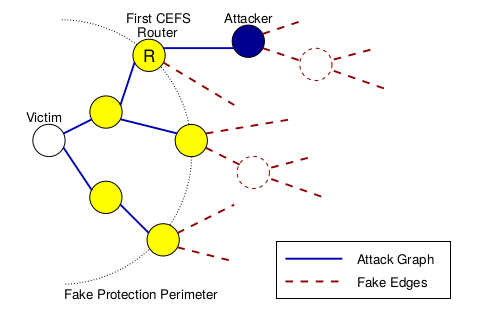
-
Versatile Key Management for Secure Cloud Storage
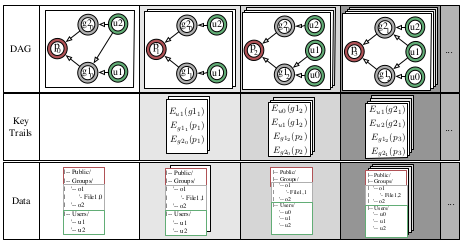
-
BitTorrent traffic obfuscation: A chase towards semantic traffic identification
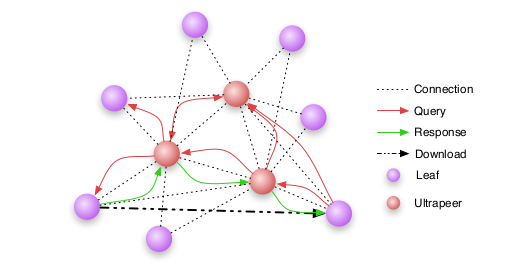
-
A Legal and Technical Perspective on Secure Cloud Storage
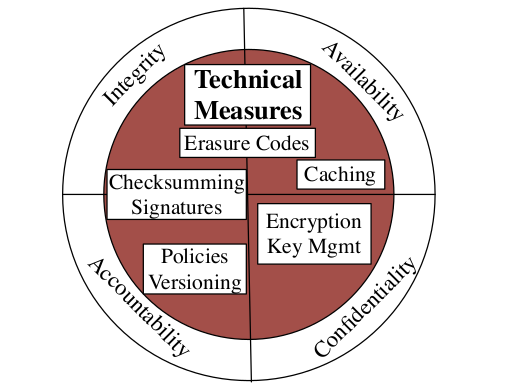
-
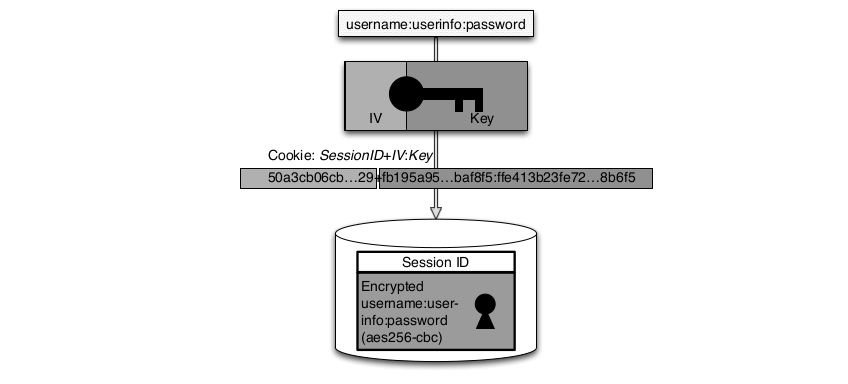
Polybius: Secure Web Single-Sign-On for Legacy Applications
-
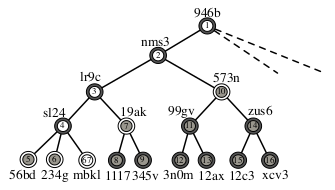
Integrity Assurance for RESTful XML
-
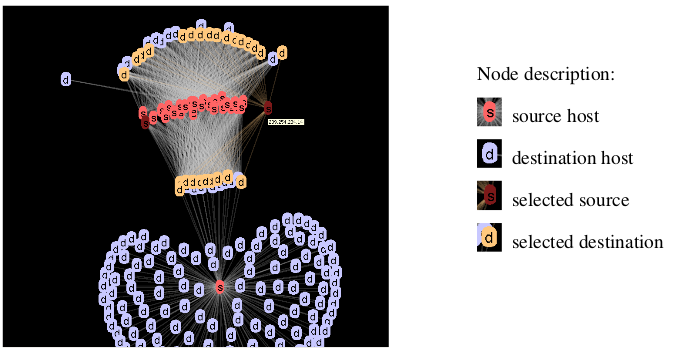
Interactive Analysis of NetFlows for Misuse Detection in Large IP Networks
-
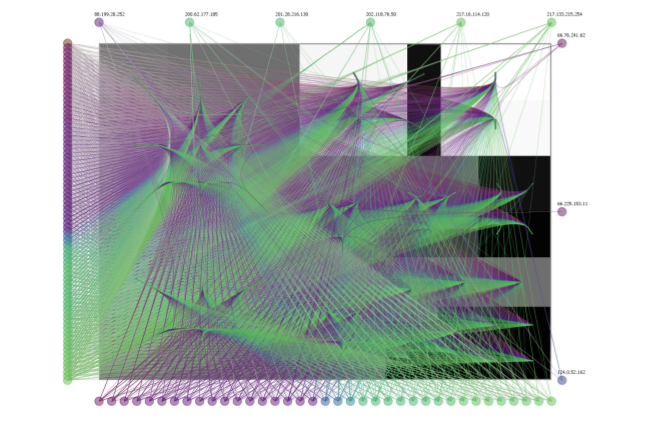
Large-scale Network Monitoring for Visual Analysis of Attacks
-
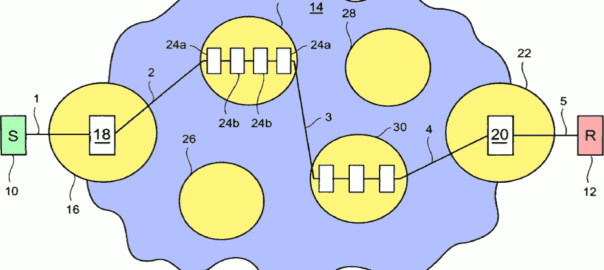
Identifying a Distributed Denial of Service (DDoS) attack within a network and defending against such an attack
-
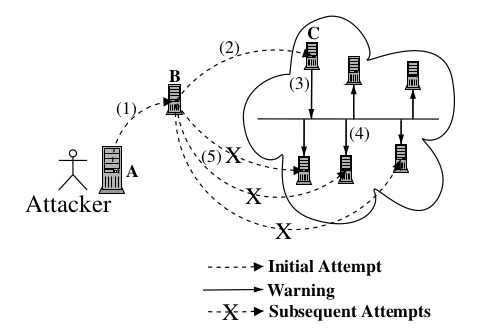
Indra: A Peer-to-Peer Approach to Network Intrusion Detection and Prevention
-
GOSSIB vs. IP Traceback Rumors