-
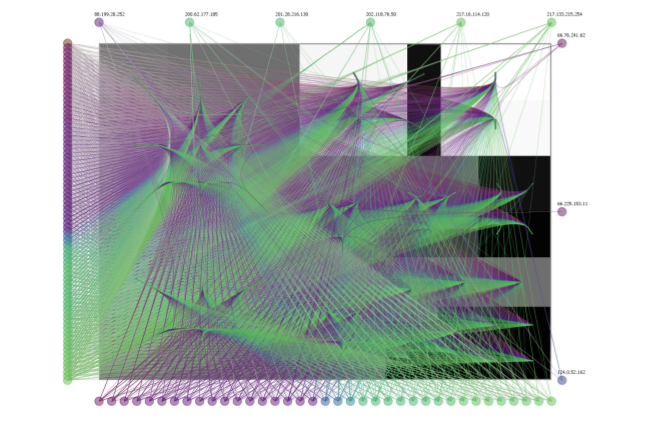
Large-scale Network Monitoring for Visual Analysis of Attacks
-
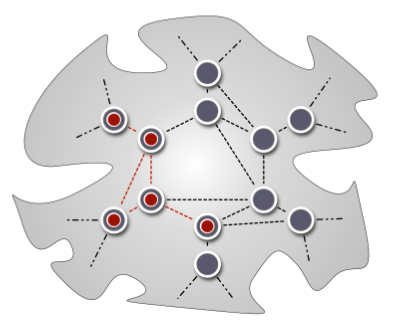
Reality-Check for DTN Routing Algorithms
-
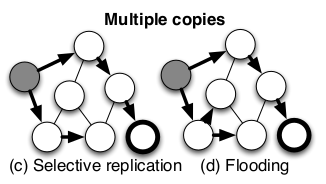
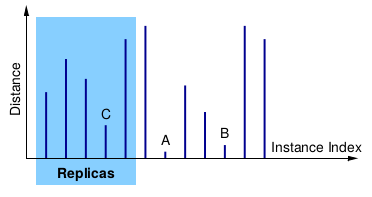
Replica Placement and Location using Distributed Hash Tables
-
Replica Placement and Location using Distributed Hash Tables
-
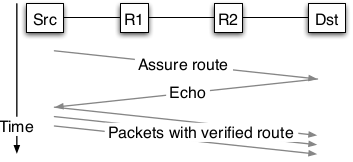
Light-weight End-to-End QoS as DoS Prevention
-
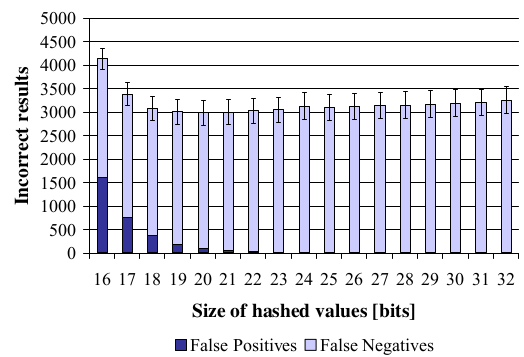
Bloom Filters: One Size Fits All?
-
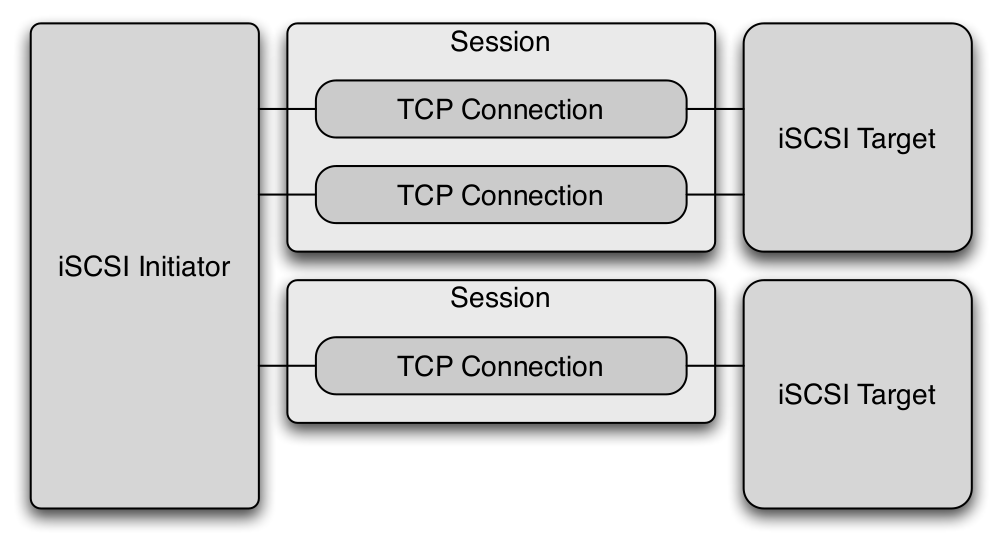
jSCSI – A Java iSCSI Initiator
-
Interactive Poster: Exploring Block Access Patterns of Native XML Storage
-
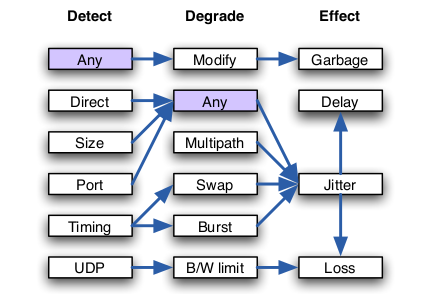
Stealth DoS