-
SMTP Smuggling Status

«SMTP Smuggling» is a vulnerability that allows to circumvent some mail checks at the receiver and therefore will allow additional spam and/or phishing messages through. Here is the list of what we currently know.
-
The year in review

This is the time to catch up on what you missed during the year. For some, it is meeting the family. For others, doing snowsports. For even others, it is cuddling up and reading. This is an article for the latter.
-
Kensington PowerPointer for Linux LibreOffice

Navigating the slides works perfectly with the Kensington PowerPointer for LibreOffice under Linux, no questions asked. The extra functions (“laserpointing”, drawing, and screen blanking) are not well supported. Here is how to fix them.
-
NFTs are unethical

As an avid reader, you know my arguments that neither NFT nor smart contracts live up to their promises, and that the blockchain underneath is also more fragile and has a worse cost-benefit ratio than most believe. Similarly, I also claim the same for the metaverses built on top of them all. And that the…
-
Inefficiency is bliss (sometimes)

Bureaucracy and inefficiency are frowned upon, often rightly so. But they also have their good sides: Properly applied, they ensure reliability and legal certainty. Blockchain disciples want to “improve” bureaucracy-ridden processes, but achieve the opposite. Two examples:
-
How to block AI crawlers with robots.txt

If you wanted your web page excluded from being crawled or indexed by search engines and other robots, robots.txt was your tool of choice, with some additional stuff like <meta name=”robots” value=”noindex” /> or <a href=”…” rel=”nofollow”> sprinkled in. It is getting more complicated with AI crawlers. Let’s have a look.
-
«Right to be Forgotten» void with AI?

In a recent discussion, it became apparent that «unlearning» is not something machine learning models can easily do. So what does this mean to laws like the EU «Right to be Forgotten»?
-
Post Quantum and Homomorphic Encryption made easy
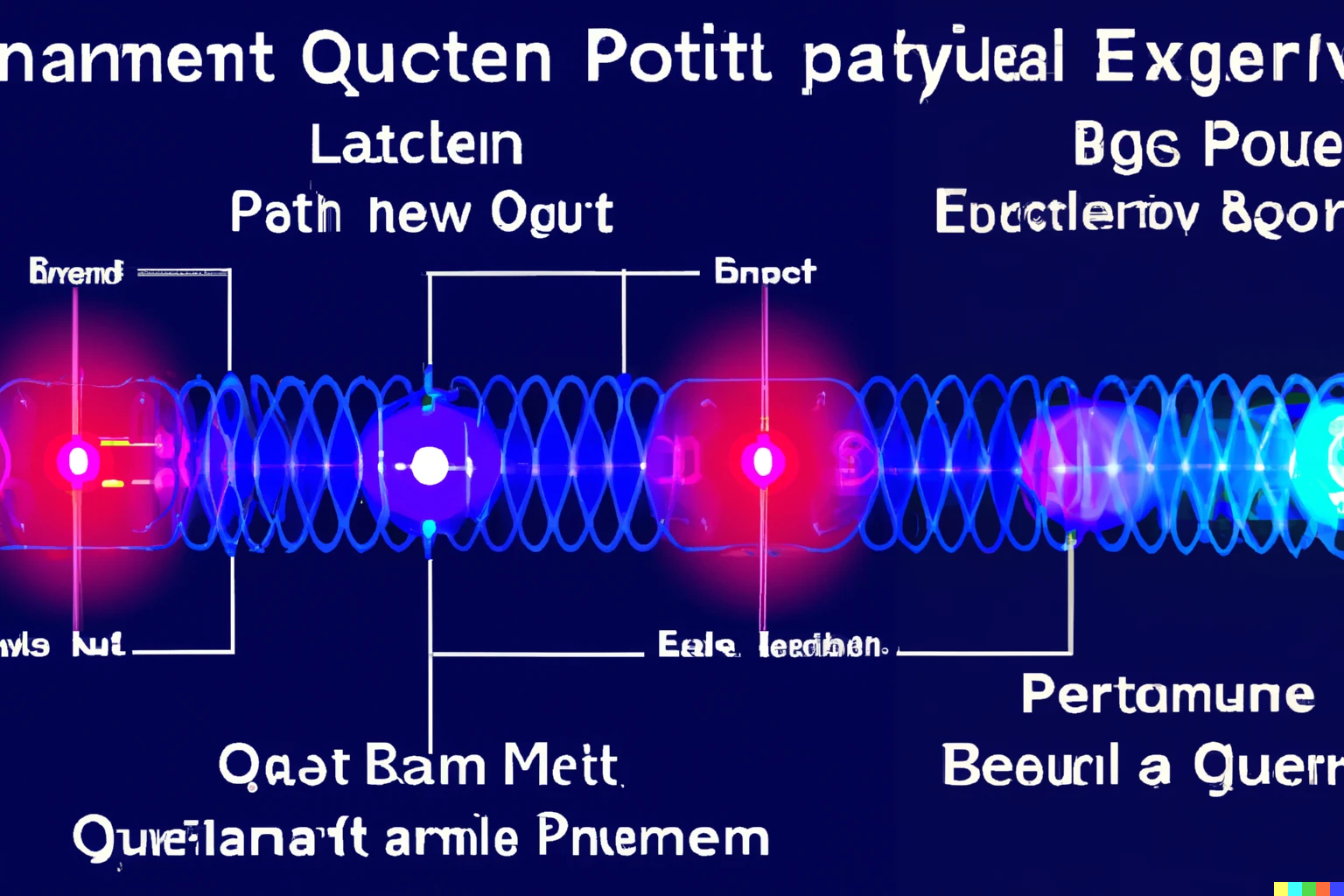
Major challenges in computer and information security are the advent of quantum computers and the need to trust your data to (cloud) service providers. New cryptography is supposed to help, but they look daunting. At their core, however, they are just children’s riddles. An introduction to Lattice cryptography and Learning With Errors.
-
How does ChatGPT work, actually?
ChatGPT is arguably the most powerful artificial intelligence language model currently available. We take a behind-the-scenes look at how the “large language model” GPT-3 and ChatGPT, which is based on it, work.
-
Identifying AI art

AI art is on the rise, both in terms of quality and quantity. It (unfortunately) lies in human nature to market some of that as genuine art. Here are some signs that can help identifying AI art.
