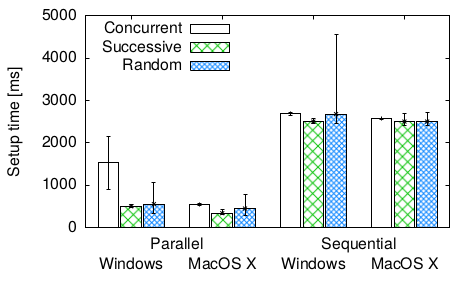
-
BitTorrent traffic obfuscation: A chase towards semantic traffic identification
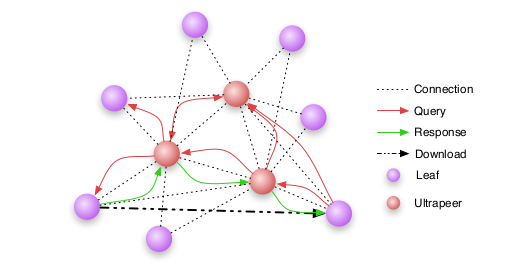
-
P2P-RMI: Transparent Distribution of Remote Java Objects
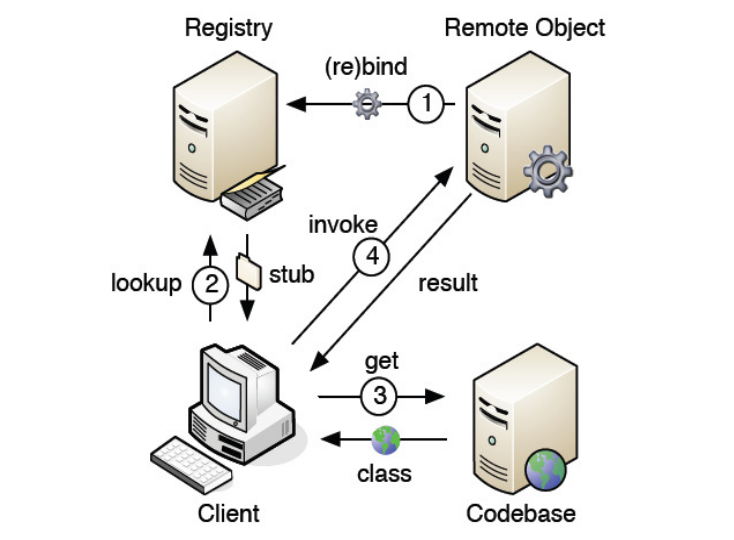
-
Analyzing History Quality for Routing Purposes in Opportunistic Network Using Max-Flow
-
A Legal and Technical Perspective on Secure Cloud Storage
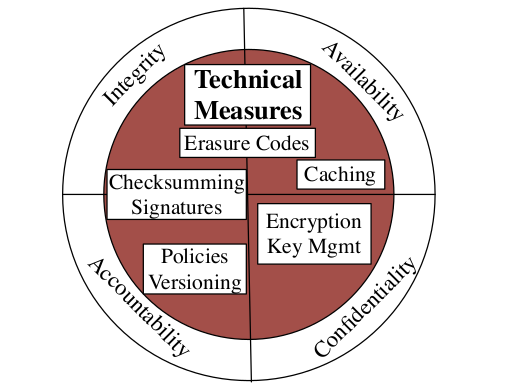
-
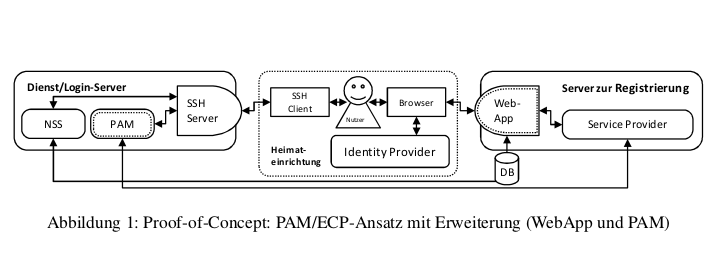
bwIDM: Föderieren auch nicht-webbasierter Dienste auf Basis von SAML
-
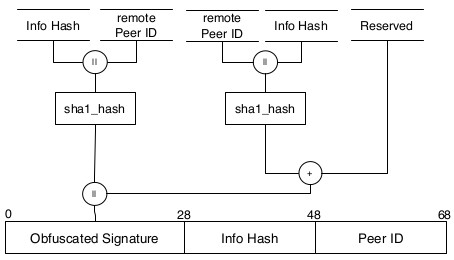
Efficient BitTorrent handshake obfuscation
-
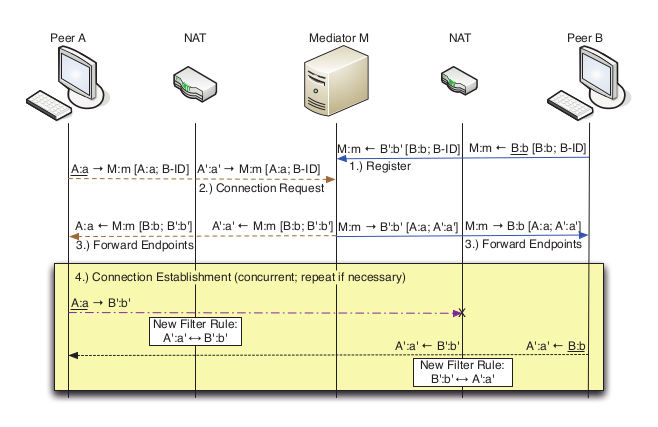
A Comparative Analysis of NAT Hole Punching
-
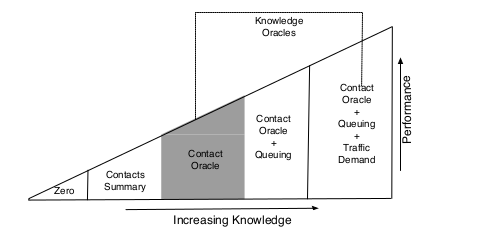
Prediction quality of contact history in opportunistic networks
-
Prediction Quality of Contact History in Opportunistic Networks
-
NAT Hole Punching Revisited