How much we are all looking forward to returning to normal lives: Meeting friends, hugging family, a cool beer, culture. After more than a year, we really deserve it! However, there are still roadblocks in the form of a bloody virus and the countermeasures. Anyone promising a quick end is hailed as a saviour.
(This article originally appeared in Das Netz ist Politisch in German.)
Luca: A (bad) example
In Germany, multiple States have already spent around 20 Million Euro in taxes for the Luca app, “developed” and marketed by a famous musician. Switzerland is also on within reach.
The app promises no less than to enable us to resume to go to events and opening restaurants: Just scan a QR code on entry. In case of a potential infection, the guests will be informed. Traditionally, you would have to leave your contact details. Luca claims that you have to enter data only once and they will leave your mobile phone only securely encrypted. The data should only be recoverable through a combination of health authorities and host or guest.
The app’s makers pledge of “encrypted, secure, and responsible data transmission”, is the least we should expect. Regular use of the app discloses too many details of our lives, including participating in religious services, political meetings, self-help groups or the red-light district. Maximum privacy delivered by data protection and IT security is only appropriate.
Few musicians are experts in IT security. Singer Smudo of the successful German band Die Fantastischen Vier, figurehead of Luca, and referred as one of its developers, is no exception. Politicians–supported by Data Protection Officers–saw a possibility to score. The promoter’s notability, the easy money and Germany’s Super Election Year were a good match. The Federal Government even promised to cover the costs of the first 18 months, no questions asked. In such a situation, laws and best practices about evaluation or procurement seem moot. Luckily, some steadfast IT experts spent their free evenings and weekends on the necessary analysis.
Already last week, the result was devastating for Luca: Security professional Manuel Atug alone collected over 400 tweets on Luca problems. His collected wisdom of various IT experts was summarized as Luca being “dilettante and useless”. More questions were raised when it became known that the very same musicians pressuring unswervingly for tougher copyright laws had been caught red-handed violating the same, illegally copying source code.
The Luca owners also plan to earn more money later with ticketing-related services. User anonymity is probably the first thing that you want to get rid of when taking this route and maximizing your profits.
Without the dangerous combination of
- notable star,
- politicians desperate to grasp at any straws, and
- the sunk-cost fallacy of the already wasted millions,
any other project rightfully would have been killed immediately.
In the last few days, our unswerving experts spent their time off well, digging up problems, each of which would be a death blow on its own:
- Marcus Mengs discovered that Luca continuously tells the server where the user currently is, in a form perfect for tracking behaviour and creating personalised visitor lists. Besides these tracing IDs and IP addresses, OS version and model of the mobile device are sent every few seconds. Linking to the supposedly secret phone number also becomes possible. Together with other weaknesses of the encryption protocol used, even your supposedly secret personal data could be obtained. The app therefore does the very opposite of what it promises. It probably will always remain unclear whether this resulted from negligence or deliberation.
How can things go so fundamentally wrong?
Today, encrypting data is child’s play. However, key management, the art of ensuring that only the intended recipients can decrypt the data is rocket science. Compare this to installing locks in a large office building: Buying hundreds of tumbler locks and installing them is easy. Creating a master key plan such that everyone can only open the doors they should, without requiring everyone to carry a hundred keys with them, this is far from trivial. And don’t get me started about losing keys or cross-department collaboration.
Data ≠ metadata. Contact and location data stored on the server are encrypted (even though researchers discovered problems here as well). However, to enable the guest app of learning that the check-in has been recorded by the host, it polls the server every few seconds. Naturally, metadata are involved here. Designing the process with a minimum of expertise would have avoided leaking traitorous metadata. It seems, that nobody cared.
- If you cannot or do not want to use the app, you can buy a key fob with QR code. This fob is scanned by the host to add you to the visitor list. Bianca Kastl and Tobias Ravenstein discovered that anyone taking a snap or a scan of the QR code on the fob can immediately recover your movement over the past 30 days. The QR code not only contains the anonymous ID necessary to be added to the list, but also the secret to authorize the querying of the list of locations visited. Another key management problem.
Both findings support what was suspected due to the lack of missing design and data protection documents: The app has been hastily put together without involving anyone with thorough expertise in data protection and IT security. Lack of technical knowledge was more than compensated by excellent PR and connections.
Luca is not the only case, even though it is probably the one with the deepest chasm between the promises and reality. Many other apps designed in the past few months started out with similar goals but do not have the necessary foundation in privacy and IT security. How can we get at to robust promises?
But we desperately need a tracing app!
You probably have heard countless times that the tracing of the infection chain, known as contact tracing, is the ultimate goal. The other message that has been repeated ad nauseam is that the pandemic would long be over, if we only had scrapped privacy altogether.
We will look at these questions after taking a step back.
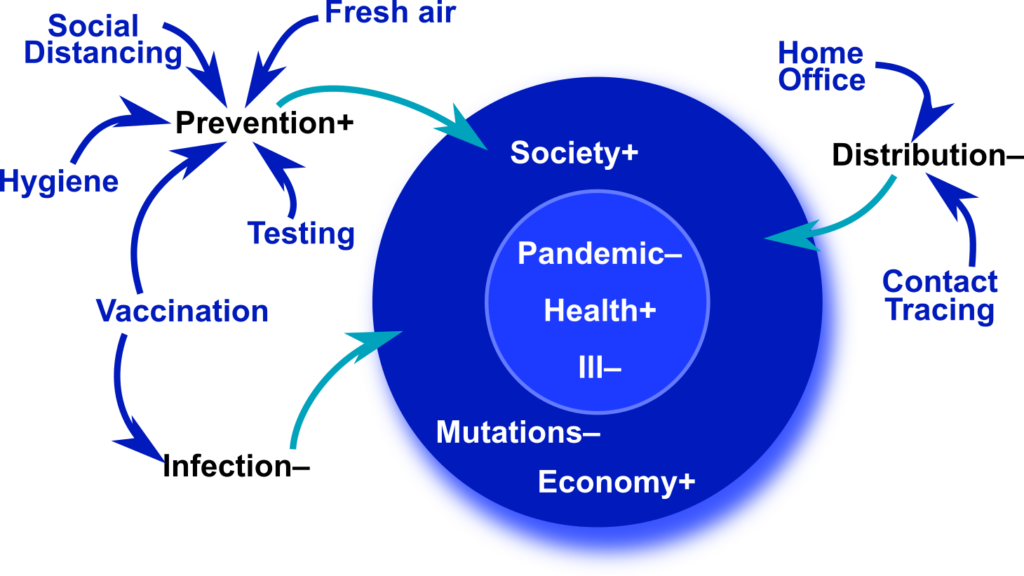
The ultimate goals are
- Guaranteeing the health of the population,
- minimizing the number of people getting sick or dying, and
- a quick end to the pandemic.
Secondary goals include:
- Reduction of the probability for new mutations
- preventing a breakdown of our healthcare system, and
- minimizing social and economic impacts (not necessarily in the short term, but in total).
Several measures are put into place to achieve this:
- Prevention of infections and reduction of their strength (vaccination)
- Reduction of the number of infections (vaccination, tests, social distancing, closures, fresh air, hygiene)
- Reduction of the speed of spreading (home office, travel reduction, contact tracing)
Be aware that contact tracing originally was created to curb very rare cases of severe illnesses, because you can never have 100% protection.
Now, we perform contact tracing because the other measures are not effective enough or they are implemented shyly out of fear of the short-term effects to economy and society. And we have not yet reached herd immunity, especially, as vaccination progresses at glacial speeds.
IT, our saviour
Contact tracing was only meant to be a small piece of the puzzle, for a handful of infections daily. However, all other measures combined are far from strong enough, so we grasp at every straw.
Also, marketing of IT startups and tech giants indoctrinated us over the past 25 years that digital transformation or an app can magically solve all our problems. If nothing else works, just conjure up an app!
We often forget that human problems (such as the readiness for social distancing, hygiene, tests, and vaccination) is never solved by technology. Technology can only play a support role when solving human problems.
Let’s step back further and build solution from there.
How does contact tracing work?
Bianca Kastl, whom we have met earlier, describes contact tracing. As an insider of the IT infrastructure in a German public health department, she provides a glimpse behind the scenes. In short: Many departments and systems are to be combined; data exchange is complicated, especially when crossing regional borders. In Switzerland, it is probably similar.
There are a lot of manual and time-consuming processes involved, requiring a lot of resources and resulting in potential infected people getting notified late. No wonder, contact tracing was never meant to be used at this scale. As a result, infection chains are not broken fast enough. To change this is the promise of these apps.
Too many apps spoil the broth
Exchanging data with existing contact tracing systems is probably the hardest part, due to lack of automated data exchange and standardized interfaces. If a person records her visits in app A, it becomes tedious at least to inform persons using apps B, C, or D about their potential infection. The fewer apps, the better, with a monopoly being the optimum. This is what is supposed to happen with Luca in Germany.
We already have an app for contact tracing: SwissCovid app (in Germany: CoronaWarnApp). It recognizes other smartphones with similar app via Bluetooth and tries to guess distance and duration of the contact. It also records the time-dependent random IDs of the peers. An infected person can publish her IDs. Anyone having been close will recognize the ID, without learning more about that person’s identity or whereabouts. Nevertheless, former contacts can be informed of the risk and take action.
Privacy-wise, this is great. And solutions with less privacy are not better.
Why another app, then?
The main means of transmission in society is through inhalation of virus-laden particles: Droplets and aerosols. With little air exchange, aerosols spread even into the furthest corner of a large room, like cigarette smoke. They can remain in the air for hours, even after their producer left.
No app can know what happens in the air. So it will not know how duration and distance correlate to the infection risk. Therefore, we need to feed the app with the information that we spent time indoors, such that transmission to and from other people in the same room can be assumed independent of distance. A QR code placed at the entrance can be used as this indication. This is the approach taken by Luca and many similar apps.
But, if Luca and friends are no good…?
Researchers at EPFL, with plenty of experience in secure and private communication and also the brains behind the DP³T technolog behind SwissCovid app, also created CrowdNotifier. From 10,000 feet, this anonymous protocol works similar to DP³T, just considering the QR code of a room as a virtual contact. An infected person or the contact tracing team informs the room owner of the time span of a potential infection. The owner then stores an encrypted message in the database, which is regularly anonymously downloaded by all the app users. Anyone who was present during the questionable time interval can decrypt the message. For anyone else, it is just gibberish and discarded. Nobody else learns about what happened.
NotifyMe is an app implementing this CrowdNotifier protocol. Unlike Luca and hundreds of other apps, the foundation behind protocol and app are solid expertise in data protection and privacy.
NotifyMe (andin the next version, CoronaWarnAppor SwissCovid app) is an application, which is founded on a solid basis of privacy protection and efficiency for recognizing potential infections in the same room.
What now?
- Contact tracing is only necessary, because we can still infect each other. It is inherently complicated and inefficient as long as infection numbers are high. But because other measures are not strong enough, it is an essential means even now.
- Many avoid the installation of apps or using tests, because they are afraid of the impact of self-isolation and quarantine. This cannot be solved technically. Employers and lawmakers are instrumental to reduce this barrier by creating unbureaucratic solutions for support and compensation.
- Luca app is highly questionable, both technically and from a privacy perspective. Also, the planned business model is alarmingly incompatible with privacy.
- The existing national Covid apps provide good base protection and help cover the holes left by the other means. CrowdNotifier, respectively NotifyMe help to anonymously provide the additional information that you were in the same closed room as an infectuous person.
The use of Luca (and several of its brethren) is highly discouraged. Well thought-out and sound apps like SwissCovid and NotifyMe are important alternatives focusing on privacy and security.