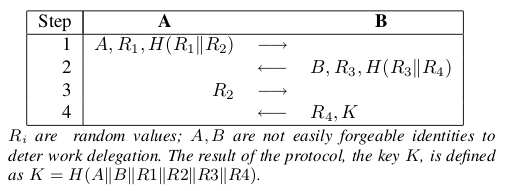
Abstract
Corporate IT as well as individuals show increasing interest in reliable outsourcing of storage infrastructure. Decentralized solutions with their resilience against partial outages are among the most attractive approaches. Irrespective of the form of the relationship, be it based on a contract or on the more flexible cooperative model, the problem of verifying whether someone promising to store one’s data actually does so remains to be solved, especially in the presence of multiple replicas. In this paper, we introduce a lightweight mechanism that allows the data originator or a dedicated verification agent to build up trust in the replica holder by means of protocols that do not require prior trust or key establishment. We show how naive versions of the protocol do not prevent cheating, and then strengthen it by adding means that make it economically attractive to be honest. This provides a foundation for further work in providing trustworthy distributed storage.
BibTeX (Download)
@inproceedings{Caronni2003Establishing,
title = {Establishing Trust in Distributed Storage Providers},
author = {Germano Caronni and Marcel Waldvogel},
url = {https://netfuture.ch/wp-content/uploads/2003/caronni03establishing.pdf},
year = {2003},
date = {2003-09-01},
urldate = {1000-01-01},
booktitle = {Proceedings of Third IEEE International Conference on Peer-to-Peer Computing (P2P 2003)},
abstract = {Corporate IT as well as individuals show increasing interest in reliable outsourcing of storage infrastructure. Decentralized solutions with their resilience against partial outages are among the most attractive approaches. Irrespective of the form of the relationship, be it based on a contract or on the more flexible cooperative model, the problem of verifying whether someone promising to store one's data actually does so remains to be solved, especially in the presence of multiple replicas. In this paper, we introduce a lightweight mechanism that allows the \textit{data originator} or a dedicated \textit{verification agent} to build up trust in the \textit{replica holder} by means of protocols that do not require prior trust or key establishment. We show how naive versions of the protocol do not prevent cheating, and then strengthen it by adding means that make it economically attractive to be honest. This provides a foundation for further work in providing trustworthy distributed storage.},
keywords = {Cloud Storage, Peer-to-Peer, Replication, Trust},
pubstate = {published},
tppubtype = {inproceedings}
}