Links
Abstract
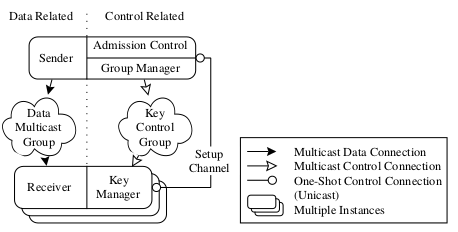
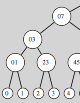
Proposals for multicast security that have been published so far are complex, often require trust in network components or are inefficient. In this paper we propose a series of novel approaches for achieving scalable security in IP multicast, providing privacy and authentication on a group-wide basis. They can be employed to efficiently secure multi-party applications where members of highly dynamic groups of arbitrary size may participate. Supporting dynamic groups implies that newly joining members must not be able to understand past group communications, and that leaving members may not follow future communications. Key changes are required for all group members when a leave or join occurs, which poses a problem if groups are large. The algorithms presented here require no trust in third parties, support either centralized or fully distributed management of keying material, and have low complexity (O(log N) or less). This grants scalability even for large groups.
BibTeX (Download)
@inproceedings{Caronni1998Efficient,
title = {Efficient Security for Large and Dynamic Multicast Groups},
author = {Germano Caronni and Marcel Waldvogel and Dan Sun and Bernhard Plattner},
url = {https://netfuture.ch/wp-content/uploads/1998/caronni98efficient.pdf},
year = {1998},
date = {1998-06-01},
urldate = {1000-01-01},
booktitle = {Proceedings of the IEEE 7th International Workshop on Enabling Technologies: Infrastructure for Collaborative Enterprises (WET ICE '98)},
address = {Palo Alto, CA, USA},
abstract = { Proposals for multicast security that have been published so far are complex, often require trust in network components or are inefficient. In this paper we propose a series of novel approaches for achieving scalable security in IP multicast, providing privacy and authentication on a group-wide basis. They can be employed to efficiently secure multi-party applications where members of highly dynamic groups of arbitrary size may participate. Supporting dynamic groups implies that newly joining members must not be able to understand past group communications, and that leaving members may not follow future communications. Key changes are required for all group members when a leave or join occurs, which poses a problem if groups are large. The algorithms presented here require no trust in third parties, support either centralized or fully distributed management of keying material, and have low complexity (O(log N) or less). This grants scalability even for large groups. },
keywords = {Multicast, Security},
pubstate = {published},
tppubtype = {inproceedings}
}