ejabberd is a very fine XMPP server. However, it has very few options to configure its SSL and TLS security settings away from the very weak OpenSSL defaults. The TLS Interposer makes securing TLS used by ejabberd a breeze.
[simple_series title=”TLS Interposer articles”]
Installation
If you have not installed TLS Interposer yet, please do so now using the TLS Interposer installation instructions.
TLS Interposer Configuration
The following description is for ejabberd 2.1.10 on Ubuntu 12.04 LTS; other Linux-based versions and installations should be easy to adapt.
The tail end of /usr/sbin/ejabberd should look as follows:
umask 027
exec $ERL $SNAME $ERLANG_NODE …
Directly before the exec line, add the following two lines (each starts with export, if your browser wraps them, just undo the additional wrapping):
export LD_PRELOAD=/usr/local/lib/libtlsinterposer.so
export TLS_INTERPOSER_CIPHERS='EECDH+ECDSA+AESGCM:EECDH+aRSA+AESGCM:EECDH+ECDSA+SHA384:EECDH+ECDSA+SHA256:EECDH+aRSA+SHA384:EECDH+aRSA+SHA256:EECDH+aRSA+RC4:EECDH:EDH+aRSA:RC4:!aNULL:!eNULL:!LOW:!3DES:!MD5:!EXP:!PSK:!SRP:!DSS'
The first line activates TLS Interposer; the second line adds support for RC4 (it is the default cipher set without the trailing “:!RC4”), which is needed for Jitsi.
Update 2014-04-07: You can also put these lines into /etc/default/ejabberd (on Ubuntu and other Debian-based systems, will make updates easier) or /usr/sbin/ejabberdctl (for CentOS).
Update 2014-06-05: You can also put the lines at the beginning (line 2) of /usr/sbin/ejabberdctl (e.g. in CentOS). This should not change functionality but might slow down the system startup by a few milliseconds. Also changed the library name to fit the new name the Makefile on github creates.
Other Configuration
The following parameters might already be set, but let’s double-check. Of course, you first need a key and certificate file.
In /etc/ejabberd/ejabberd.cfg, you should also have the following settings in the listen section:
{5222, ejabberd_c2s, [
{access, c2s},
{shaper, c2s_shaper},
{max_stanza_size, 65536},
%%zlib,
starttls_required, {certfile, "/etc/ejabberd/ejabberd.pem"}
]},
This ensures all clients need to connect via STARTTLS, passwords and messages can only be passed in encrypted form. Further down, outside the listen section, you should also have:
{s2s_use_starttls, true}.
{s2s_certfile, "/etc/ejabberd/ejabberd.pem"}.
For server-to-server communication, STARTTLS currently needs to remain optional. An unscientific study shows about 1/3 of the other servers cannot use STARTTLS, among them Google. For most uses, s2s communication thus cannot be forced to use TLS. If you want at least some privacy for s2s communication, your users have to use OTR.
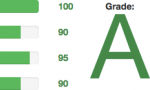
Now, you too should get an A ranking on xmpp.net. It should look similar to mine [Service discontinued].



9 responses to “Upgrade ejabberd to the latest TLS security [UPDATE#2, 2014-06-05]”
Hi, I use ejabberd 2.1.13 on CentOS and I can’t reproduce your tutorial, can you please give me a hand of help?
my jabber is serghei@jabber.ru
please add me and let me know how to secure my xmpp server, I will appreciate a lot your effort and I can even pay you if is necessary.
ps, for moment I use jabber.ru because my own server isn’t secured enough.
Frank,
thank you for the interest. As I do not have a CentOS installation right now, I’ll get in touch with you to identify the problem and report the result here for the community.
Hi Marcel,
I have centos 6.5 and am also having issues. I have installed TLS Interposer. However, the lines where you need to add code do not exist in /usr/sbin/ejabberdctl (umask 027 & exec $ERL $SNAME $ERLANG_NODE)
Running ejabberd 2.1.13
Thanks
I am aware of the problem with CentOS and ejabberd. I hope to be able to look at it in the near future and will let you know about the results (and hopefully a fix).
A new version is on github, which does not rely on the libssl.so.1.0.0 filename (which is different in CentOS). The current version may map two versions of the SSL library into memory, but it seems cleaner than to determine and hardcode the SSL version number at compile time.
Could you check /usr/sbin/ejabberdctl on CentOS as umask 027 doesn’t exist in this file, so not sure where to add export LD_PRELOAD=/usr/local/lib/tlsinterposer.so
The version of TLS Interposer builds.
I don’t have access to a working ejabberd on CentOS. Near the end of the file should be a line that contains
exec $ERL…. Insert it before this line.If there is no particular line which is suitable, you can also add it as the second line of the file. This might slow down the startup by a few milliseconds but should make no difference otherwise.
Thanks for the update. I have it working.
There are some build errors on CentOS, but it does work. Error during make install:
make install
mkdir -p /usr/local/lib
install -p -m755 libtlsinterposer.so /usr/local/lib/libtlsinterposer.so.1.1.0
ln -s libtlsinterposer.so.1.1.0 /usr/local/lib/libtlsinterposer.so.1
ln: creating symbolic link `/usr/local/lib/libtlsinterposer.so.1′: File exists
make: *** [install] Error 1
Thanks for you efforts.
On Ubuntu with ejabberd 2.1.10 I needed to add export LD_PRELOAD to the end of /etc/default/ejabberd rather than /usr/sbin/ejabberd to get ejabberd to preload tlsinterposer.so
But it works! 🙂