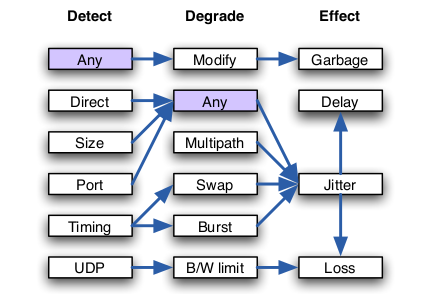
Abstract
Users and providers increasingly disagree on what Denial of Service (DoS) is. For example, an ISP might consider large multimedia downloads an attack to overload its infrastructure or have it pay high interconnection fees. On the other hand, a user will certainly consider selective bandwidth reduction that is used by ISPs as a countermea- sure, as a DoS measure. Given the nature of their business relationship, neither side is likely to openly admit that they are fighting each other. In this paper we attempt to formalise the concept of Stealth DoS, including listing mechanisms that may be used at high speed. We concentrate on mechanisms that might be used in one particular area, voice over IP (VoIP). We start evaluating them under the different aspects, including their cost, political suitability and the likelihood for countermeasures to succeed. We expect that this will give both sides better insight on their options and plea for peace, hopefully in an attempt to avoid and open war.
BibTeX (Download)
@inproceedings{Waldvogel2006Stealth,
title = {Stealth DoS},
author = {Marcel Waldvogel and Michael Muncan and Mahak Patidar},
url = {https://netfuture.ch/wp-content/uploads/2006/waldvogel06stealth.pdf},
year = {2006},
date = {2006-09-28},
urldate = {1000-01-01},
booktitle = {Proceedings of IEEEslash IST Workshop on Monitoring, Attack Detection, and Mitigation (MonAM 2006)},
abstract = {Users and providers increasingly disagree on what Denial of Service (DoS) is. For example, an ISP might consider large multimedia downloads an attack to overload its infrastructure or have it pay high interconnection fees. On the other hand, a user will certainly consider selective bandwidth reduction that is used by ISPs as a countermea- sure, as a DoS measure. Given the nature of their business relationship, neither side is likely to openly admit that they are fighting each other. In this paper we attempt to formalise the concept of Stealth DoS, including listing mechanisms that may be used at high speed. We concentrate on mechanisms that might be used in one particular area, voice over IP (VoIP). We start evaluating them under the different aspects, including their cost, political suitability and the likelihood for countermeasures to succeed. We expect that this will give both sides better insight on their options and plea for peace, hopefully in an attempt to avoid and open war.},
keywords = {Denial of Service, Security},
pubstate = {published},
tppubtype = {inproceedings}
}