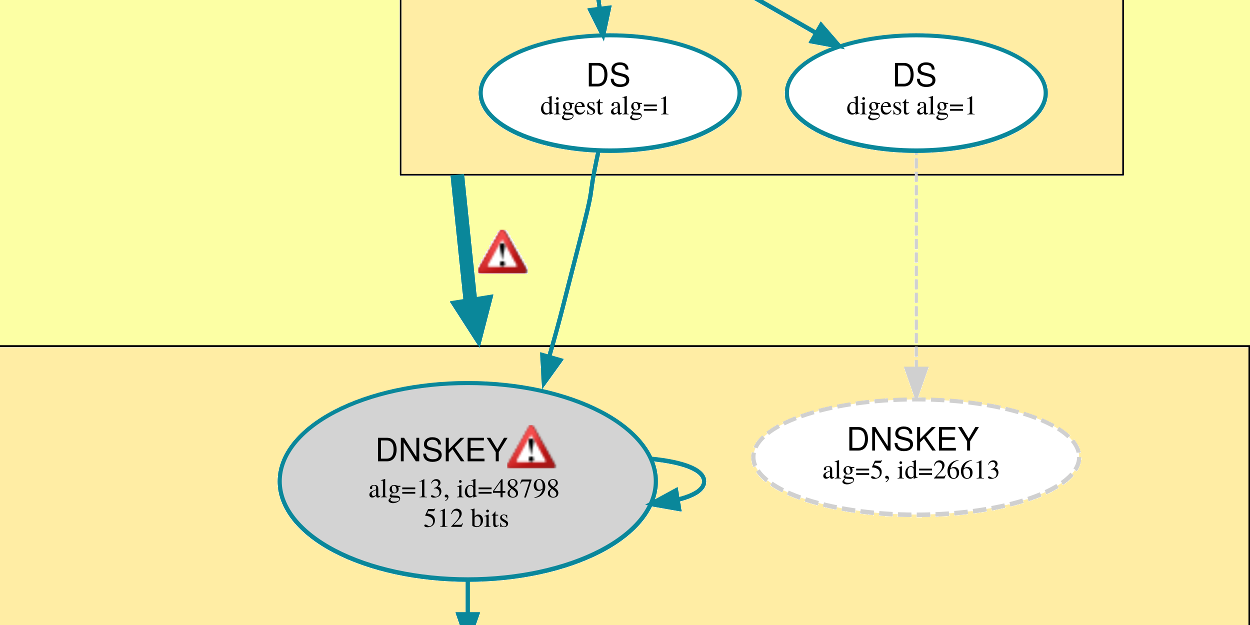
DNSSEC is cool. It easily adds security to probably the most important enabling protocol in today’s Internet: No web pages could be found, email delivered, or instant message received, without the Domain Name System (DNS). DNSSEC also enables DANE, a step forward for certificates for most applications. Sometimes you want to change a few settings.…
-
DNSSEC made easy: Converting an existing DNS zone to Inline signing with BIND

DNSSEC — the security extensions to the trusty Domain Name System (DNS) upon which almost all Internet transactions rely — is often considered hard to set up. My own setup has been very dated, using complicated scripts which needed to run after every change to the zone file. There was time to change this. Modern…
-
DDoS: What we can do to prevent it

Distributed Denial of Service, DDoS for short, is the shooting star in today’s Internet nightmare gallery. Here is a quick overview over what each and everyone of us can do to prevent his. And some hints at manufacturers and researchers.