Links
Abstract
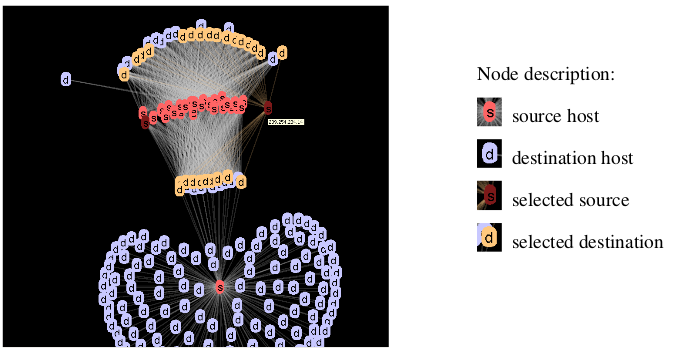
While more and more applications require higher network bandwidth, there is also a tendency that large portions of this bandwidth are misused for dubious purposes, such as unauthorized VoIP, file sharing, or criminal botnet activity. Automatie intrusion detection methods can detcct a large portion of such misuse, but novel patterns can only be detected by humans. Moreover, interpretation of large amounts of alerts imposes new challenges on the analysts. The goal of this paper is to preseot the visual analysis system NFlowVis to interactively detcct unwanted usage of the network infrastructure either by pivoting NetFlows using IOS alerts or by specifying usage patterns, such as sets of suspicious port numbers. Thereby, our work focuses on providing a scalable approach to store and retrieve large quantities of Netflows by means of a database management system.
BibTeX (Download)
@inproceedings{Mansmann2009Interactive,
title = {Interactive Analysis of NetFlows for Misuse Detection in Large IP Networks},
author = {Florian Mansmann and Fabian Fischer and Daniel A. Keim and Stephan Pietzko and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2009/mansmann09interactive.pdf},
year = {2009},
date = {2009-05-01},
urldate = {1000-01-01},
booktitle = {DFN-Forum Kommunikationstechnologie},
address = {Garching (Munich), Germany},
abstract = {While more and more applications require higher network bandwidth, there is also a tendency that large portions of this bandwidth are misused for dubious purposes, such as unauthorized VoIP, file sharing, or criminal botnet activity. Automatie intrusion detection methods can detcct a large portion of such misuse, but novel patterns can only be detected by humans. Moreover, interpretation of large amounts of alerts imposes new challenges on the analysts. The goal of this paper is to preseot the visual analysis system NFlowVis to interactively detcct unwanted usage of the network infrastructure either by pivoting NetFlows using IOS alerts or by specifying usage patterns, such as sets of suspicious port numbers. Thereby, our work focuses on providing a scalable approach to store and retrieve large quantities of Netflows by means of a database management system.},
keywords = {Intrusion Detection, Security},
pubstate = {published},
tppubtype = {inproceedings}
}