Abstract
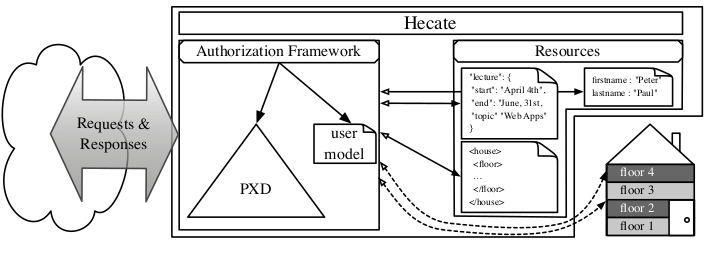
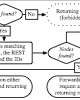
The potentials of REST offers new ways for communications between louse coupled entities featured through the Web of Things. The binding of the disjunct components of this architecture creates security issues, such as the centralized authorization techniques respecting the independence of the underlying entities. This results in the question how authorization is performed respecting the flexibility of REST without any knowledge about the underlying resources. Nevertheless, possible knowledge about these resources should enable the authorization workflow to offer finer-granular permissions on substructures of the resources. With our new approach – named Hecate – we offer a framework to assure simplified handling while keeping the potentials and flexibility of REST. We have designed an architecture based on XML with a flexible authorization mechanism on the one hand and optional resource-awareness on the other hand. The flexibility within the authorization work-flow bases on permission sets respecting the HTTP verbs. Additional in-depth knowledge of the entity optionally extends these permissions with resource-aware filters. Hecate offers not only great benefits because of its flexibility, but also because of the optional extensibility proved within the two reference implementations. With Hecate, we show that a centralized authorization mechanism combining independence and optional resource-based filtering extends the flexibility of REST rather than restricting it.
BibTeX (Download)
@inproceedings{Graf2011Hecate,
title = {Hecate: Managing Authorization with RESTful XML},
author = {Sebastian Graf and Vyacheslav Zholudev and Lukas Lewandowski and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2011/graf11hecate.pdf},
year = {2011},
date = {2011-03-28},
urldate = {1000-01-01},
booktitle = {Proceedings of WS-REST 2011},
abstract = {The potentials of REST offers new ways for communications between louse coupled entities featured through the Web of Things. The binding of the disjunct components of this architecture creates security issues, such as the centralized authorization techniques respecting the independence of the underlying entities. This results in the question how authorization is performed respecting the flexibility of REST without any knowledge about the underlying resources. Nevertheless, possible knowledge about these resources should enable the authorization workflow to offer finer-granular permissions on substructures of the resources. With our new approach - named Hecate - we offer a framework to assure simplified handling while keeping the potentials and flexibility of REST. We have designed an architecture based on XML with a flexible authorization mechanism on the one hand and optional resource-awareness on the other hand. The flexibility within the authorization work-flow bases on permission sets respecting the HTTP verbs. Additional in-depth knowledge of the entity optionally extends these permissions with resource-aware filters. Hecate offers not only great benefits because of its flexibility, but also because of the optional extensibility proved within the two reference implementations. With Hecate, we show that a centralized authorization mechanism combining independence and optional resource-based filtering extends the flexibility of REST rather than restricting it.},
keywords = {Identity Management, Security, XML},
pubstate = {published},
tppubtype = {inproceedings}
}